GoDaddy found a multi-year security breach in December 2022, the web hosting company has just now revealed.
The breach allowed unknown third parties to gain access to GoDaddy source code, and they installed malware on the company’s servers as well.
No security breach is a good breach, but this particular one is worse than normal, and may cast doubt on the web hosting and domain services that the company offers. GoDaddy says it has added security measures to stop a similar attack in the future and is working with law enforcement to stop the bad actors.
GoDaddy first noticed a problem in early December of last year, when a few customer complaints all mentioned that their website had been “intermittently redirected,” the company said in its statement.
After taking a look, GoDaddy realized that the issue wasn’t easily reproducible, but involved “seemingly random websites hosted on our cPanel shared hosting servers.” The company eventually realized that an unauthorized party had accessed the servers in their cPanel shared hosting environment, and the issue was caused by malware that had been installed by the third-party actor.
The same hackers also “obtained pieces of code related to some services within GoDaddy.”
GoDaddy didn’t explain how the breach had happened but did say that the situation had been “remediated,” with new “security measures” rolled out to prevent future breaches.
Security breaches themselves aren’t a sign that a tech company has failed, since mitigation measures can help to reduce the severity of a breach’s impact. But just going off of what we know, this seems likely to be a rough PR hit for GoDaddy to recover from.
Not only does the breach encompass multiple years, but GoDaddy customers’ websites were vulnerable to malware as a result of the breach.
It appears to be bad news for every other major hosting platform, as well. According to the GoDaddy announcement, the breach is just one incident from a group dedicated to targeting hosting services specifically:
“We have evidence, and law enforcement has confirmed, that this incident was carried out by a sophisticated and organized group targeting hosting services like GoDaddy. According to information we have received, their apparent goal is to infect websites and servers with malware for phishing campaigns, malware distribution and other malicious activities.”
It does make sense to hack a hosting service, since it’s a one-stop shop for a huge range of other websites. And that means the customers are the true target, which is bad news for anyone currently hosting their own website.
We’ve rated and reviewed all the top web hosting platforms. While GoDaddy does make our list, it’s towards the end, trailing InMotion (the best all-around web hosting provider), Bluehost (a still-great but cheaper InMotion alternative), HostGator (the best for reliable uptime), and a few others.
Check out our full guide over here — and let’s hope they remain secure against any data breaches in the near future.
Verifying
We’re sorry this article didn’t help you today – we welcome feedback, so if there’s any way you feel we could improve our content, please email us at contact@tech.co
Adam is a writer at Tech.co and has worked as a tech writer, blogger and copy editor for more than a decade. He was a Forbes Contributor on the publishing industry, for which he was named a Digital Book World 2018 award finalist. His work has appeared in publications including Popular Mechanics and IDG Connect, and his art history book on 1970s sci-fi, ‘Worlds Beyond Time,’ is out from Abrams Books in July 2023. In the meantime, he’s hunting down the latest news on VPNs, POS systems, and the future of tech.
Despite a decrease in attacks, “ransomware remains a…
Keeping drivers safe is a top-three concern for any fleet….
According to the threat actor selling the information, at…
The new feature will be available to all Google One…
© Copyright 2023
Category: Uncategorized
-
GoDaddy Reveals Data Breach Led to Malware on Customer Sites – Tech.co
-
Trove of L.A. Students' Mental Health Records Posted to Dark Web … – The 74
The 74
America's Education News Source
Copyright 2023 The 74 Media, Inc
Update: After this story published, the Los Angeles school district acknowledged in a statement that “approximately 2,000” student psychological evaluations — including those of 60 current students — had been uploaded to the dark web.
Detailed and highly sensitive mental health records of hundreds — and likely thousands — of former Los Angeles students were published online after the city’s school district fell victim to a massive ransomware attack last year, an investigation by The 74 has revealed.
The student psychological evaluations, published to a “dark web” leak site by the Russian-speaking ransomware gang Vice Society, offer a startling degree of personally identifiable information about students who received special education services, including their detailed medical histories, academic performance and disciplinary records.
But people are likely unaware their sensitive information is readily available online because the Los Angeles Unified School District hasn’t alerted them, a district spokesperson confirmed, and leaders haven’t acknowledged the trove of records even exists. In contrast, the district publicly acknowledged last month that the sensitive information of district contractors had been leaked.
Cybersecurity experts said the revelation that student psychological records were exposed en masse and a lack of transparency by the district highlight a gap in existing federal privacy laws. Rules that pertain to sensitive health records maintained by hospitals and health insurers, which are protected by stringent data breach notification policies, differ from those that apply to education records kept by schools — even when the files themselves are virtually identical. Under existing federal privacy rules, school districts are not required to notify the public when students’ personal information, including medical records, is exposed.
But keeping the extent of data breaches under wraps runs counter to schools’ mission of improving children’s lives and instead places them at heightened risk of harm, said school cybersecurity expert Doug Levin, the national director of the K12 Security Information eXchange.
“It’s deeply disturbing that an organization that you’ve entrusted with such sensitive information is either significantly delaying — or even hiding — the fact that individuals had very sensitive information exposed,” Levin told The 74. “For a school system to wait six months, a year or longer before notifying someone that their information is out on the dark web and being potentially abused is a year that those individuals can’t take steps to protect themselves.”
In a January report, the federal Cybersecurity and Infrastructure Security Agency warned that school districts were being targeted by cyber gangs “with potentially catastrophic impacts on students, their families, teachers and administrators.” Threats became particularly acute during the pandemic as schools grew more reliant on technology. The number of publicly disclosed cybersecurity incidents affecting schools has grown from 400 in 2018 to more than 1,300 in 2021, according to the federal agency.
When L.A. schools Superintendent Alberto Carvalho acknowledged in early October that the cyber gang published some 500 gigabytes of stolen records to the dark web after the district declined to pay an unspecified ransom demand, he sought to downplay its effects on students. An early news report said the leaked files contained some students’ psychological assessments, citing “a law enforcement source familiar with the investigation.” Carvalho called that revelation “absolutely incorrect.”
“We have seen no evidence that psychiatric evaluation information or health records, based on what we’ve seen thus far, has been made available publicly,” said Carvalho, who acknowledged the hackers had “touched” the district’s massive student information system and had exposed a limited collection of students’ records, including their names and addresses.
The 500 gigabytes of stolen records include tens of thousands of individual files, including scanned copies of adults’ Social Security cards, passports, financial records and other personnel files.
The systemic release of students’ psychological assessments stolen from the Los Angeles district and published to the dark web hasn’t been previously reported. Leaked psychological evaluations use a consistent file-naming structure, allowing The 74 to isolate them from other types of district records that appear on the ransomware gang’s leak site, including those related to district contractors and files that are benign and do not contain confidential information. The 74 has independently verified that 500 students’ sensitive psychological assessments are available for download as PDF files on the Vice Society leak site, reaching a federal threshold that would require health care providers to publicly disclose such a data breach if it involved patient health records.
More than 2,200 PDFs — and a large swath of other document types — follow the consistent file-naming structure, suggesting the total number of leaked student psychological files is in the thousands. The records are at least a decade old and while they don’t appear to contain information about current students, they do contain highly personal information about former LAUSD students who are now in their 20s and 30s.
In early October, Carvalho said that people would be contacted if their information got exposed in the data breach, assuring them, “No news is good news.” By that point, Carvalho said, school district and law enforcement analysts had already reviewed about two-thirds of the data leaked on the dark web.
Now, more than four months after the schools chief denied that psychological evaluations were exposed, the nation’s second-largest school district has not changed its position publicly. A district spokesperson said that Carvalho’s statements in October “were based on the information that had been developed at that time” and that the review was still ongoing.
“Los Angeles Unified is in the process of completing its review and analysis of the data posted by the criminals responsible for the cyberattack to the dark web, to identify individuals impacted and to provide any required notifications,” the district told The 74 in a statement. “Once Los Angeles Unified has completed its review and analysis of that data, Los Angeles Unified will provide an update,” to affected individuals and the public.
The particular files posted online — students’ psycho-educational case studies — are among the most sensitive records that schools keep about children with disabilities, said Steven Catron, senior staff attorney of the Learning Rights Law Center, a Los Angeles-based nonprofit that provides free legal representation to low-income families in special education disputes with their children’s school district.
The evaluations are designed to help schools assess how a student’s disabilities and other factors affect their learning. They include a comprehensive background on the child’s medical history, observations on their home and family life, and assessments of their cognitive, academic and emotional functioning.
One of the reports notes that a student was placed in foster care “due to domestic violence in the home.” The student struggled with “a limited attention span” and often refused to complete his work, the report notes, and “is easily angered when he does not get his way.” Another states a student’s desire to “become a police officer so that he can ‘arrest people because they do drugs.’” A student’s father “works in a plant that makes airplane parts and speaks no English,” one report notes. “His mother is a librarian assistant and speaks a ‘little English.’”
In general, Catron said, such reports can include details about a family’s immigration status, sexual misconduct allegations, unfounded child abuse reports or that a student has “been hitting other children or adults in a school environment.” Yet it’s often difficult for families to get sensitive information removed from the files, he said, even if it isn’t accurate. Now, with breached student records of this nature in the public domain, “who knows what is going to happen.”
“The sheer scope of information, like you’ve seen, it’s darn broad and pretty hurtful for people,” Catron said. “If those records include those types of notes, whether correct or not, it can just cause a huge emotional strain for the family.”
The files themselves note that the assessment reports “may contain sensitive information subject to misinterpretation by untrained individuals” and that the “nonconsensual re-disclosure by unauthorized individuals is prohibited” by state law.
Available files appear to be limited to former Los Angeles students born primarily in the late 1980s and 1990s. The age of the records highlight how potential data breach victims extend far beyond current students when districts suffer hacks, Levin, the cybersecurity expert, said. Students’ sensitive information can be exposed years or even decades after they graduate if districts lack sufficient data security safeguards.
Are you a former Los Angeles Unified School District student in special education who may have been a data breach victim?
Please click here to share your story with investigative reporter Mark Keierleber.
The timeline could also complicate any potential efforts by the district to find and notify affected individuals who could unknowingly face heightened risks including embarrassment, identity theft and extortion.
“Sometimes school districts will delay notifying until they can identify every last person that they possibly can, but that can be an expensive to impossible endeavor,” Levin said. “For a school district like LAUSD to try to track people who were associated with the district say 10 years ago, that’s a daunting task and clearly is very likely to be imperfect.”
Health care providers are held to strict data privacy rules and could face steep fines in the event of a data breach involving sensitive patient records. Agencies and businesses covered by the federal Health Insurance Portability and Accountability Act are required to publicly acknowledge health data breaches affecting 500 or more people and notify the U.S. Department of Health and Human Services “without unreasonable delay and in no case later than 60 days following a breach.”
The Broward County, Florida, school district recently got caught in a data breach disclosure debacle after the country’s sixth-largest school system suffered a ransomware attack in 2021 and refused to pay an extortion demand initially set at $40 million. In response, threat actors published to a dark web leak site the personal information of nearly 50,000 district personnel enrolled in its health plan. The Broward district is currently one of four K-12 school systems listed on a data breach portal maintained by the Department of Health and Human Services. The breach portal — often referred to as the “Wall of Shame” — includes all data breaches affecting 500 or more people that were reported to the federal agency in the last 24 months.
District officials in Florida ultimately waited 154 days — three months longer than federal rules allow — to disclose the breach’s full extent on its website, according to the South Florida Sun-Sentinel. In a statement, a district spokesperson told The 74 the school system “worked diligently to investigate the incident.” Once officials realized that records related to the district’s self-insured health plan were breached, notifications to affected personnel and the federal health administration “required the gathering and sorting of significant amounts of data in order to determine the individuals to be notified.”
“That process was complex and took substantial hours,” the spokesperson said. “Under the circumstances, notification was made in an expeditious manner.”
The Broward district is a HIPAA-covered entity because it operates a self-insured health plan. But public schools aren’t generally considered “covered entities” under the health privacy law. And even when they are, students’ education records — including their health information — are exempt. They’re instead covered by the Family Educational Rights and Privacy Act, the federal student privacy law known as FERPA. The law prohibits student records from being released publicly but, unlike HIPAA, does not require schools to disclose when such breaches occur.
“The same type of information is treated differently from a compliance standpoint depending on who is holding and maintaining that information,” said student privacy expert Jim Siegl, a senior technologist with the nonprofit Future of Privacy Forum. The federal privacy rules that apply to hospitals and schools “live in separate universes. If it’s maintained by the school, it’s FERPA. If it’s maintained by your doctor, the same information is HIPAA protected.”
A small subset of Los Angeles students’ health records are covered by HIPAA, the LAUSD district spokesperson said, but the psychological assessments are not. A data breach involving student’s records — like the one in Los Angeles — could be considered a FERPA violation, according to the U.S. Department of Education.
“FERPA requires the school to maintain direct control over the records,” Siegl said. “There is a lot that goes into a FERPA violation, but I would say that within the spirit of FERPA, they did not maintain direct control over the records.”
Yet, consequences for violating FERPA are next to nonexistent. Districts can lose federal funds if they have “a policy or practice” of releasing students’ records without parental permission, a high bar that excludes occasional violations. Since the law was enacted in 1974, it’s never been used to strip funding from a district that broke the rules.
To comply with state privacy rules, the Los Angeles district has been more transparent about the systemic breach of sensitive records about distinct construction contractors. In a data breach notice posted to the California state attorney general’s office website in January, the district said its investigation into the breach had uncovered certified payroll records and other labor compliance documents that included the names, addresses and Social Security numbers of district contractors.
The data breach notice also made clear that cyber criminals had infiltrated the district’s computer network more than a month earlier than initially disclosed. Carvalho said in October that district cybersecurity officials were quick to detect the unauthorized access and, “in a very, very unique way, we stopped the attack midstream.”
The district spokesperson said LAUSD is working to determine whether any of the breached files are considered “medical information” under state law and whether a notification is required. Any data breach alert to the state attorney general’s office would coincide with notifications to affected individuals, the spokesperson said.
Asked about the school district’s notification obligations for the trove of leaked student psychological records and whether it’s investigating the matter, an AG’s office spokesperson said in an email “we can’t comment on, even to confirm or deny, a potential or ongoing investigation,” and didn’t offer any other information. Reached for comment about the data breaches in Los Angeles and Broward County, a federal Department of Health and Human Services spokesperson said its civil rights division “does not typically comment on open or potential investigations,” and declined to say anything further.
The Los Angeles district has for decades struggled with its obligations to provide special education services to children with disabilities. Last year, it reached an agreement to provide compensatory services to children with disabilities after an investigation by the U.S. Education Department’s civil rights office found it had failed to provide them during the pandemic. Parents and advocates said last month many children are still waiting for those services.
Los Angeles parent Ariel Harman-Holmes, whose three children are in special education, said she’s worried the data breach could further divert funds from those much-needed special education services.
“I would rather have those funds go back into the schools and special education rather than spending a ton on litigation or settlements about privacy issues,” said Harman-Holmes, who serves as vice chair of the district’s Community Advisory Committee for Special Education. But she acknowledged it “would be very disturbing” if her own child’s psychological evaluations were leaked online.
“Our middle son is a very private person and this could be a psychological torment to him knowing that personal observations about him were out there,” she said. “That would be very devastating to him.”
Get stories like these delivered straight to your inbox. Sign up for The 74 Newsletter
Mark Keierleber is an investigative reporter at The 74.
Start your day with the most important education news. Sign up for our free newsletter today.
Copyright 2023 The 74 Media, Inc -
Cybersecurity hiring remains red-hot—the industry to surpass $400 … – Fortune
In 2017, the global cybersecurity industry had an approximate market size of $86.4 billion, according to research conducted by Gartner, a tech research and consulting firm. But just a decade later, the market is expected to grow nearly 80%. By 2027, market research company BrandEssence projects that the global cybersecurity market will reach $403 billion; that’s with a compound annual growth rate of 12.5% between 2020 and 2027.
This rapid growth rate is the result of a cycle of actions between cybercrime actors and intelligence agencies, explains Kayne McGladrey, a Institute of Electrical and Electronics Engineers (IEEE) senior member, and cybersecurity strategist at Ascent Solutions. While cybercrime actors reinvest their illegally gained profits in developing new capabilities, employing more staff, and diversifying their supply chains, cybersecurity customers aren’t investing or hiring at the same rate.
“As a result, those companies with solutions and products in the cybersecurity industry are heavily reinvesting their profits into research and development of artificial intelligence-based solutions intended to automatically detect and remediate actions from these increasingly well-funded adversaries,” McGladrey tells Fortune. “This cycle will continue so long as it remains profitable for cybercrime actors, barring remarkable changes in how companies prioritize and address their cyber risks.”
Simply put, there are more cyber attacks happening each year. Between 2020 and 2021, the average number of cybersecurity attacks per year rose 31%, to 270 attacks, according to Accenture’s State of Cybersecurity Report 2021. And the average number of successful attacks per company was 29.
For that reason, adequate cybersecurity measures are becoming a necessary venture for companies of all shapes and sizes.
“Cybersecurity is an integral part of all businesses, whether they are online or not, especially given the proliferation of payment networks, cloud-based data storage, and everything else regardless of if they are internet facing businesses,” Yale Fox, IEEE member and CEO of Public Benefit Technologies, tells Fortune.
Plus, new technology is growing at a rapid pace. As Fox points out, artificial intelligence and machine learning are really “just starting to awaken,” he says. “We’re in the middle of a renaissance right now.”
As a result, Yale says the market could end up being larger than the projected target of $400 billion by 2027. “We’re in the eye of the storm for a rapid and exponential growth of all the tech industries.”
With massive industry growth comes the need for more trained cybersecurity professionals. But we’re already short-staffed in the U.S.—and a lot of that has to do with the fact that there simply aren’t enough people trained and qualified to work on some of these complex systems.
“Organizations are challenged in hiring cyber security experts who are equipped with the skills to defend the complex attack surface, like the cloud, and can operate the new technologies that are being purchased every year,” Adi Dar, CEO and founder of Cyberbit, a company that offers cybersecurity readiness and skills platform, tells Fortune.
In the U.S., there are about 1 million cybersecurity workers, but there were around 715,000 jobs yet to be filled as of November 2021, according to a report by Emsi Burning Glass (now Lightcast), a market research company. Worldwide, the number of unfilled cybersecurity jobs worldwide grew 350% between 2013 and 2021, from 1 million to 3.5 million, according to Cybersecurity Ventures.
Companies continue to hunt for cyber talent, but many of these jobs require credentials, certifications, or a master’s degree in the field.
“There’s just not enough people in cyber security with the skills to handle the new threat landscape,” Dar says. “Government, education, and industry should urgently get together to find a way to increase both the quantity and quality of the workforce in cybersecurity, or we’ll keep seeing an increase in spend year over year, with no real impact.”
See how the schools you’re considering fared in Fortune’s rankings of the best master’s in cybersecurity programs, public health programs, business analytics programs, data science programs, and part-time, executive, full-time, and online MBA programs. -
Hackers Stole GoDaddy Source Code in a Multi-Year Data Breach – HackRead
In a filing with the Securities and Exchange Commission (SEC), GoDaddy revealed that three serious security breaches had impacted the company, boasting 21 million customers and almost $4 billion in revenue.
On Friday, GoDaddy, the world’s leading web hosting firm, confirmed that its network had been impacted by a data breach that started in 2020 and continued until 2022. As a result of this compromise, unidentified hackers stole the company’s source code.
Additionally, part of the stolen data included employees’ and customers’ login credentials. Moreover, the flaw allowed attackers to install malware, which would redirect customers’ websites to malicious domains.
This should not come as a surprise, since GoDaddy has a history of security-related incidents. For instance, in November 2021, hackers accessed 1.2 million GoDaddy customers’ accounts.
In November 2020, GoDaddy revealed that its employees had been tricked by hackers into modifying the DNS settings of at least two cryptocurrency websites. In April 2020, Escrow.com was defaced by hackers after they managed to hack one of GoDaddy’s employees.
As for the recent incident, in a filing with the Securities and Exchange Commission, GoDaddy revealed that three serious security breaches had impacted the company, boasting 21 million customers and almost $4 billion in revenue.
The incident started in 2020, and the latest was recorded in 2022. The company noted that a sophisticated hacker group was responsible for all the incidents. This means the same group has repeatedly invaded its networks and may or may not have left, despite the company’s extensive security measures.
The first incident occurred in March 2020, when the attackers obtained login credentials and accessed a limited number of employee accounts and hosting accounts belonging to approximately 28,000 customers. But they couldn’t access the main accounts of GoDaddy customers.
The most recent invasion was noticed in December of 2022. At that time, the attacker accessed the cPanel hosting servers. The company explained that it has responded to subpoenas about the incident that the Federal Trade Commission (FTC) issued in July 2020 and October 2021.
In November 2021, GoDaddy discovered another security breach in which the attacker obtained a password that provided access to GoDaddy’s Managed WordPress service source code.
The attackers gained access in September 2021 and obtained login credentials of WordPress admin accounts, email addresses, and FTP accounts of 1.2 million inactive currently Managed WordPress users. GoDaddy formally disclosed the breach in November 2021.
“We believe these incidents are part of a multi-year campaign by a sophisticated threat actor group that, among other things, installed malware on our systems and obtained pieces of code related to some services within GoDaddy.”
GoDaddy has claimed that it has evidence, and law enforcement authorities have also confirmed that a security breach occurred, performed by an organized and sophisticated group.
Furthermore, the company added that the hackers’ primary targets are hosting services such as GoDaddy, infecting websites with malware, and launching phishing campaigns.
Super secure VPN
Minimal data logging
Favorable privacy policy
Visit IPVanish
HACKREAD is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance and Hacking News with full-scale reviews on Social Media Platforms & Technology trends. Founded in 2011, HackRead is based in the United Kingdom.
Hackread.com is among the registered trademarks of Gray Dot Media Group Ltd. Company registration number 12903776 in regulation with the United Kingdom Companies House. The registered address is 85 Great Portland Street, London, England, W1W 7LT The display of third-party trademarks and trade names on the site do not necessarily indicate any affiliation or endorsement of Hackread.com. If you click an affiliate link and buy a product or service, we may be paid a fee by that merchant. -
CISA Tells Agencies What to Prioritize to Meet Cybersecurity Log … – Nextgov
dem10/Getty Images
By
As federal agencies work to meet cybersecurity records mandates issued in 2021, the government’s lead cybersecurity department released general guidance to help agency leaders prioritize parts of what can be a costly and resource-intensive implementation.The Office of Management and Budget issued a memo in August 2021 telling agencies to create and maintain certain network traffic data that can be useful in the aftermath of a cybersecurity incident. The memo—”Improving the Federal Government’s Investigative and Remediation Capabilities Related to Cybersecurity Incidents”—requires agencies store cybersecurity event logs for at least 30 months and full packet capture date, or PCAPs, for 72 hours.
The latter requirement has raised some concerns among cybersecurity experts who note that PCAP data sets are large—resulting in high data storage costs—and are often not as valuable on encrypted traffic. Add to that the low likelihood that a security breach would be detected within the 72-hour window for maintaining those records, and the potential value of PCAP data for forensics doesn’t always justify the cost.
But with a mandate in place, agencies are required to implement PCAP and maintain cybersecurity logs. So, the Cybersecurity and Infrastructure Security Agency developed a brief guidance document to help agencies prioritize implementation to effectively reach the lowest baseline in time for OMB reviews.
The guidance was offered to agencies in December but was expected to be released publicly Monday.
“Agencies should make risk-informed decisions about where log collection is most beneficial for improving cybersecurity incident detection and investigation,” the document states. “CISA recommends that agencies prioritize high value asset (HVA) systems, high impact systems, and the enterprise IT network.”
CISA suggests focusing on “identity providers like Azure Active Directory or Active Directory,” and “internet-accessible systems—e.g., web applications—and systems that interact with the internet regularly.”
The document offers a tiered list of the kinds of network activity that should be prioritized for logs, as well as offering tips for keeping PCAP data size low and, in turn, keeping costs down.
“Agencies can minimize the size of collected PCAP by filtering out encrypted traffic—Transport Layer Security, etc.—and collecting PCAP only at central points—e.g., first hop in/out of an agency-managed network,” the document states, acknowledging that captures of encrypted packets will only offer limited information for forensics purposes, such as the size of the packet and its destination but not its contents.
The document also clarifies that agencies do not need to break encryption to be in compliance.
“While maturity level 2 requires ‘full packet capture data: decrypted plaintext and clear text,’ the Inspection of Encrypted Data section of Table 3 states, ‘if agencies do not perform full traffic inspection, they should log the metadata available to them,’” CISA officials wrote in the FAQ section. That said, “If an agency implements a decryption capability, they need to log decrypted packet capture.”
Separate from the document, a CISA spokesperson told Nextgov the decision to require agencies to store PCAP data for 72 hours was about balancing the value to forensic investigations against the expense of storing that data.
“A 72-hour retention time means the PCAP data can be used to inform the investigation of network or host-based intrusion alerts—e.g. to confirm an alert is truly malicious—while limiting the overall storage costs,” the spokesperson said in an emailed statement.
The spokesperson also noted the importance of the other event logs required under the mandate, which are to be retained for at least 30 months.
“In addition, many of the logging types required by [the OMB logging memo] M-21-31 provide significant value in incident response even where PCAP is no longer available, such as process creation, user sign-in, Domain Name System (DNS) queries, and firewall logs,” they said.The document also offers a glimpse at how agencies will coordinate with CISA and the FBI after a cyber incident has been identified, including creating new user accounts for agents.
“When a security incident occurs, CIOs will provision accounts within an agency environment and provide CISA and FBI officials credentials granting access to data by the same means as agency employees,” the document states.
CISA hopes to automate some of that process in the future, including “explor[ing] approaches to allow queries of the data from outside the agency, or approaches that will allow agencies to send data continuously to CISA,” so long as those methods don’t hamper the performance of agency networks.
Prioritization list
With an understanding of “the technical and operational obstacles to collecting and storing 72 hours of PCAP,” CISA offered a specific, ordered priority list of the types of events that should be captured to meet the lowest level of policy compliance:
NEXT STORY: CISA Urges 'Increased Vigilance' for Cyber Threats on Anniversary of Russia’s Invasion of Ukraine
Do Not Sell My Personal Information
When you visit our website, we store cookies on your browser to collect information. The information collected might relate to you, your preferences or your device, and is mostly used to make the site work as you expect it to and to provide a more personalized web experience. However, you can choose not to allow certain types of cookies, which may impact your experience of the site and the services we are able to offer. Click on the different category headings to find out more and change our default settings according to your preference. You cannot opt-out of our First Party Strictly Necessary Cookies as they are deployed in order to ensure the proper functioning of our website (such as prompting the cookie banner and remembering your settings, to log into your account, to redirect you when you log out, etc.). For more information about the First and Third Party Cookies used please follow this link.
Manage Consent Preferences
Strictly Necessary Cookies – Always Active
We do not allow you to opt-out of our certain cookies, as they are necessary to ensure the proper functioning of our website (such as prompting our cookie banner and remembering your privacy choices) and/or to monitor site performance. These cookies are not used in a way that constitutes a “sale” of your data under the CCPA. You can set your browser to block or alert you about these cookies, but some parts of the site will not work as intended if you do so. You can usually find these settings in the Options or Preferences menu of your browser. Visit www.allaboutcookies.org to learn more.
Sale of Personal Data, Targeting & Social Media Cookies
Under the California Consumer Privacy Act, you have the right to opt-out of the sale of your personal information to third parties. These cookies collect information for analytics and to personalize your experience with targeted ads. You may exercise your right to opt out of the sale of personal information by using this toggle switch. If you opt out we will not be able to offer you personalised ads and will not hand over your personal information to any third parties. Additionally, you may contact our legal department for further clarification about your rights as a California consumer by using this Exercise My Rights link
If you have enabled privacy controls on your browser (such as a plugin), we have to take that as a valid request to opt-out. Therefore we would not be able to track your activity through the web. This may affect our ability to personalize ads according to your preferences.
Targeting cookies may be set through our site by our advertising partners. They may be used by those companies to build a profile of your interests and show you relevant adverts on other sites. They do not store directly personal information, but are based on uniquely identifying your browser and internet device. If you do not allow these cookies, you will experience less targeted advertising.
Social media cookies are set by a range of social media services that we have added to the site to enable you to share our content with your friends and networks. They are capable of tracking your browser across other sites and building up a profile of your interests. This may impact the content and messages you see on other websites you visit. If you do not allow these cookies you may not be able to use or see these sharing tools.
If you want to opt out of all of our lead reports and lists, please submit a privacy request at our Do Not Sell page.Cookie List
A cookie is a small piece of data (text file) that a website – when visited by a user – asks your browser to store on your device in order to remember information about you, such as your language preference or login information. Those cookies are set by us and called first-party cookies. We also use third-party cookies – which are cookies from a domain different than the domain of the website you are visiting – for our advertising and marketing efforts. More specifically, we use cookies and other tracking technologies for the following purposes:
Strictly Necessary Cookies
We do not allow you to opt-out of our certain cookies, as they are necessary to ensure the proper functioning of our website (such as prompting our cookie banner and remembering your privacy choices) and/or to monitor site performance. These cookies are not used in a way that constitutes a “sale” of your data under the CCPA. You can set your browser to block or alert you about these cookies, but some parts of the site will not work as intended if you do so. You can usually find these settings in the Options or Preferences menu of your browser. Visit www.allaboutcookies.org to learn more.
Functional Cookies
We do not allow you to opt-out of our certain cookies, as they are necessary to ensure the proper functioning of our website (such as prompting our cookie banner and remembering your privacy choices) and/or to monitor site performance. These cookies are not used in a way that constitutes a “sale” of your data under the CCPA. You can set your browser to block or alert you about these cookies, but some parts of the site will not work as intended if you do so. You can usually find these settings in the Options or Preferences menu of your browser. Visit www.allaboutcookies.org to learn more.
Performance Cookies
We do not allow you to opt-out of our certain cookies, as they are necessary to ensure the proper functioning of our website (such as prompting our cookie banner and remembering your privacy choices) and/or to monitor site performance. These cookies are not used in a way that constitutes a “sale” of your data under the CCPA. You can set your browser to block or alert you about these cookies, but some parts of the site will not work as intended if you do so. You can usually find these settings in the Options or Preferences menu of your browser. Visit www.allaboutcookies.org to learn more.
Sale of Personal Data
We also use cookies to personalize your experience on our websites, including by determining the most relevant content and advertisements to show you, and to monitor site traffic and performance, so that we may improve our websites and your experience. You may opt out of our use of such cookies (and the associated “sale” of your Personal Information) by using this toggle switch. You will still see some advertising, regardless of your selection. Because we do not track you across different devices, browsers and GEMG properties, your selection will take effect only on this browser, this device and this website.
Social Media Cookies
We also use cookies to personalize your experience on our websites, including by determining the most relevant content and advertisements to show you, and to monitor site traffic and performance, so that we may improve our websites and your experience. You may opt out of our use of such cookies (and the associated “sale” of your Personal Information) by using this toggle switch. You will still see some advertising, regardless of your selection. Because we do not track you across different devices, browsers and GEMG properties, your selection will take effect only on this browser, this device and this website.
Targeting Cookies
We also use cookies to personalize your experience on our websites, including by determining the most relevant content and advertisements to show you, and to monitor site traffic and performance, so that we may improve our websites and your experience. You may opt out of our use of such cookies (and the associated “sale” of your Personal Information) by using this toggle switch. You will still see some advertising, regardless of your selection. Because we do not track you across different devices, browsers and GEMG properties, your selection will take effect only on this browser, this device and this website.
Help us tailor content specifically for you: -
January 2023 Healthcare Data Breach Report – HIPAA Journal
The HIPAA Journal is the leading provider of news, updates, and independent advice for HIPAA compliance
Posted By HIPAA Journal on Feb 22, 2023
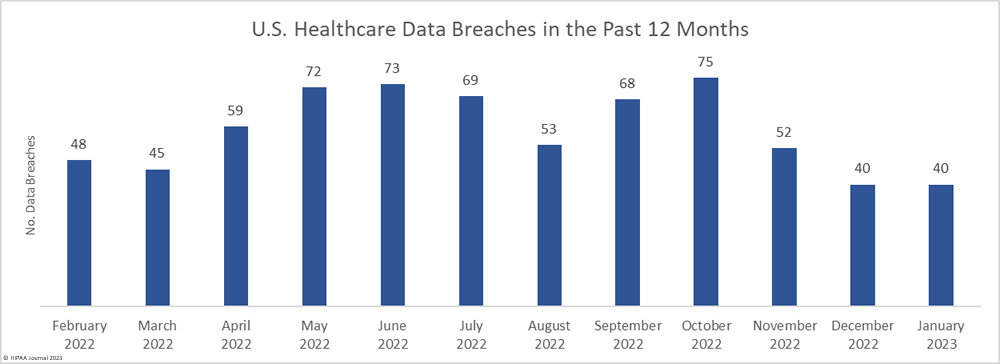
January is usually one of the quietest months of the year for healthcare data breaches and last month was no exception. In January, 40 data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights, the same number as in December 2022. January’s total is well below the 53 data breaches reported in January 2022 and the 12-month average of 58 data breaches a month.
For the second successive month, the number of breached records has fallen, with January seeing just 1,064,195 healthcare records exposed or impermissibly disclosed – The lowest monthly total since June 2020, and well below the 12-month average of 4,209,121 breached records a month.
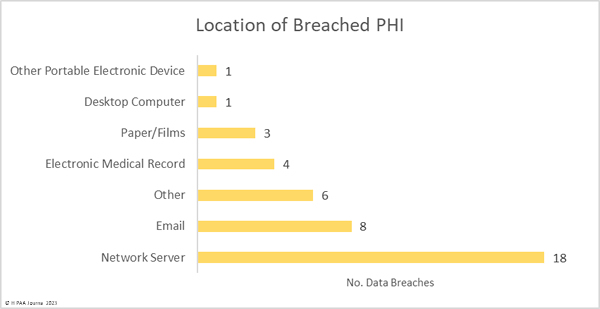
In January there were 13 data breaches involving 10,000 or more records, 8 of which involved hacked network servers and email accounts. The largest data breach of the month affected Mindpath Health, where multiple employee email accounts were compromised. 5 unauthorized access/disclosure incidents were reported that impacted more than 10,000 individuals, three of which were due to the use of tracking technologies on websites. The tracking code collected individually identifiable information – including health information – of website users and transmitted that information to third parties such as Google and Meta, including the month’s second-largest breach at BayCare Clinic. Another notable unauthorized access incident occurred at the mobile pharmacy solution provider, mscripts. Its cloud storage environment had been misconfigured, exposing the data of customers of its pharmacy clients on the Internet for 6 years.
Just over half of the 40 data breaches reported in January were hacking/IT incidents, the majority of which involved hacked network servers. Ransomware attacks continue to be conducted, although the extent to which ransomware is used is unclear, as many HIPAA-regulated entities do not disclose the exact nature of their hacking incidents, and some entities have not made public announcements at all. Across the 23 hacking incidents, the records of 698,295 individuals were exposed or stolen. The average breach size was 30,61 records and the median breach size was 5,264 records.
Delivered via email so please ensure you enter your email address correctly.
Your Privacy Respected
HIPAA Journal Privacy Policy
There was an increase in unauthorized access/disclosure incidents in January, with 15 incidents reported. The nature of 7 of the unauthorized access/disclosure incidents is unknown at this stage, as announcements have not been made by the affected entities. 5 of the 15 incidents were due to the use of tracking technologies on websites and web apps. Across the 15 unauthorized access/disclosure incidents, 362,629 records were impermissibly accessed or disclosed. The average breach size was 24,175 records and the median breach size was 3,780 records. There were two theft incidents reported, one involving stolen paper records and one involving a stolen portable electronic device. Across those two incidents, 3,271 records were stolen. No loss or improper disposal incidents were reported.
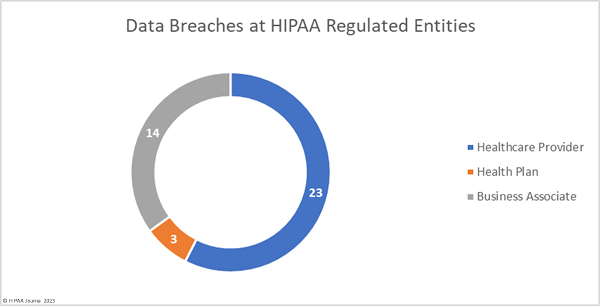
Healthcare providers were the worst affected HIPAA-covered entity with 31 reported data breaches and 5 data breaches were reported by health plans. While there were only 4 data breaches reported by business associates of HIPAA-covered entities, 14 data breaches had business associate involvement. 10 of those breaches were reported by the covered entity rather than the business associate. The chart below shows the breakdown of data breaches based on where they occurred, rather than which entity reported the breach.
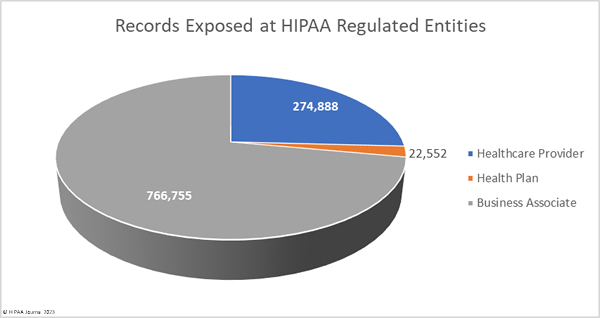
The chart below highlights the impact of data breaches at business associates. 23 data breaches occurred at health plans, involving almost 275,000 records. The 14 data breaches at business associates affected almost three times as many people.
California was the worst affected state with 7 breaches reported by HIPAA-regulated entities based in the state, followed by Texas with 6 reported breaches. January’s 40 data breaches were spread across 40 U.S. states.
The Office for Civil Rights announced one settlement in January to resolve potential violations of the HIPAA Right of Access. OCR investigated a complaint from a personal representative who had not been provided with a copy of her deceased father’s medical records within the allowed 30 days. It took 7 months for those records to be provided. Life Hope Labs agreed to pay a $16,500 financial penalty and adopt a corrective action plan that will ensure patients are provided with timely access to their medical records in the future. This was the 43rd penalty to be imposed under OCR’s HIPAA Right of Access enforcement initiative, which was launched in the fall of 2019. No HIPAA enforcement actions were announced by state attorneys general in January.
Author: Steve Alder is the editor-in-chief of HIPAA Journal. Steve is responsible for editorial policy regarding the topics covered on HIPAA Journal. He is a specialist on healthcare industry legal and regulatory affairs, and has several years of experience writing about HIPAA and other related legal topics. Steve has developed a deep understanding of regulatory issues surrounding the use of information technology in the healthcare industry and has written hundreds of articles on HIPAA-related topics.
Delivered via email so please ensure you enter your email address correctly.
Your Privacy Respected
HIPAA Journal Privacy Policy
Delivered via email so please ensure you enter your email address correctly.
Your Privacy Respected
HIPAA Journal Privacy Policy
HIPAA Journal provides the most comprehensive coverage of HIPAA news anywhere online, in addition to independent advice about HIPAA compliance and the best practices to adopt to avoid data breaches, HIPAA violations and regulatory fines. HIPAA Journal’s goal is to assist HIPAA-covered entities achieve and maintain compliance with state and federal regulations governing the use, storage and disclosure of PHI and PII.
Receive weekly HIPAA news directly via email
HIPAA News
Regulatory Changes
Breach News
HITECH News
HIPAA Advice
Email Never Shared
Cancel Any Time
Privacy Policy
Copyright © 2014-2023 HIPAA Journal. All rights reserved.
Get Help With Your HIPAA Compliance
Eliminate Risk Of Non-Compliance
Your Privacy Respected Please see HIPAA Journal privacy policy
Get Help With Your
HIPAA Compliance
Your Privacy Respected
Please see HIPAA Journal privacy policy
For Individuals
Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunction’s Certificate Of Completion
Your Privacy Respected
HIPAA Journal Privacy Policy -
I Got A Measly $14.90 From Equifax’s Data Breach Settlement – Forbes
Close-up of the hand of a man holding a mobile phone open to the web site of credit bureau Equifax, … [+]
Americans likely can’t even fill up their gas tanks with the paltry payments EquifaxEFX is providing for allowing hackers to easily steal Social Security numbers and other personal identifiable information. The payments are part of the company’s settlement with the Federal Trade Commission (FTC) over a 2017 data breach that exposed the personal information of 147 million Americans.
In 2019, people affected by the breach were able to file claims for compensation. Those who suffered direct losses due to the breach and were able to provide documentation of out-of-pocket costs were eligible for up to $20,000. Those who didn’t suffer a direct loss were still eligible for some relief, including a one-time cash payment of up to $125 and additional compensation for time spent “remedying fraud, identity theft, or other misuse of your personal information caused by the data breach, or purchasing credit monitoring or freezing credit reports.”
Payments for eligible claims were sent starting this past December. I received an envelope with a check for $14.90; a far cry from the $125 one-time cash payment that had been touted by the FTC after the settlement. Perhaps I should consider myself lucky as others claimed to have received payments as low as $2.64; the modal amount anecdotally appears to be around $5.20.
The low-dollar payouts are the result of an anemic settlement negotiated by the FTC. As part of the settlement’s restitution fund, Equifax had to create a fixed pot of $31 million to cover compensation for consumers whose data was stolen but hadn’t yet been the victim of any direct loss. As I wrote back in 2019, the $31 million cap “illuminates a potential flaw in the settlement that regulators negotiated with Equifax. Providing a fixed amount of compensation available to consumers is clearly in Equifax’s best interest because it caps the company’s financial exposure. But does it really serve consumers who were affected by the breach? Instead, why not offer a fixed amount of money to anyone who files a claim?”
The FTC believed that only a minute fraction of the 147 million Americans would care enough to file a claim. Robert Schoshinski, assistant director in the division of privacy and identity protection at the FTC, asserted in a 2019 blog post that “the public response to the settlement has been overwhelming” and that there has been “an unexpected number of claims.”
With a purported settlement payment of $125 and a fixed pot of $31 million, Schoshinski appears to have calculated that only 248,000 Americans would file a claim and ask for the cash payment. That translates to a forecasted claim rate of 0.17%. I questioned this forecast in 2019: “was it reasonable to assume that only 248,000 would want to at least get some money back after Equifax’s egregious handling of their data? Was it reasonable to assume that there wouldn’t be more anger and a desire to make Equifax pay for its security lapses?”
It is hard to know the average payment made by Equifax, but it appears to be quite low. If it were $5.20, that would mean 28 million Americans filed a claim, or close to 20% of eligible individuals. Even if the average payment were $15, that would mean close to 10 million Americans filed a claim, or 6.7%.
While I’m happy to have a few more dollars in my bank account, I’d be even happier if Equifax had been truly held accountable for its egregious data breach. “Even when companies are unquestionably at legal fault, the victims of data malfeasance are frequently unable to receive adequate compensation, if anything at all,” writes Indiana University law professor Joao Marinotti in an NYU Law Review article. Settlements like the Equifax one “neither affect the business practices of these global giants, nor do they provide adequate remedies for the victims harmed. If these consequences neither deter future cyber-negligence nor compensate victims for harms experienced, what, then, are they for? Unfortunately, some argue they are ‘mostly exercises in public relations,’ remediating the reputation of both regulators and companies alike.”
Regardless, I’m off to pump a few “free” gallons of gas. -
Hutchinson Clinic issues alert concerning December data breach – KWCH
WICHITA, Kan. (KWCH) – A Kansas health clinic issued a notice to federal law enforcement about a data breach that happened late last year. The Hutchinson Clinic said around Dec. 21, it was made aware of suspicious activity related to its computer systems.
The clinic said a hacker they labeled “an unauthorized actor” had the ability to acquire information that included names, contact information, Social Security numbers, driver’s license numbers, health insurance information and physician names.
The Hutchinson Clinic said it immediately launched an investigation with assistance from third-party forensic specialists “to secure [its] network and to determine the nature and scope of the activity.”
The response includes an ongoing effort to alert any current or former patients and employees whose information may have been impacted. The clinic included the following statement with its notice:
“We at Hutchinson Clinic take this event and the security of your information seriously. Upon learning of this event, we immediately took steps to secure our network and maintain operations in a safe and secure fashion. As part of our ongoing commitment to the privacy of personal information in our care, we are working to review our existing policies and procedures and to implement additional administrative and technical safeguards to further secure the information on our systems.”
Copyright 2023 KWCH. All rights reserved. To report a correction or typo, please email news@kwch.com -
Attorneys General Bring Multistate Data Breach Settlement Against … – WilmerHale
On February 17, 2023, the state attorneys general of Pennsylvania and Ohio reached a settlement with Ohio-based DNA Diagnostics Center (“DDC”) for a 2021 data breach that affected 2.1 million individuals nationwide and resulted in a breach of the personal information of nearly 46,000 patients. The hacking incident involved legacy data from databases that were not in business use, but that DDC had acquired as part of an acquisition in 2012. As part of the settlement deal, DDC will pay a fine totaling $400,000. The company will also implement heightened data security measures, including updating the asset inventory of its network and disabling or removing data deemed unnecessary for any legitimate business purpose.
This settlement further indicates that companies that process genetic data, health information, and other sensitive categories of information are going to continue to catch the eye of regulators for data breaches, especially if these breaches are the result of outdated security practices. In addition to state AGs, companies regulated by the Health Insurance Portability and Accountability Act (HIPAA) need to be aware of potential enforcement by the Department of Health and Human Services. And all companies need to be paying attention to FTC enforcement in this space, especially in light of its recent enforcement action against GoodRx. Businesses that process sensitive personal information in the ordinary course of business should proactively review and update their security practices to mitigate their potential risk of a security incident (as well as a subsequent regulatory investigation).
This settlement also highlights the importance of safeguarding legacy data. Organizations storing protected health information and other sensitive personal information should conduct risk analyses and comprehensive due diligence of legacy databases, along with monitoring databases actively in use. Companies should also review and revise their data retention and disposal policies as needed to limit their relevant risk.
We have provided a summary of the incident and settlement as well as critical considerations below. Please feel free to reach out to us with any questions you may have.
DDC’s Data Breach
DDC is one of the largest private DNA testing laboratories in the United States. The affected databases contained sensitive information of over 2 million individuals who had received DNA testing services between 2004 and 2012, including names, social security numbers, and payment information. DDC had acquired these databases from Orchid Cellmark in 2012. This data had been archived as was not used for any business purpose. According to DDC, the company was unaware that this data had been inadvertently transferred as part of the acquisition.
DDC discovered the data breach that prompted the investigation on August 6, 2021, when the company detected suspicious activity in some of its archived databases. The internal investigation concluded that the databases had been subject to unauthorized access between May 24 and July 28, 2021. An unauthorized third party had logged in via VPN on May 24 using a DDC account, having harvested credentials from a domain controller that provided password information for each account in the network. Using a test account with administrator privileges, the hacker installed the malware Cobalt Strike to exfiltrate the data over the course of two months. 5 servers that contained backups of 28 databases were compromised in the incident. In September 2021, the threat actor demanded payment from DDC for the return and deletion of the stolen data and payment was made.
According to court documents, prior to the data breach, a third-party data breach monitoring vendor had detected the breach and attempted to notify DDC of suspicious activity. The attempts to alert the company had been overlooked by company employees for nearly two months.
Alleged Violations and Settlement Terms
The states’ attorneys general investigation concluded that DDC engaged in deceptive or unfair cybersecurity practices by making material misrepresentations in its privacy policy regarding its safeguarding of consumers’ personal information, which left consumers’ personal data vulnerable to unauthorized access.
In addition to the fine, the settlement requires DDC to maintain reasonable security policies to protect consumer personal information. DDC will also ensure timely software updates, penetration-testing of its networks, and implementation of reasonable access controls such as multi-factor authentication. Particularly regarding legacy systems, DDC will conduct annual security risk assessments of its networks and disable or remove any assets not necessary for any legitimate business purpose.
Key Considerations for Companies
Any organization maintaining sensitive user information should keep the following considerations in mind:
Unless you are an existing client, before communicating with WilmerHale by e-mail (or otherwise), please read the Disclaimer referenced by this link.(The Disclaimer is also accessible from the opening of this website). As noted therein, until you have received from us a written statement that we represent you in a particular manner (an “engagement letter”) you should not send to us any confidential information about any such matter. After we have undertaken representation of you concerning a matter, you will be our client, and we may thereafter exchange confidential information freely.
Thank you for your interest in WilmerHale. -
Ireland Set to Notify 20,000 More Health Data Breach Victims – BankInfoSecurity.com
Breach Notification , Business Continuity Management / Disaster Recovery , Cybercrime
Ireland’s child and family agency, Tusla, says it is beginning a months-long process to notify 20,000 individuals that their personal information was exposed in the May 2021 ransomware attack against the Health Service Executive.
See Also: State of Brand Protection Report
The HSE is Ireland’s publicly funded national healthcare system and social services agency. It formerly provided IT services to Tusla.
An investigation into the ransomware attack against HSE, led by An Garda Síochána – Ireland’s police force – found that “some personal information belonging to a number of people who have been involved with Tusla services and a small number of Tusla employees was illegally accessed and data was copied,” the agency says.
Data handled by Tusla includes information gathered by providing child protection and welfare services; adoption and foster care; early years services; domestic, sexual and gender-based violence services; family and community support services; and more.
Tusla says the process of notifying the 20,000 victims likely won’t be complete until November.
Working with Ireland’s data protection authority – the Data Protection Commissioner, which enforces privacy rules, including the EU General Data Protection Regulation – Tusla says it has developed a notification process for victims. All individuals whose personal details were exposed in the attack on HSE will receive a registered letter via the national postal service.
Each letter will contain a unique PIN for each breach victim, which they can use to access their information through the Tusla Personal Information Access Portal, backed by telephone-based support if they need assistance. Alternately, victims can set up an in-person meeting with a case worker to review the data that was exposed.
Tusla says the delay between the attack and eventual victim notification is due to the challenge of reconciling which records were exposed and the patients associated with the records.
“At the end of December 2021, An Garda Síochána provided Tusla with a copy of the files that were illegally accessed and copied,” it says. “Tusla has undertaken an extensive process to carefully review all of this information, to identify individuals affected in accordance with GDPR guidance, and guidance from the Data Protection Commission.”
On a per-victim basis, the agency has also had to review all of the exposed records to redact any information they might contain about other individuals, when necessary, to protect those individuals’ data rights.
“We acknowledge that it has taken some time for the commencement of this notification program; however, it was crucial that each record that was affected by the cyberattack was carefully reviewed to identify the people affected,” says Kate Duggan, Tusla’s director of services and integration.
“We also have to ensure that letters are being sent to verified addresses,” she adds. “Notifications will continue over the coming months, and we ask for understanding and patience as we continue to work through this complex process.”
Tusla says that it will communicate with victims only by registered letter and never by text messages, phone calls, emails or social media.
Despite the personal data having been exfiltrated during the Conti attack, it’s possible that none of it has been sold via cybercrime forums or dumped via data leaks.
“We have seen no evidence that any of the Tusla information that was affected has been published on the internet or dark web, and we are continuing to monitor the situation with the assistance of cybersecurity experts,” Duggan says. “There is also no evidence that any of the Tusla information has been involved in scams or other fraudulent activity.”
The now-defunct Russian ransomware group Conti took credit for the attack, which began on March 16, 2021, with a phishing email carrying a malicious Microsoft Excel file attachment. By the end of the attack, on May 14, 2021, nearly 80% of data managed by HSE – including medical and banking information – had been forcibly encrypted, and attackers held the decryption key.
Separately, HSE has already notified approximately 113,000 individuals – 94,800 patients and 18,200 staff members – that their data may have been stolen by attackers.
While Conti made a big show of providing a “free” decryptor to HSE, on account of it being part of the National Health Service, cleanup costs have been extreme. As of October 2022, mitigating the attack, restoring systems, probing the incident and notifying victims had already cost more than 80 million euros – or $85 million.
HSE also has been overhauling its IT environment in light of numerous deficiencies identified by consultancy PricewaterhouseCoopers, which it hired to review its cybersecurity posture.
Following the May 2021 attack, Tusla says it had systems restored by June 30, 2021. Since then, it has largely stopped using any HSE-managed IT systems.
“Much of Tusla’s IT infrastructure has since undergone a migration to Tusla-owned and secured systems, of which cybersecurity is a cornerstone,” the agency says. “We are monitoring and regularly assessing our systems for vulnerabilities and opportunities for improvement with the assistance of cybersecurity experts, to help protect the data that we hold from any future attacks.”
Executive Editor, DataBreachToday & Europe, ISMG
Schwartz is an award-winning journalist with two decades of experience in magazines, newspapers and electronic media. He has covered the information security and privacy sector throughout his career. Before joining Information Security Media Group in 2014, where he now serves as the executive editor, DataBreachToday and for European news coverage, Schwartz was the information security beat reporter for InformationWeek and a frequent contributor to DarkReading, among other publications. He lives in Scotland.
Covering topics in risk management, compliance, fraud, and information security.
By submitting this form you agree to our Privacy & GDPR Statement
whitepaper
whitepaper
whitepaper
3rd Party Risk Management
Breach Notification
Governance & Risk Management
Attack Surface Management
Governance & Risk Management
Continue »
90 minutes · Premium OnDemand
Overview
From heightened risks to increased regulations, senior leaders at all levels are pressured to improve their organizations’ risk management capabilities. But no one is showing them how – until now.
Learn the fundamentals of developing a risk management program from the man who wrote the book on the topic: Ron Ross, computer scientist for the National Institute of Standards and Technology. In an exclusive presentation, Ross, lead author of NIST Special Publication 800-37 – the bible of risk assessment and management – will share his unique insights on how to:
Sr. Computer Scientist & Information Security Researcher, National Institute of Standards and Technology (NIST)
Was added to your briefcase
Ireland Set to Notify 20,000 More Health Data Breach Victims
Ireland Set to Notify 20,000 More Health Data Breach Victims
Sign in now
Need help registering?
Contact support
Complete your profile and stay up to date
Contact Support
Create an ISMG account now
Create an ISMG account now
Need help registering?
Contact support
Sign in now
Need help registering?
Contact support
Sign in now
Our website uses cookies. Cookies enable us to provide the best experience possible and help us understand how visitors use our website. By browsing bankinfosecurity.com, you agree to our use of cookies.