Image via Freepik
As we celebrate another Cybersecurity Awareness Month, this year’s theme, “See yourself in Cyber,” is especially poignant for an industry that desperately needs to find new and creative ways to establish a sustainable workforce. As of last year, more than 700,000 cybersecurity jobs remained unfilled in the United States, with experts estimating that number will only rise over the next decade.
What the general population doesn’t understand about cybersecurity, and what I believe this month-long celebration should intend to explore, is that it doesn’t take a computer genius, or even a background in computer science, to embark on a successful career in the industry. Are you an art major who is looking to pivot? An accountant who loves solving puzzles? Or even a construction worker who excels in working in teams? I promise, there is room for you in cybersecurity. As more professionals look to change industries completely and follow their dreams, I want you to know that you’re not alone, and it can actually be done. I know because I did it.
As a former humanities major and video game developer, I can confidently say that I didn’t always see myself in cyber, especially in the early 2000s, when hacking — and thwarting hackers — was more common in Hollywood than on the nightly news. At that time, I was developing video games for a small studio on September 11, 2001, and the tragedy changed everything for me. I decided I wanted to make a more direct impact on my country and studied the best path to realize that goal. Soon after, I joined the U.S. Army to gain the intelligence experience necessary to serve in the Federal Bureau of Investigation (FBI) as a special agent covering mostly cybercrime, but also a bit of everything from international terrorism to gang interdictions. I even had the opportunity to serve as a SWAT team leader.
In the FBI, I was assigned to investigate cybercrime, that was my initial motivation to develop the technical skills necessary to work in cybersecurity in both the public and private sectors, but I want everyone to understand that there are other ways to enter this industry. Some cybersecurity firms offer internships, and at other non-cybersecurity businesses, you can start on the helpdesk or in a system admin position and make your way across the industry into more security-focused work. Also, tinkering on security projects in a home lab is a great way to set yourself apart from others in an interview cycle. Focused determination and a curious mind can open this field to many who might not otherwise see it as a possibility.
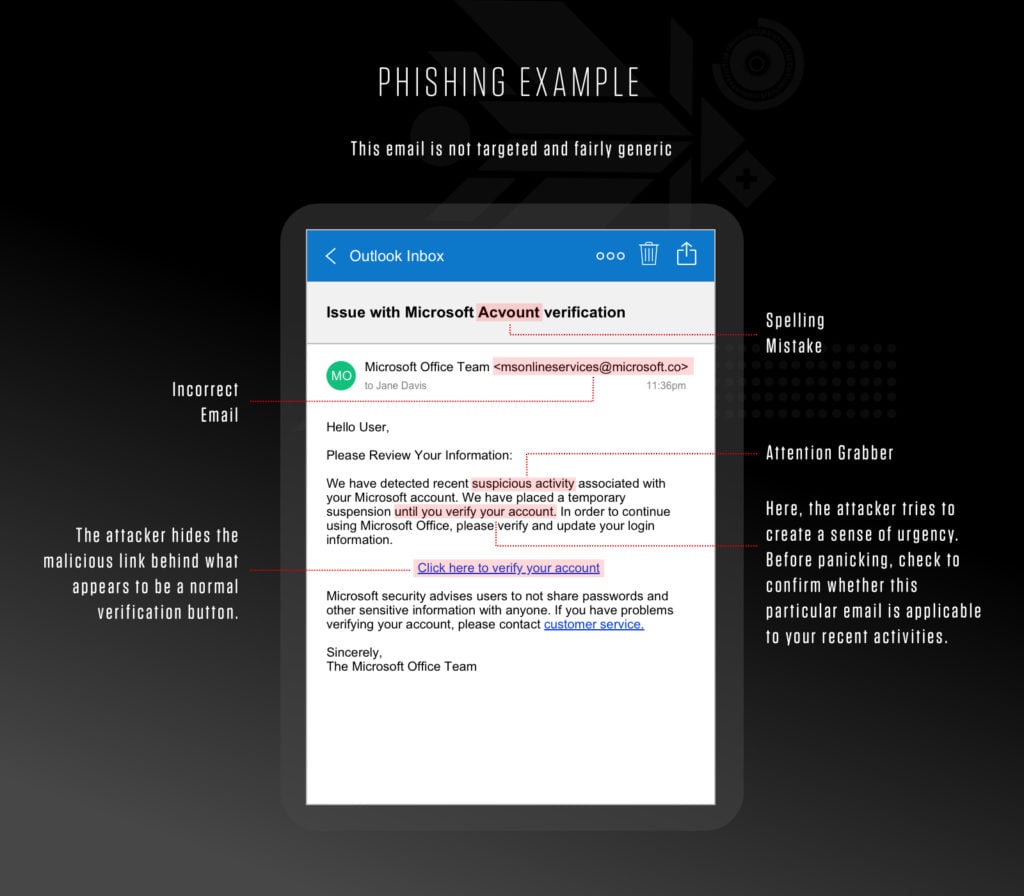
The truth of the matter is that you are already in cybersecurity. If you use a computer to do your job, at home, or at any time, including smartphones, then you are in cybersecurity. We are all part of the security team that secures our businesses, organizations, and our own data. The fact that you must be on the lookout for phishing and other scams at work and home proves this point. You are already performing your cybersecurity role when you screen your calls for fraud attempts and help your grandma avoid sending money to that ubiquitous Nigerian prince. And you are probably pretty good at it too.
Historically, though, career security practitioners have been depicted as people with their heads hovering four inches away from a computer screen 18 hours a day — not very appealing to folks with real passions and pursuits outside of the workplace. But that image couldn’t be further from the truth of what real cybersecurity talent looks like.
As a Chief Information Security Officer (CISO), I look for specific personality traits when hiring for analysts and engineers rather than a perceived interest in technology or networks. Effective cybersecurity talent, regardless of background, will always be curious, gritty and eager to learn more as new threats develop and vulnerabilities are exposed. Having an investigative mind is very helpful. In addition, people who want to understand how things work, or who like to know the answer to a mystery, are good candidates. Even musicians, or folks with an analytical mind that can recognize patterns like they recognize their own family members, stick out to me on a resume or during an interview.
Though I gained technical cybersecurity experience of my own through self-teaching, training, and working for the FBI, my humanities degree has been invaluable in encouraging me to look at problems at a holistic and systemic level. It has helped me have a greater perspective for the ancillary and downstream effects of cybersecurity attacks and policies. It has also helped me know how to communicate to various levels of leadership within my own organization and to clients, articulating the severity of a situation and the possible remedies that are available for any attack. Without the communication skills to break down cybersecurity jargon into plain English, even the most technically talented analyst will always be at a loss in explaining their value to potential customers.
The point is that it’s high time for the cybersecurity industry to take action to change its reputation as a realm of complexity and secrecy to a fast-paced industry where those with innate curiosity and leadership can thrive. My journey to cybersecurity started 20 years ago with a deep motivation to protect my country, and I have been able to take my career everywhere, from investigative work to incident response to strategic leadership. Over the next 20 years, let’s ensure that every talented individual has the power to do the same.
Adam Marrè is the Chief Information Security Officer at Arctic Wolf. Prior to joining Arctic Wolf, Adam was the Global Head of Information Security Operations and Physical Security at Qualtrics. With deep roots in the cybersecurity space, Adam spent almost 12 years with the FBI, holding positions like SWAT Senior Team Leader and Special Agent.
You must have JavaScript enabled to enjoy a limited number of articles over the next 30 days.
Sponsored Content is a special paid section where industry companies provide high quality, objective, non-commercial content around topics of interest to the Security audience. All Sponsored Content is supplied by the advertising company. Interested in participating in our Sponsored Content section? Contact your local rep.
ON DEMAND: Business-impacting events such as severe weather, man-made disasters, and supply chain disruption are increasing in frequency and making impacts around the globe.
The John F. Kennedy Center for the Performing Arts is home to some of the nation’s largest events, from the Kennedy Center Honors to the Mark Twain Prize and high-caliber theatrical and symphonic performances.
Effective Security Management, 5e, teaches practicing security professionals how to build their careers by mastering the fundamentals of good management. Charles Sennewald brings a time-tested blend of common sense, wisdom, and humor to this bestselling introduction to workplace dynamics.
Copyright ©2023. All Rights Reserved BNP Media.
Design, CMS, Hosting & Web Development :: ePublishing