On February 22, 2023, Alvaria, Inc. filed notice of a data breach with the Attorney General of Massachusetts after confirming that a recent cybersecurity event was a Hive ransomware attack resulting in confidential employee information being leaked. Based on the company’s official filing, the incident resulted in an unauthorized party gaining access to consumers’ names, Social Security numbers, passport numbers, financial account information, health insurance information and tax-related information. After confirming that consumer data was leaked, Alvaria began sending out data breach notification letters to all employees who were impacted by the recent data security incident.
If you are a current or former employee of Alvaria, it’s possible that the recent Hive Ransomware attack compromised the security of your personal information. As we’ve discussed in previous posts, ransomware attacks like these are becoming increasingly common. They also significantly increase your risk of identity theft and other frauds. Therefore, as a data breach victim, it is imperative that you understand how to mitigate these risks and what you can do to hold a company that negligently leaked your information accountable.
The available information regarding the Alvaria breach comes from the company’s filing with the Attorney General of Massachusetts. According to this source, on November 28, 2022, Alvaria was targeted in a Hive Ransomware attack. In response, Alvaria contained the incident, notified the FBI, and began investigating what data was removed from the company’s computer network. However, while this investigation was underway, Hive Ransomware leaked certain information onto the group’s Dark Web leak site. While none of the leaked information belonged to consumers or employees, it proved that the attack occurred. This prompted the company to investigate the incident further to determine what other information may have been leaked. Ultimately, Alvaria was able to determine that confidential employee information was accessible to the hackers.
Upon discovering that sensitive consumer data was made available to an unauthorized party, Alvaria began to review the affected files to determine what information was compromised and which consumers were impacted. While the breached information varies depending on the individual, it may include your name, Social Security number, passport number, financial account information, health insurance information and tax-related information.
On February 22, 2023, Alvaria sent out data breach letters to all individuals whose information was compromised as a result of the recent data security incident.
Alvaria, Inc. is a business software company based in Westford, Massachusetts. The company was recently formed through the merger of Aspect Software and Noble Systems, two companies that offered a variety of Customer Experience (CX) and Workforce Engagement solutions. Alvaria creates software that enables companies to better understand and track the customer experience, as well as workforce engagement. Alvaria employs more than 2,000 people and generates approximately $423 million in annual revenue.
See more »
DISCLAIMER: Because of the generality of this update, the information provided herein may not be applicable in all situations and should not be acted upon without specific legal advice based on particular situations.
© Console and Associates, P.C. | Attorney Advertising
Refine your interests »
Back to Top
Explore 2023 Readers’ Choice Awards
Copyright © JD Supra, LLC
Category: Uncategorized
-
Alvaria, Inc. Announces Data Breach Following Hive Ransomware … – JD Supra
-
Hackers Breach U.S. Marshals System With Sensitive Personal Data – The New York Times
Advertisement
Supported by
The compromised computer system includes information on both investigative targets and agency employees.
Send any friend a story
As a subscriber, you have 10 gift articles to give each month. Anyone can read what you share.
Glenn Thrush and
The U.S. Marshals Service suffered a major security breach this month when hackers broke into and stole data from a computer system that included a trove of personal information about investigative targets and agency employees, a spokesman for the service said on Monday.
The service, a division of the Justice Department, is responsible for the protection of judges, the transportation of federal prisoners and the operation of the federal witness protection program. The witness protection database was not breached, but hackers did gain access to information about some fugitives sought by federal authorities, according to a senior law enforcement official.
Justice Department officials have determined that the breach, which was carried out through ransomware on Feb. 17, was “a major incident,” said Drew J. Wade, the Marshals Service spokesman. It was yet another in a series of breaches that have underscored the government’s struggles to protect sensitive information as the frequency, scale and sophistication of ransomware attacks have surged in recent years.
The affected system “contains law enforcement sensitive information, including returns from legal process, administrative information and personally identifiable information pertaining to subjects of U.S.M.S. investigations, third parties and certain U.S.M.S. employees,” Mr. Wade said in an email. Officials with the Marshals Service disconnected the system after discovering the attack, he said.
The department is investigating the origin of the attack and working on an assessment of the damage while officials with the Marshals Service race to limit the risk posed by the theft of the highly sensitive personal and investigative information.
The breach was reported earlier by NBC News.
Several government agencies have fallen victim to hackers in recent years, as a growing number of groups have acquired the tools and expertise to steal data, disrupt critical infrastructure and extort payments from victims that also include corporations and private individuals.
A highly sophisticated Russian hacking attack during the final year of the Trump administration compromised the networks of more than 250 federal agencies and businesses — including the Treasury, State, Commerce and Energy Departments, and parts of the Pentagon.
A spate of hacks of government computers in 2015 that originated in China stole the personal information of about 21.5 million people, including addresses, health and financial history, and other private details, from people who had been subjected to a government background check. The hackers also took the personnel data and fingerprints of federal employees.
A number of other, smaller data breaches have targeted groups related to the federal government, including the theft by Chinese government hackers of sensitive data from a Navy contractor in 2018 and the theft in 2019 of tens of thousands of images of travelers and license plates stored by Customs and Border Protection.
The Biden administration has made combating ransomware a national security priority, and has succeeded in recovering ransoms, thwarting extortion attempts and dismantling criminal organizations that engage in ransomware attacks.
Advertisement -
EU Parliament bans staff from using TikTok over ‘cybersecurity concerns’ – POLITICO Europe
In-depth reporting, data and actionable intelligence for policy professionals – all in one place.
MEPs and assistants are ‘strongly recommended’ to delete the social media app.
The European Parliament on Tuesday banned the use of social media app TikTok on staff devices and recommended that MEPs delete it from their phones.
Following in the footsteps of the European Commission and Council of the EU, Parliament President Roberta Metsola and Secretary-General Alessandro Chiocchetti have told about 8,000 officials they should uninstall TikTok from corporate devices such as mobiles and tablets by March 20.
It is also “strongly recommended” that MEPs and their staff and accredited assistants remove TikTok from their personal devices, according to the note. The popular video-sharing app is owned by Chinese tech firm ByteDance and has become the focus of mounting security and data protection fears.
“Cybersecurity concerns have been raised on the usage of the social media platform TikTok, in particular regarding data protection and collection of data by third parties,” reads the Parliament’s email, sent out to staffers on Tuesday.
“I think it is logical and important that the Parliament joins the other European institutions on this,” said Dita Charanzová, the vice president in charge of cybersecurity.
There is no active official European Parliament account on TikTok, although one account with the handle @europarl posted a video about the institution in late 2019. A spokesperson said that the @europarl account was not official and that a procedure to have it removed by TikTok had been launched. Some of the political groups, such as the center-right European People’s Party and The Left, maintain a presence on the platform.
A TikTok spokesperson said the suspension was misguided and based on misconceptions.
“TikTok is enjoyed by 125 million EU citizens and potentially depriving users” of “access to their representatives is a self-defeating step, especially in our shared fight against misinformation and when this action is being taken on the basis of fears rather than facts,” a spokesperson said in a statement. “We repeat our calls to EU institutions for due process and equal treatment.”
Pedro López, the spokesperson of the EPP group, said the group had no plans to remove its TikTok account, which has 50,000 followers — far larger than the next-highest group, The Left, which has around 6,000.
“We will not erase our account on TikTok,” López said, adding that they had not received any official news of the decision yet.
“I think it is absurd to abandon the highest-growing social network in Europe, even if the Chinese are using it for spying,” the EPP spokesperson said.
He added that the Parliament should launch an official TikTok account because it is a useful tool to fight fake news and that the institution was instructed to do so a few months ago by the so-called bureau, the group of vice presidents chaired by President Metsola.
The Commission was the first EU institution to take such a measure, but it ruffled the feathers of other EU bodies, including the Parliament, by going it alone.
A spokesperson for Parliament Vice President Marc Angel said he regretted “that the [European Commission] made a unilateral decision on banning TikTok. As it concerns cybersecurity, he would have preferred a coordinated decision by the institution.”
This article has been updated with TikTok’s comment and a comment from a Parliament spokesperson.
Log in to access content and manage your profile. If you do not have an account you can register here.Forgot your password?
By logging in, you confirm acceptance of our POLITICO Privacy Policy. -
How to Prepare for a Data Breach before it Happens – Security Boulevard
The Home of the Security Bloggers Network
Home » Security Bloggers Network »
Preparation is key in preventing the worst outcomes from a data breach, so it is important to have a plan in place ahead of time. Here are some steps you can take to prepare for a potential data breach: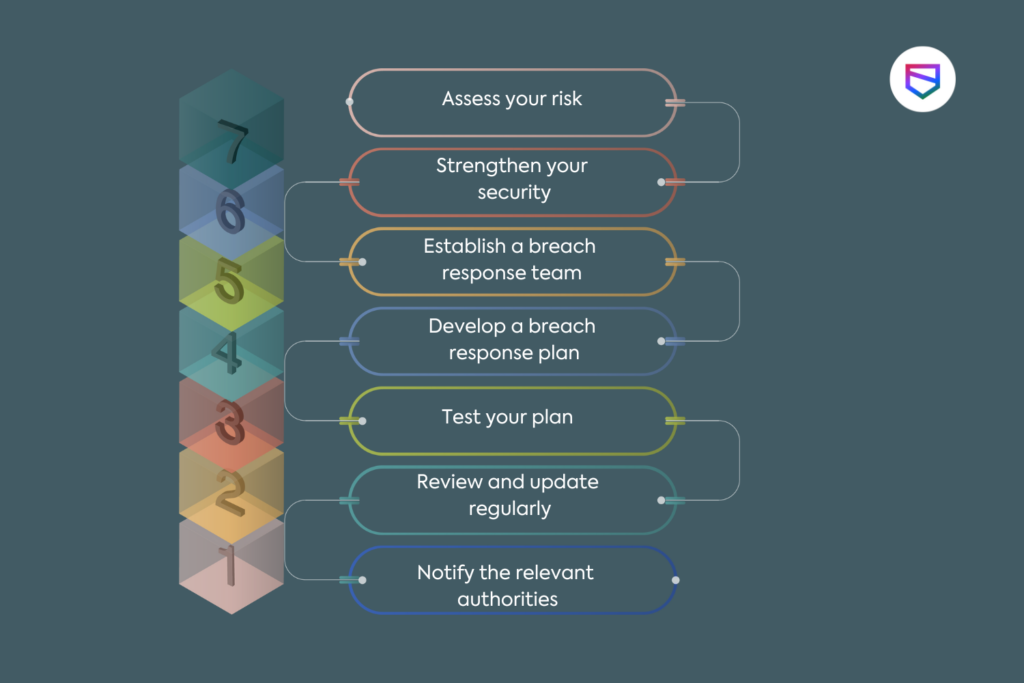
By taking these steps, you will be better prepared to respond to a data breach if it occurs, and you may be able to prevent it from happening in the first place.
When a data breach occurs, it is important to respond quickly and effectively to minimize the damage and protect sensitive information. Here are some strategies for responding to a data breach:
It is important to remember that the steps taken during a breach response can have long-term consequences, so it is crucial to act quickly and effectively to minimize damage and protect sensitive information.
Data breach responses can be successful or unsuccessful. The first step to effectively responding is having a plan ready in advance, as well as resources available when you need them. Not having a plan will lead to extended problems and increased costs of incident response. Here are several real life examples of successful data breach response efforts:
The recent news about the Chinese hackers who stole information from hundreds of companies has been all over the news, but not everyone is aware that many other similar cyber attacks on large organizations preceded this attack. In some cases, as in the case of McAfee and its employees, after being hacked they paid a $100m ransom in bitcoins to obtain back their stolen data. Unfortunately, we are still far away from having a real-time electronic defense that can ensure 100% protection against such attacks. Even if these attacks were detected earlier than they actually happened, it would take an extended period of time for their damage to be fully assessed or mitigated. In other words, cyber security awareness at all levels will always be an issue that requires serious attention so it does not happen again in the future.
Unlike other security threats, data breaches are not always immediately obvious. In many cases companies don’t know they’ve been breached until well after the fact. Effective responses to these incidents can be difficult to predict, but there are a few key things that successful companies have in common. Data breaches are not a new phenomenon. They have been around for decades, and they continue to grow in number and severity. While no two data breaches are the same, there are several commonalities that can help predict how successful your company’s response will be.
Assumed Breach Assessment Case Study: Uncovering WeSecureApp’s Approach
Automation and Scalability in Red Team Assessments
Don’t Leave Your Security to Chance: The Importance of Zero Security
The post How to Prepare for a Data Breach before it Happens appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Naimisha. Read the original post at: https://wesecureapp.com/blog/how-to-prepare-for-a-data-breach-before-it-happens/
More Webinars

-
Top 5 security improvements to protect against public sector … – Open Access Government
The solution to reducing public sector cybercrime lies in finding trusted experts, like Firstserv, to provide managed solutions and secure cloud hosting including disaster recovery, managed backups, and server monitoring.
Public sector cybercrime has been particularly dramatic over the last year. The digital skills gap, home working, multiple device access and a lack of cyber awareness in employees have all contributed to increased cyber risk. Due to its size, the number of systems utilised, numerous locations and the number of employees, the NHS is particularly vulnerable. In January this year, Firstserv rescued an NHS Foundation Trust after their skills gap left them defenceless.
In December 2021, the Trust had a robust Intrusion Detection and Prevention System (IDS/IPS) solution installed, but it was never used. The in-house IT team lacked the skills to onboard the key infrastructure configuration.
With the system sitting dormant, the Trust was unable to identify attacks and techniques. Their employees were not knowledgeable enough to spot them.
It was a high-risk situation, as malicious traffic could go undetected leading to attacks.
The costs are threefold and often underestimated. Resolving the issue once the attack has happened is expensive. Preventative measures in the form of server monitoring and other managed solutions are more budget-friendly.
Depending on the type of breach, General Data Protection Regulation’s (GDPR) non-compliance fines can be up to €10 million, or 2% annual global turnover – whichever is greater; or up to €20 million, or 4% annual global turnover – whichever is greater.
“Each individual cyber-attack is estimated to cost an average of between £4,200 to £19,400 and that doesn’t include potential fines for not protecting data efficiently.”
In addition to this, the reputational damage that results from a serious data breach can be crippling.
At the end of January, this year, the Trust suffered from a Distributed Denial-of-Service (DDoS) attack on its main trust server. Without the necessary knowledge and skills to protect themselves, they were powerless to stop it and contacted Firstserv for help.
The immediate corrective action taken to mitigate the attack was to increase resources on the main firewall. Once this was done, the existing IDS/IPS solution was properly configured to prevent future attacks.
Firstserv is continuing to work with the NHS Foundation Trust’s IT department to build its in-house cyber security skills and awareness. This will enable it to take a more active role in owning its own security posture, ensuring it continues to make full use of its Cloud infrastructure.
Due to its internal skills gap, the Trust is also looking to implement Firstserv’s High Availability Solution and outsource management of servers and system infrastructure to the expertise of the Firstserv team.
So, how can you mitigate the risks? Firstserv’s CEO, Sebastian, shares the Top 5 ways to fight public sector cybercrime:
Cloud security provides multiple levels of control within a network infrastructure. It gives you continuity and protection for cloud-based assets like websites and web applications. Businesses need to ensure their chosen cloud security provider provides DDoS protection, high availability, data security, and regulatory compliance.
Keep your business operating without interruption as your IT security staff deals with vulnerabilities and cyberattacks. By providing multiple paths for traffic, any downtime you suffer won’t leave data vulnerable.
The issue can be isolated and resolved far more efficiently. It is essential to maintain redundancy for cybersecurity and successful compliance audits.
The digital skills gap and lack of cyber awareness among employees make them key targets for attackers. Strategies include phishing scams and malware-containing emails.
By decentralising your network and segmenting it into smaller, sub-networks you add an extra layer of protection for your organisation. Even if a hacker successfully breaks into one segment of the network, they won’t be able to access everything. The threat can be isolated and successfully removed.
To ensure cyber resilience, all platforms and data hosted in the cloud should have fine-tuned access restrictions. Firstserv can provide you with easy-to- configure control and tools including:
No cyber security strategy can provide 100% protection which is why Firstserv offers robust 24/7 monitoring of your hardware and software. Hackers are more sophisticated with each day, and this threat can never be eliminated but a proactive monitoring solution is crucial to reduce your vulnerability.
We need a cyber-resilient public sector. If you need help to ensure your protection is good enough, email Sebastian Tyc at Firstserv on styc@firstserv.com.
Sebastian Tyc is Firstserv’s Managing Director, ensuring their high availability solution is made available to all public sector organisations.
-
Multi-agency operation leads to nine cyber crime arrests in San Angelo – MyFoxZone.com KIDY
SAN ANGELO, Texas — The Abilene Police Department Cyber Crimes Unit assisted the Department of Homeland Security office in San Angelo in the arrest of nine individuals from various locations for crimes against children.
The multi-agency operation that included the Texas Department of Public Safety, the Federal Bureau of Investigation, the U.S. Air Force and other area law enforcement agencies, targeted suspects seeking to engage in sexual contact with minors in the San Angelo area.
According to a APD press release, the two-day operation is the type of operation that the Abilene Cyber Crimes Unit assists with on a regular basis. These operations seeks to bring to justice individuals who target the most vulnerable population through the internet and social media applications.
Next up in 5
Example video title will go here for this videoIn Other News
Notifications can be turned off anytime in the browser settings. -
Emtec, Inc. Reports Data Breach Affecting Over 7,000 People … – JD Supra
On February 21, 2023, Emtec, Inc. filed notice of a data breach with several state attorney general offices, including those in Maine and Texas, after determining that confidential consumer information was leaked following a cyberattack. Based on the company’s official filing, the incident resulted in an unauthorized party gaining access to consumers’ names, addresses, Social Security numbers, driver’s license numbers, financial account information and protected health information. After confirming that consumer data was leaked, Emtec began sending out data breach notification letters to the 7,637 individuals who were impacted by the recent data security incident.
If you were an employee or contractor who did business with Emtec, the recent data breach may have resulted in your personal information being exposed to potential criminals. As we’ve discussed in prior posts, data breaches like these dramatically increase your risk of identity theft and other frauds. Therefore, as a data breach victim, it is important you understand what you can do to mitigate these risks. Depending on the outcome of the pending investigation into the Emtec breach, you may also be able to hold the company accountable for its role in leaking your information.
The available information regarding the Emtec breach comes from the company’s filings with the attorney general offices in Maine and Texas. According to these sources, Emtec recently learned of a possible cyberattack. While the company did not provide the exact date it learned of the potential intrusion, in response, the company worked with law enforcement and a third-party forensics firm to determine the nature and scope of the incident.
On January 17, 2023, the Emtec investigation confirmed that an unauthorized party had gained access to the company’s computer network on September 7, 2022, which was terminated on September 14, 2022. It was also determined that some of the files that were accessible to the unauthorized party contained confidential consumer information.
Upon discovering that sensitive consumer data was made available to an unauthorized party, Emtec began to review the affected files to determine what information was compromised and which consumers were impacted. While the breached information varies depending on the individual, it may include your name, address, Social Security number, driver’s license number, financial account information and protected health information.
On February 17, 2023, Emtec sent out data breach letters to all individuals whose information was compromised as a result of the recent data security incident. In total, the Emtec data breach affected 7,637 individuals.
Emtec, Inc. is an IT consulting firm based in Jacksonville, Florida. The company provides a wide range of services, including strategy, planning and process improvements; marketing analytics; customer experience improvement; digital strategy consulting; cybersecurity; Oracle consulting and Salesforce consulting. Emtec operates locations in Florida, Alabama, Illinois, Pennsylvania, Toronto, Ontario and India. Emtec employs more than 1,000 people and generates approximately $204 million in annual revenue.
See more »
DISCLAIMER: Because of the generality of this update, the information provided herein may not be applicable in all situations and should not be acted upon without specific legal advice based on particular situations.
© Console and Associates, P.C. | Attorney Advertising
Refine your interests »
Back to Top
Explore 2023 Readers’ Choice Awards
Copyright © JD Supra, LLC -
Australia to establish new coordinator to fight cybercriminals – 9News
Coupons: All the latest trending fashion deals
© 2023 Nine Entertainment Co. -
Cybersecurity Courses Ramp Up Amid Shortage of Professionals – Claims Journal
DENVER (AP) — The pressure was on. Someone, somewhere, was attacking computer systems so customers couldn’t reach certain websites. In a windowless room in Denver, Zack Privette had worked all morning with his security team to figure out what the cyber strangers were up to.
“What’s happened is that we have an attacker who has been going through our different websites and they found a vulnerability into our active directory and .,” Privette explained to Richard Mac Namee, identified as chief operating officer of the company under attack.
“OK, I’m not technical. What does that mean?” interrupted Mac Namee, who is really the director of the new Cybersecurity Center at Metropolitan State University of Denver. And he’s actually quite technical.
This was a simulation.
The makeshift “Cyber Range” command center inside MSU Denver’s Cybersecurity Center had multiple TV screens showing ominous maps of live cyber threats. It’s part of a unique training ground for students, recent grads and people who don’t even attend the college but are interested in cybersecurity careers.
Privette, who isn’t an MSU student, got to experience the Cyber Range program because it’s open to outsiders. The industry needs more outsiders. According to one estimate, there are 66 cybersecurity professionals for every 100 job openings nationwide. It’s tighter in Colorado, where there are 59 for every 100. And demand is growing faster than training programs like MSU can graduate.
Mac Namee is behind the school’s Cybersecurity Center and getting the school designated as a National Centers of Academic Excellence in Cyber Defense in March. A former commander in the United Kingdom’s Special Forces who’s worked as a specialist in counterterrorism, Mac Namee keeps it practical. During the simulation, he pretends to be an ordinary company executive. Students must figure out how to explain the cyber mayhem to non-techies — and fast!
“It is a giant database that … holds their DNS server. And what a DNS server does is when you type in Google.com, it will change that to the IP address that the computer actually reads. That went down, which is why people are not able to access websites correctly,” Privette told Mac Namee. “That was down at 3:30:29. We have since brought it back up at 3:44.”
“So, 14 minutes of outage,” Mac Namee said. “Fourteen minutes with our athletes and the way they’re trying to log on, that’s quite a big problem. How will we resolve this?”
Privette went on to explain that there was a backup so the data is safe. But he acknowledged the attackers were still inside the system and his team was now trying to figure out if data had been stolen. His team thinks credentials were taken, but he doesn’t think the theft involved customers’ personally identifiable data, he said. Mac Namee gave him an hour to figure it out.
Targeted training programs have been popping up nationwide for the past decade as nearly every business with a website, ecommerce offering or other internet-based operation must deal with data breaches, ransomware and other cyber threats.
According to the Identity Theft Resource Center, which tracks breaches and supports victims, the number of publicly reported data breaches in the U.S. more than doubled since 2015 to 1,862 last year. Regulations in Colorado and around the globe also put the onus on companies to protect customers’ personal data.
Back in 1999, partly to address the lack of qualified professionals, the U.S. National Security Agency launched its National Centers of Academic Excellence program. It certifies schools with a cybersecurity curriculum for cyber research, defense education and cyber operations. There are now about 380 colleges and universities in the U.S. Such designations require standardized cybersecurity curriculum, active challenges and professional development. There are 13 schools in Colorado and include state, community and private colleges.
The partnership with industry and MSU Denver is credited to Mac Namee, said Steve Beaty, a professor in the school’s computer science department. While Beaty started teaching cybersecurity courses in 2004, a cybersecurity degree debuted just four years ago. The new center and partnerships with private cybersecurity companies such as Atos, a European information technology firm that is now taking up space in the facility, really took off after Mac Namee arrived.
“He had the bandwidth. Some of us haven’t had the bandwidth to do a lot of this stuff. Atos is due to him,” Beaty said. “Richard is the one who put the fire under what’s going on here.”
And looking at the heat map of cybersecurity job openings at CyberSeek.org, the U.S. needs it.
In the past 12 months, 714,548 cybersecurity jobs were posted in the U.S. according to EMSI Burning Glass, a firm that analyzes job openings and labor data. EMSI partnered with the Computing Technology Industry Association (CompTIA) and the National Initiative for Cybersecurity Education on the CyberSeek effort to document the need for more trained workers. Colorado, among the top 10 states with the most openings, had 25,761 as of April.
“The field is just growing so fast that even if we churn out many graduates, which we have seen a significant uptick in, it still often doesn’t keep pace with the growth in demand,” said Will Markow, an EMSI Burning Glass cybersecurity expert. “We’ve seen about a 40%-50% increase in the number of graduates from cybersecurity programs across the country. The problem is that during the same timeframe, demand for cybersecurity workers grew about twice that rate.”
The industry has a number of unique issues that compound the shortage, Markow said. New threats erupt all the time, so the industry is constantly scrambling. Workers need a mix of different IT skill sets plus credentials, some that require years of experience. That makes it difficult for those starting out who have no experience.
“Employers are also not offering many opportunities for people who either don’t have a bachelor’s degree or who don’t have at least three to five years of prior work experience,” Markow said. “What that means is that there aren’t many entry level opportunities (and that) presents a unique challenge for building the pipeline of cybersecurity workers.”
Cybersecurity jobs stay open 20% longer than other tech jobs, which are already notoriously hard to fill, he added. And because of the required degrees and certifications, the jobs pay about $15,000 more compared to other IT jobs.
Government agencies are more open to hiring skilled workers without college backgrounds. That’s true with the state Governor’s Office of Information Technology. A paid apprenticeship for veterans requires “some IT experience but no degree,” said Ray Yepes, Colorado’s chief information security officer.
“It’s also worth noting that for the majority of OIT positions we will accept years of experience as a substitute for education,” Yates said in an email.
With the growth of college programs, boot camps and other training programs, Markow said that it’s up to companies to adjust hiring requirements if they really want to fill openings and feed their own talent pipeline.
“I think that really the question is whether employers are going to be receptive (and) hire those workers,” he said. “They’re learning the right skills for cybersecurity. What we need are employers to also recognize that they need to take more of a skills-based lens towards recruiting cybersecurity workers as opposed to a credential- or experience-based lens which they have done historically.”
While security simulations were happening in one part of the room at MSU Denver, in another, Nathan Shelley was at work. Literally. The recent MSU graduate with a Bachelor of Science in cybersecurity was hired by Atos as an intern just before his December graduation. He became a full-time employee May 30. Atos is a massive European IT firm based in Paris.
“We monitor public-sector clouds,” said Shelley, who grew up in Estes Park and was drawn to MSU Denver because of its new cybersecurity degree. “We are responsible for monitoring log traffic and determining if there are false positives or true positives.”
Shelley was monitoring computer systems of actual government agencies that hire Atos to make sure what is stored in the internet cloud isn’t being compromised. Security analysts like Shelley spend hours watching the online activity and thanks to artificial intelligence and monitoring tools, they get alerts when something is awry and must determine if the issue is real.
That may not seem very exciting but a cheery Shelley speaks enthusiastically about his gig, which includes plugging holes discovered only after software was released. In other words, bugs born on day zero that online mischief makers are constantly hunting for.
“Probably the most active that I’ve been this week was yesterday when we were patching for a recently discovered CVE, that is a vulnerability with Follina, it’s a proliferating, zero-day exploit,” he said. “This is very widespread for the Microsoft environment. It’s an Office 365 zero-day vulnerability so that means (the software) was released with the vulnerability. It’s now flaring up in the cybersecurity realm. It allows remote code execution and that can be done through a certain domain.”
Microsoft had not yet issued a fix for Follina, named after an Italian village with a postal code that was found in the exploit.
The MSU Cybersecurity Center is a resource for others, too. Helping potential IT workers get hired is the mission of ActivateWork, a nonprofit IT recruiting and training organization that connects employers to the overlooked talent.
“We believe the traditional hiring process leaves extremely valuable talent out. We help employers solve talent gaps by finding underrepresented candidates and preparing them to excel in new careers,” said Susan Hobson, the nonprofit’s director of apprenticeships and evaluation.
Its first-ever 15-week security fundamentals course culminated last week with MSU Denver’s Cyber Range simulation. Hobson said ActivateWork focuses on the workforce employers need.
“We know that cybersecurity has a gap, especially here in the Denver area,” she said. “If you look at local area labor data, there were 13,000 open cybersecurity jobs as of March this year. We knew the need was there and we drive our course offerings based on local employer needs.”
ActivateWork’s learners aren’t typical students. Most don’t have a college credential. Many are unemployed or are looking for a better job in IT. The recent cohort of security fundamentals graduates left with CompTIA A+ certification and over 100 hours of soft skills and life skills training including resume reviews, interview prep and financial capability training. After graduation, ActivateWork helps them find a job in the field and coaches them for 12 months as they transition into a career.
The organization also has a registered apprenticeship program with the U.S. Department of Labor and works with area employers to hire graduates from their boot camps. Three of the 20 graduates start cybersecurity apprenticeships this month, and ActivateWork is always looking for more companies to partner with to build a talent pipeline in cybersecurity.
“They’re struggling to hire because they’re looking for individuals with three to five years of experience,” Hobson said. “This is a way to equip talent through 12-months of on-the-job learning with the exact skills an employer needs.”
Privette, who was part of the MSU Denver cybersecurity simulation, stopped the bug from wreaking more havoc. They brought back the websites and, well, he hopes he continues to keep learning more. He is very excited to start his ActivateWork cybersecurity apprenticeship on Monday as an information security analyst.
“I’ve been wanting to get into this since high school and I feel like ActivateWork has really given me the opportunity to pursue it,” said Privette, an electrician until he fell from the ceiling at one client location. “I didn’t have the money to afford college. And then I didn’t really realize the path to get to it (cybersecurity). I didn’t want to be an electrician forever. Falling through the ceiling gave me the opportunity to pursue this.”
About the photo: Sam Madison, front, is quizzed by Richard Mac Namee, back right, director of the Cyber Security Center at Metropolitan State University of Denver, and Klaus Streicher, back left, a graduate of the program, during a cybersecurity training exercise, Wednesday, June 1, 2022, in Denver, hosted by the school to help interest potential students who may want to pursue careers in field. (Tamara Chuang/The Colorado Sun via AP)
Was this article valuable?
Thank you! Please tell us what we can do to improve this article.
Thank you! % of people found this article valuable. Please tell us what you liked about it.
Here are more articles you may enjoy.
Get the latest insurance news
sent straight to your inbox.
Your email address will not be published. Required fields are marked *
*
*
We have updated our privacy policy to be more clear and meet the new requirements of the GDPR. By continuing to use our site, you accept our revised Privacy Policy.