Obtenga más información sobre los incidentes de seguridad más importantes que
surgieron en 2021 y cómo reforzar sus defensas.
By Mayra Rosario Fuentes
A look into the cybercriminal gender gap, the status and perceptions on gender profiles in the underground, and the role assumptions have for law enforcement.
With the anonymity of cybercrime and the groups behind them, gender plays a much less important role than in other online communities. In many ways, it is one of the most meritocratic communities online, where developers are valued for their skills and experience, and not necessarily for their gender when it comes to conducting business in the underground. In this research paper, we will show that while female cybercriminals are (still) in the minority, they most certainly do exist, and an investigator should be open to this possibility from the start.
It is generally accepted that most cybercriminals are male. Following law enforcement bulletins and media reports, it is more common to hear investigators use the terms “he” or “him” when referring to a cybercriminal that has yet to be attributed. In Trend Micro, research teams have had a long-standing policy of using “them” or “they” to refer to threat actors, long before this became more common in gender discussions. At the minimum, this allows for the hacker handles discovered to be observed or thought of being operated by a group. But looking at this usage from a bigger picture, we found that this practice removes gender bias — an unconscious tendency that we strongly believe can lead an investigator down the wrong path. Gender bias, whether explicit or implicit, can severely undermine a criminal investigation. In many cases, investigating and interviewing a female suspect requires a different mindset.
Gender is one of the important factors in dealing with different kinds of crimes. For women, there is not one dominant path that leads them to commit or be involved in criminal activities. According to an Inquiries Journal article, consistent research findings over the years from criminologists, legal scholars, and sociologists have found that men and women differ in criminal behavior and sentences received, resulting in a “gender gap” in criminality rates and prison populations. The same study also cites that the crimes most often committed by women are non-violent and carry milder sentences. On comparing past and current situations, we observed that the cybercriminal underground economy was less accepting of those who identified as women then, based on discussions in forums. Over the last few years, however, gender has been discussed less when it comes to business.
Different theories exist regarding the general lack of women’s involvement in cybercrime, including the lower numbers of women engaging with online forum communities and the gap in internet access. According to a study conducted by the World Wide Web Foundation in 2020, women are less likely to create online content, comment, or post about political events when they get online, and 29% are more likely to sell or advertise a product. Another theory is the product of having low numbers of women practicing in cybersecurity as part of the workforce as cybercrime offenses are usually technical in nature. Technical offenses require a particular skillset or knowledge about computer systems. Cybersecurity Ventures predicts women will represent 30% of the global cybersecurity workforce by 2025, and up to 35% by 2031. The report mentioned that as of 2021, women held 25% of cybersecurity jobs globally, reflecting an annual increase of female practitioners even on average. It is important that we understand the relationships between gender and cybercrime to understand the issues investigators can and will face later: Cybercrime is not gender-neutral.
For the purposes of this research, cybercrime is defined by and limited to the different types of incidents and activities such as gaining unauthorized access to a computer system with a criminal motive, fraud, money laundering, denial of service attacks, ransomware attacks, identity theft, cryptocurrency mining, and the development and supply of malware. We predominantly focus on cyber-dependent crime while also looking at some cyber-enabled crimes. We will not investigate interpersonal cybercrime offenses such as harassment, child sexual exploitation, and stalking.
It is important to mention that while carrying out this research, we made every effort to consider the wider definition of gender to include non-cisgender (to note, cisgender denotes a person whose biological sex and gender identity match) profiles. However, as will be shown throughout the study, specific profiles on a technical-level are also difficult to ascertain from the anonymous community that cybercrime represents. With some exceptions where this was possible, most of our commentary will refer to male and female gender profiles simply as that is what the data presented. On this theme, we encourage the security community to explore this further should other techniques become available later on.
In cybercrime, gender influences peoples’ different experiences and shapes their roles among cybercriminal groups or hackers. Online cybercrime patterns mimic the offline world. Due to the lack of readily available national cybercrime arrest data, we looked at the overall incarceration data for both men and women in the United Kingdom, US, and Russia. The data was compiled from the World Prison Brief, an online database providing free access to information on prison systems around the world, hosted by the Institute for Crime & Justice Policy Research at Birkbeck, University of London.
The rate at which women are incarcerated varies greatly by country, but overall still account for less than 10%. Women are accused and convicted of less serious crimes and are less likely to be incarcerated compared to their male criminal counterparts. Today, the number of women committing crimes is on the rise globally. A 2017 report by the Institute for Criminal Policy Research at Birkbeck, University of London, showed that the global female prison population has surged by more than half since the turn of the century, while the male prison population increased by just a fifth over that same period. In the US alone, women made up only 6.8% of the prison population in the first half of 2022. In the United States, women commit more drug and property offenses, making up more than half of the offenses for which women are incarcerated.
It is widely assumed that most cybercriminals are male. Over time, however, female cybercriminals have been making their presence known. In underground cybercriminal forums, jobs for women include roles as money mules and for money laundering purposes.
In Russia, women make up 8% of the total prison inmate population. The country has one of the highest incarceration rates in Europe, reaching over 356 prisoners per 100,000 of their population in 2020. Most criminal offenses in the country were considered “crimes of little gravity” (that is, minor crimes borne of negligence), while the share of “grave crimes” stood at approximately 6%.
In 2021, there were approximately 75,000 males and almost 3,200 women prison inmates in England and Wales, with females accounting for 4% of the total prison population. TV license evasion was the most common offense for which women were convicted in 2019. Theft from shops was also the most common indictable offense committed, for which 34% of females and 14% of males were convicted in 2019.
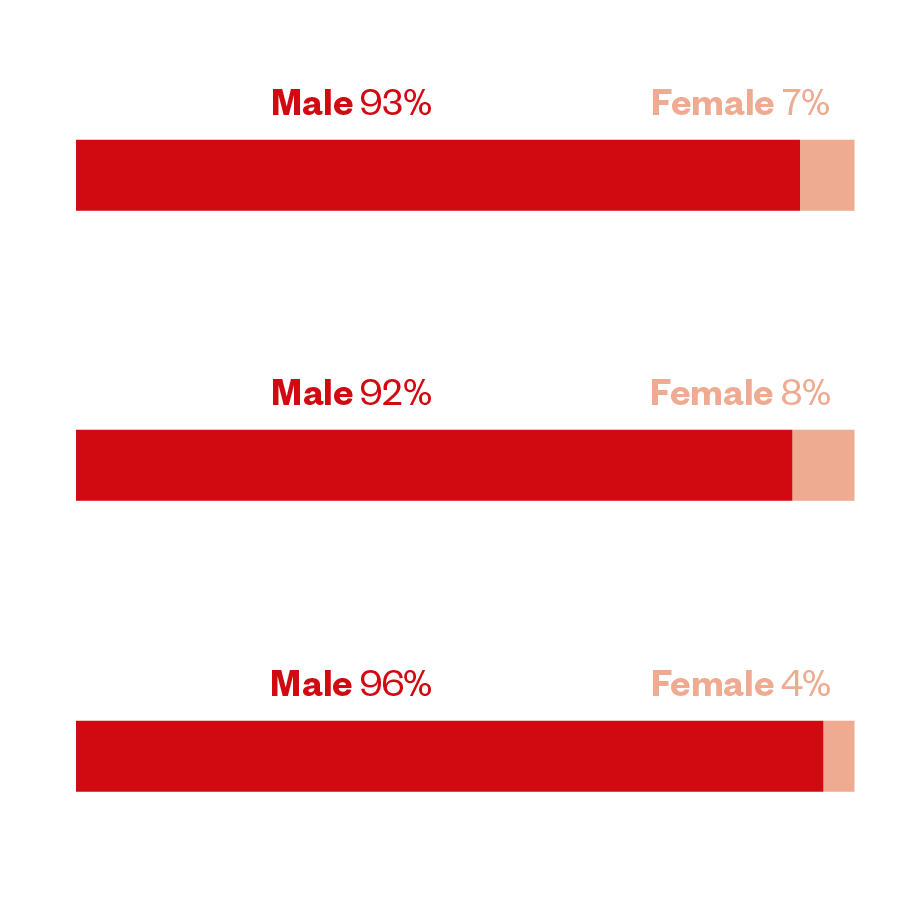
Figure 1. Male and female prison population percentage by gender (data taken from World Prison Brief)
Data from a 2020 study on women shows that men are 21% more likely to be online and use the internet globally, rising up to 52% in a gap to women in least developed countries. A lack of digital skills emerged as the biggest factor keeping women offline. Women are also less likely to create certain types of online content, compared to men being 29% more likely than women to post comments about political, social, or economic issues, and 29% more likely to sell or advertise a product or service online.
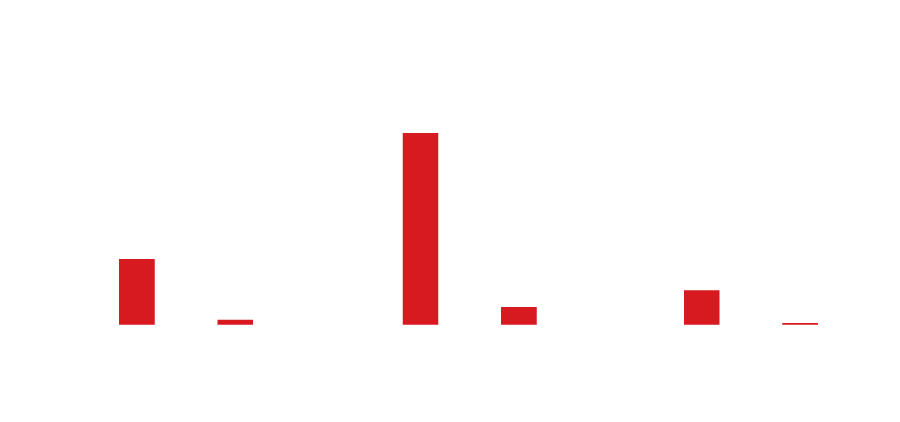
Figure 2. Prison population count by gender (data taken from World Prison Brief)
Another way gender imbalance in cybercrime can be seen and explained is due to the accessibility to formal knowledge. We have consistently seen lower numbers of female students studying STEM-based (science, technology, engineering, and mathematics) degrees than men. According to a study conducted by the International Labour Organization (ILOSTAT) in 2019, the country of Georgia had the highest share of women employed in STEM fields, with 55.6% of all those employed in STEM fields being women. In the United States, women accounted for 48% of all STEM jobs compared to the United Kingdom’s count at 40%. This is considering the already-low numbers of STEM occupations, which comprise less than 20% of employment in all 69 countries included in the study, ranging from low decimal percentages in several African countries to 15% in the US and in the UK, and 17% in Austria.
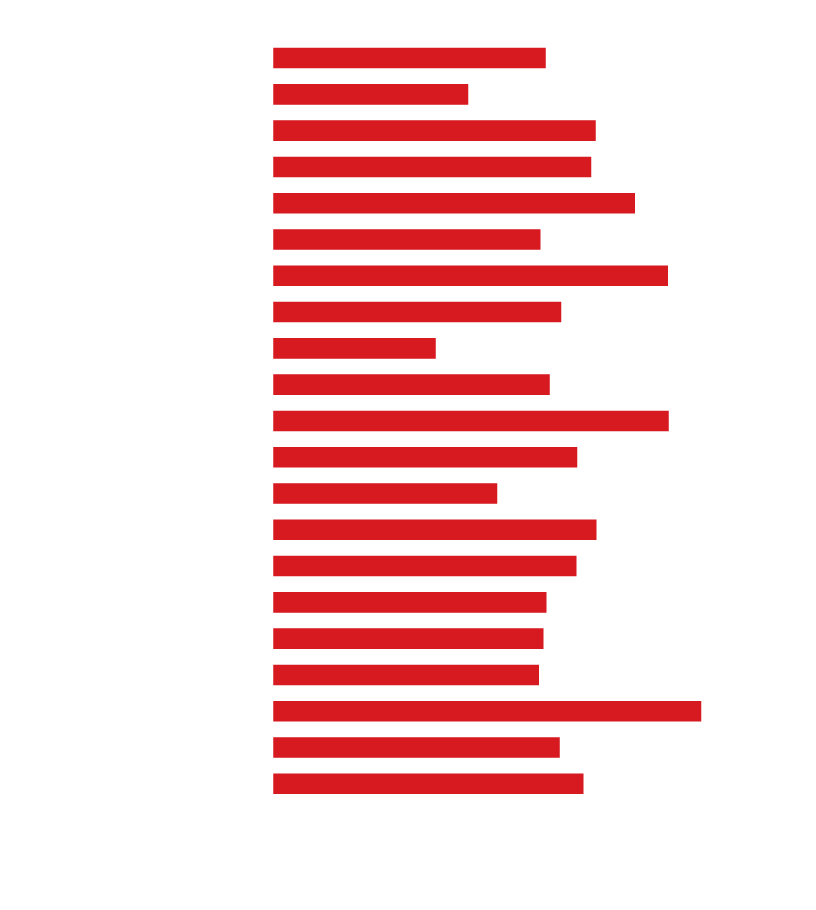
Figure 3. Percentage of women working in STEM fields in 2021 by country. Data taken from ILOSTAT.
Gender gaps such as access to the internet and mobile phones, employment, and education affect how users interact with the internet, and therefore in committing cybercrime. Women remain 7% less likely than men to own a mobile phone and are 16% even less likely to use mobile devices to access the internet. According to the International Telecommunication Union (ITU), 62% of men are using the internet, compared to 57% of women in 2022.
Given that authorities’ public identification of cybercriminals is already at a relatively low volume occurrence, identifying specifically female cybercriminal members would be even more unusual. However, when it does happen, this unusual aspect means these stories will frequently generate more media coverage than their male counterparts. Here is an overview of some of the most high-profile cases on female cybercriminals charged in recent years.
 Figure 4. Valérie Gignac. Photo courtesy of CBC News.
Figure 4. Valérie Gignac. Photo courtesy of CBC News.
In 2015, Canadian Valérie Gignac was arrested by the Royal Canadian Mounted Police for hacking computers, taking over their webcams, and spying on people. Valérie Gignac also ran the cybercriminal forum viphackforums[.]net. She was charged with four counts related to the unauthorized use of a computer and mischief in relation to computer data.
 Figure 5. Lauren Lide. Photo courtesy of Flying Magazine.
Figure 5. Lauren Lide. Photo courtesy of Flying Magazine.
Lauren Lide used to work at the Melbourne Flight Training school in Florida as a Flight Operations Manager. She quit in November 2019, the same day her father got fired from his job at the same company. In retaliation for her father being fired, the disgruntled former employee used her old boss’ login information to wipe out critical aircraft and safety data on their fleet. She was charged with two counts of unauthorized access of a computer electronic device without authority, and one count of modifying computer data programs without authority.
 Figure 6. Paige Thompson. Photo courtesy of Komo News.
Figure 6. Paige Thompson. Photo courtesy of Komo News.
Paige Thompson was a former Amazon engineer convicted in the 2019 Capital One breach. Thompson developed a tool that scanned Amazon Web Services (AWS) for misconfigured accounts to gain access to the systems of Capital One and dozens of other AWS customers. Prosecutors also say Thompson “hijacked” companies’ servers to install cryptocurrency mining software that would transfer any earnings to her wallet. Thompson was found guilty of wire fraud, five counts of unauthorized access to a protected computer, and damaging a protected computer. The jury found her not guilty of access device fraud and aggravated identity theft.
 Figure 7. Alla Witte. Photo courtesy of Tech Startups.
Figure 7. Alla Witte. Photo courtesy of Tech Startups.
55-year-old Latvian Alla Witte was charged in a US federal court with 19 counts for her role and activities in the TrickBot Group, including conspiracy to commit computer fraud and aggravated identity theft, conspiracy to commit wire and bank fraud affecting a financial institution, and conspiracy to commit money laundering, among other charges. Before her arrest in 2021, Witte worked as a malware developer and wrote code related to the control, deployment, and payment of ransomware for the group since 2015.

Figure 8. Laura Rose Carroll (left) and her daughter (right). Photo courtesy of News4Jax.
17-year-old high school student and her mother were arrested for hacking the school’s system to change the homecoming queen votes, enabling the former to win the competition in 2021. Agents with the Florida Department of Law Enforcement (FDLE) arrested the mother, former Assistant Principal Laura Rose Carroll, and daughter duo on one count each of offenses against users of computers, computer systems, computer networks, and electronic devices, unlawful use of a two-way communications device, criminal use of personally identifiable information (PII), and conspiracy. The mother was sentenced to 18 months of probation and ordered to pay court costs totaling $518.
 Figure 9. Heather “Razzlekhan” Morgan (left) and Ilya “Dutch” Lichtenstein (right). Photo courtesy of New York Post.
Figure 9. Heather “Razzlekhan” Morgan (left) and Ilya “Dutch” Lichtenstein (right). Photo courtesy of New York Post.
Husband and wife Ilya “Dutch” Lichtenstein and Heather “Razzlekhan” Morgan were arrested in February 2022 for allegedly conspiring to launder cryptocurrency stolen during the 2016 hack of virtual currency exchange Bitfinex. Law enforcement has so far seized over $3.6 billion in cryptocurrency linked to the said hack. They were charged with conspiracy to commit money laundering and conspiracy to defraud the US, which are charges punishable for up to 25 years in prison.
 Figure 10. Ruja Ignatova. Photo courtesy of BBC.
Figure 10. Ruja Ignatova. Photo courtesy of BBC.
Ruja Ignatova , known as the “missing Cryptoqueen,” is still wanted by the Federal Bureau of Investigation (FBI) for her alleged participation in a large-scale cyptocurrency fraud scheme. Ignatova was the founder of OneCoin Ltd., a Bulgaria-based company that marketed OneCoin as a purported cryptocurrency. Ignatova allegedly made false statements and representations to individual investors to solicit for OneCoin beginning in 2014, and instructed victims to transmit investment funds to OneCoin accounts to purchase OneCoin packages. The scheme caused victims to send wire transfers representing these investments, defrauding victims out of more than $4 billion in total.
To date, there have been few research on women’s participation in the cybercriminal underground. Female hackers were previously perceived with hostility by the general hacker community. If women identified themselves, users would harass them, and sometimes lower their reputation or popularity points on the forums. According to a 2021 Pew research, Americans who experienced online harassment have not increased, and that the overall prevalence of this type of abuse is the same as it was in 2017.The same report found that women are about twice as likely as men to say they have been targeted because of their gender.
But as societal norms began changing, the cybercriminal underground became less concerned about gender when conducting business. As seen in discussion boards, women would get a positive reputation because it’s not common to see female hackers in the community. With users who have yet to improve or gain points and take on female usernames, people assume the person behind the user handle is a guy pretending to be a woman to get more popularity points.
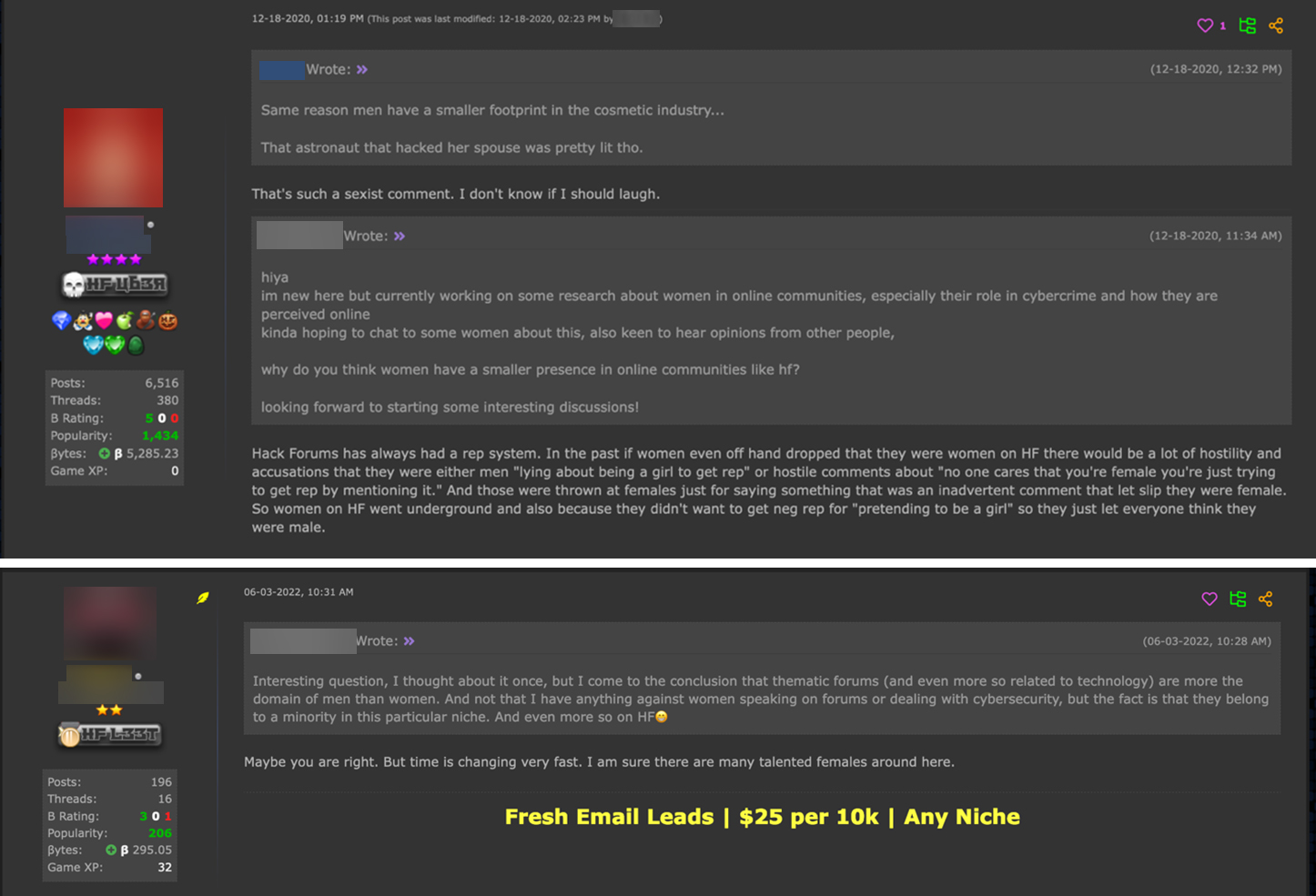
Figure 11. Discussion about past instances of women participating on hack forums wherein users were hostile toward them via the points (rep) system
Underground cybercriminal forums have rules and etiquette that prohibit harassment, bullying, and sexual harassment even though these still occur. One hacking forum, Hackforums, changed their reputation system to include a business rating. People have used reputation points to harass others, which can then affect their business since other members use it to gauge trustworthiness. Similar to the figure above, some women have discussed purposely using male pronouns to avoid harassment.
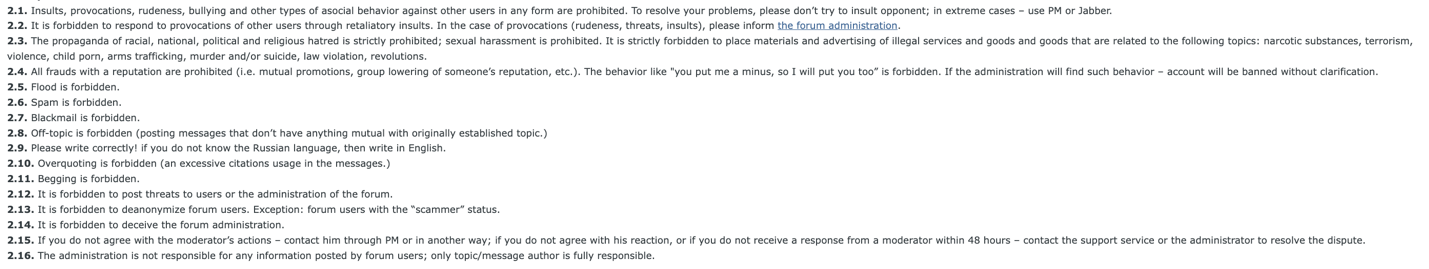
Figure 12. The “code of conduct” guidelines of a Russian language forum
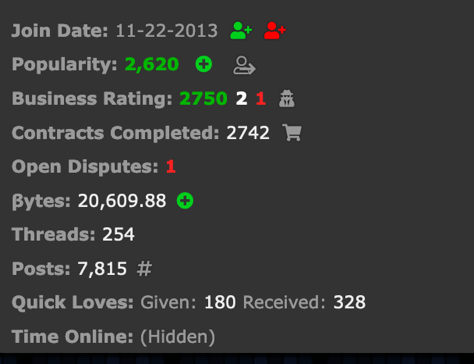
Figure 13. User profile showing reputation and business ratings
We cannot conclude that the community has become more accepting of women. Instead, it would be more accurate to say that gender is not an issue when conducting business in the underground. An example is Alla “Max” Witte, the 55-year-old woman and mother charged for her involvement with the Trickbot Group. Many in the cybercriminal gang not only knew her gender but her name as well. She was so well-liked that at one time, ransomware group Conti members were considering paying for her legal fees.
Topics about sexual orientation and genders such as LGBTQIA, female, binary, and non-binary, among others, are discussed in the underground in mostly English-speaking forums. Some users in the introduction forum section mentioned their gender though they are never required to do so in their welcome messages. We noticed a trend over the years wherein users discuss their gender and sexuality more openly than in the past. We have also seen English language forums posting with the rainbow pride flag and users celebrating Pride Month.
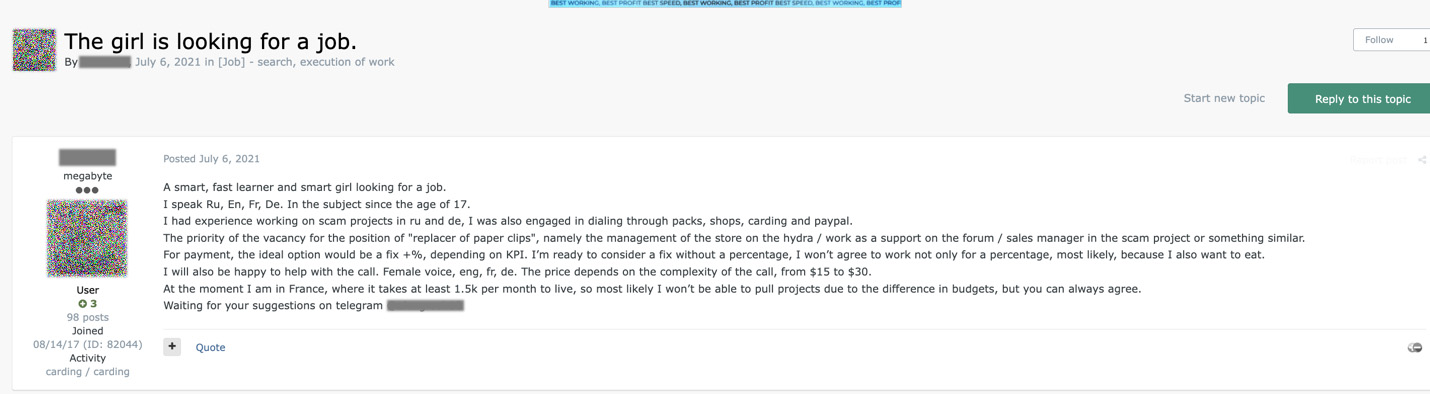
Figure 14. Forum user discussing job qualifications with their gender explicitly stated in the title
Meanwhile, Russian-based forums usually do not discuss genders or sexual orientations. This could be due to the political nature of the country where the LGBTQIA community do not have the same rights as in other countries. When these topics do appear in forums, they are often found in the non-business sections such as religion, lounge, and politics. The Russian language forum, Exploit, allows users to set their respective gender profiles, but many users leave it empty.
We found underground forums frequented by lower-level criminal actors (also known as skids, or script kiddies) discussing gender differently than other, more professional forums frequented by top-tier cybercrime actors. Many users in these lower-level communities argue over petty topics all the time and use derogatory terms to refer to each other. One example is OGUsers forum, known for selling stolen accounts and for being a community with a “lower maturity” level. Where it was possible to link these forum users to social network profiles, we noticed they behaved similarly in those communities. By comparison, gender-based derogatory comments are unusual in more professional and business-oriented communities, such as the Russian forums XSS and Exploit — it’s all about business
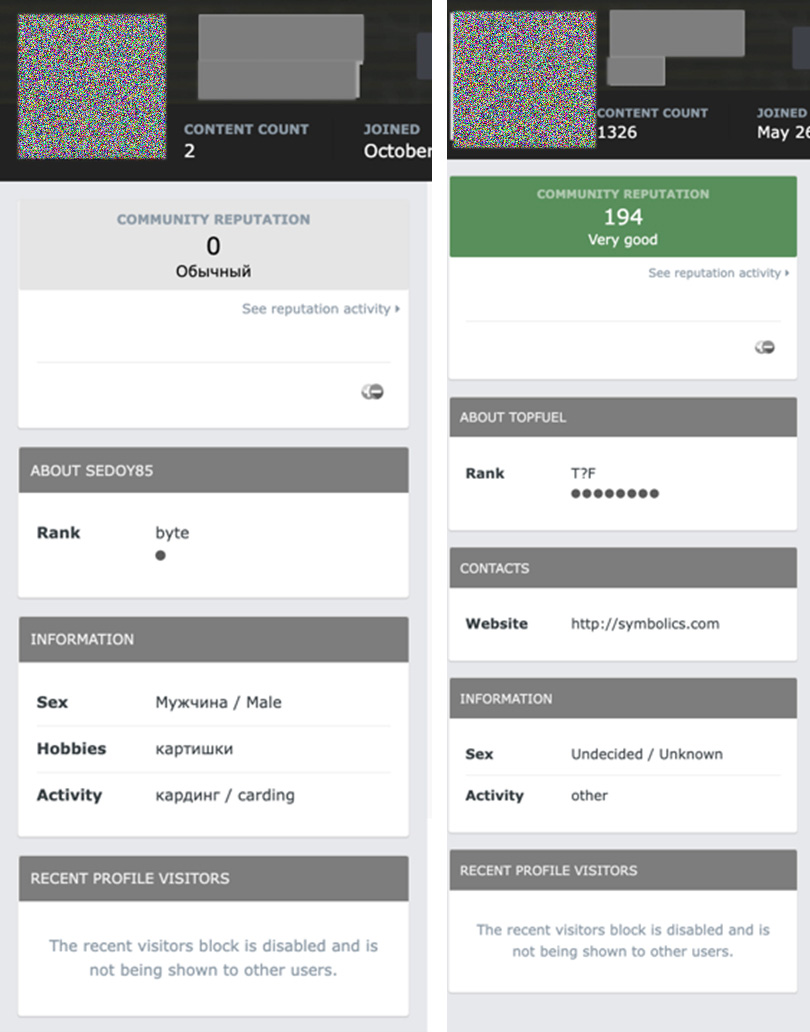
Figure 16. Exploit user profile showing their gender
The types of jobs advertised specifically for women in cybercriminal forums include muling (facilitators for drug trafficking and money laundering, among others), call center jobs, and social engineering and romance scams where voice and images are usually needed. However, most job advertisements or affiliate postings found in the underground are gender-neutral and open to everyone, as long as they have the right skillsets similar to the real world, where gender is not mentioned. In the underground, recruitment posts for cybercriminal gangs do not mention gender, either.
Mules are used by others to launder the proceeds of cybercrime by taking stolen money and goods and turning them into clean funds. They do this via internet payments, money transfers, or online auctions. We found one website advertised in a Russian forum for document forgery, betting services, and cryptocurrency exchanges where gender and age were specifically mentioned. The business also mentioned offering any photo or video recording services from the women on their site.
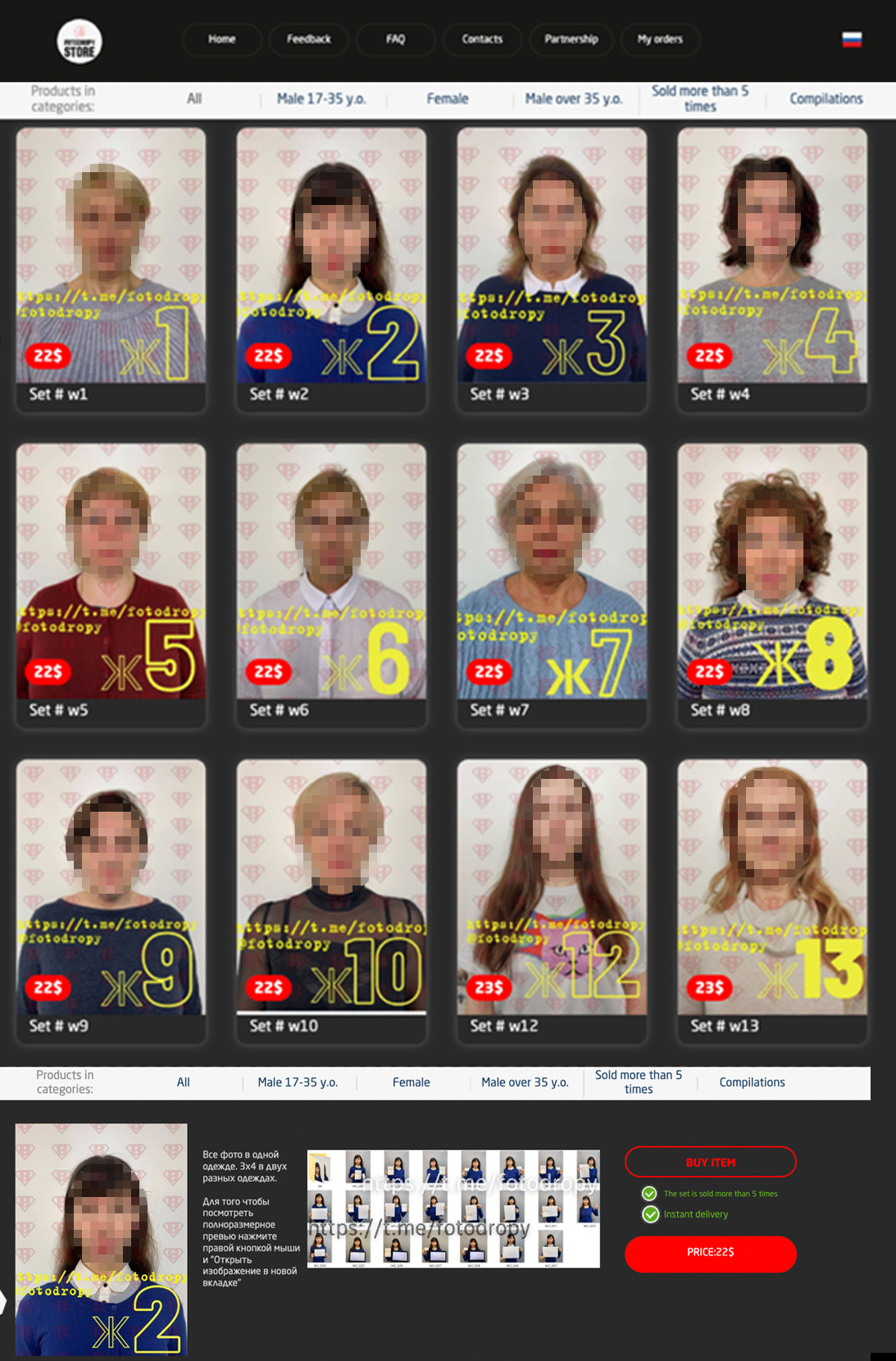
Figure 17. A photo listing of women who can be hired for document forgery, video, and photo services (above). Clicking on a photo opens a new range of photos with the instruction, “all photos are with the same clothing, while photos with 3×4 (size, or ratio) are with 2 clothes. To view the full size preview, click right mouse button and open image in the new tab.” (below)
Romance scams are considered cybercriminal activities when a scammer deceives a user into believing they’re in a romantic relationship with someone they met online. Confidence scams are similar in nature, though varying in schemes such as Grandparent Scams. In fact, the other half — commonly the initiator of contact — is a cybercriminal using a fake identity to gain enough of their victim’s trust for blackmail or to ask for money. In 2021, the Internet Crime Complaint Center (IC3) received reports from 24,299 victims who lost more than $956 million to romance scams. This type of fraud accounts for the third highest losses reported by victims, after business email compromise (BEC) and investment fraud.
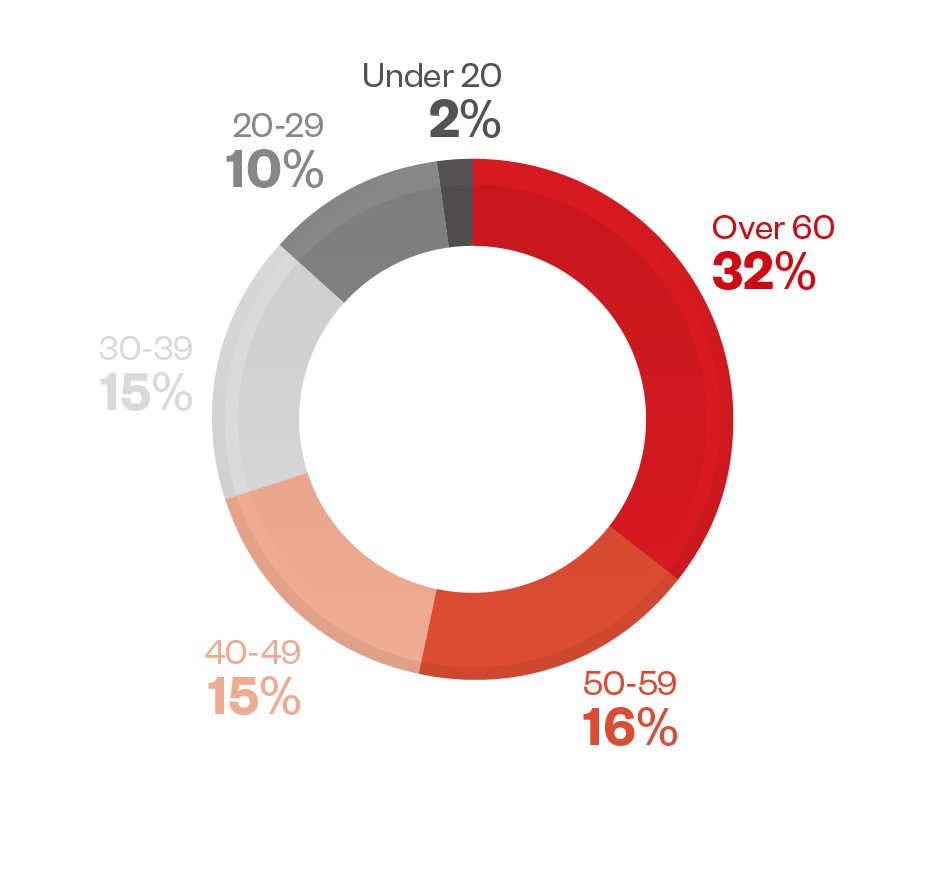
Figure 18. Romance scams and confidence fraud categorized by victims’ age groups (data taken from IC3)
For comparison, this is almost 20 times the losses associated with ransomware in the same report. The pandemic led to a boom in online romance fraud worldwide. According to a survey in the United Kingdom, two in five people (38%) who dated someone they met online were asked for money. Over half (57%) of those who were asked for money said that they gave or lent it. According to the Federal Trade Commission (FTC), people in the US reported losing a total of $1.3 billion to romance scams in the last five years. Admittedly, the number could be even higher because some victims are too embarrassed to come forward after they lose money. The underground posting for these types of scams are usually advertised under the terms “eWhoring” or “social engineering.” Prices for female voice verifications start from $15 per recording upward. These job postings are sometimes very specific with requirements about language accents, physical looks like hair color, and sometimes even some acting skills. These types of advertisements can be found in both English and Russian language forums.
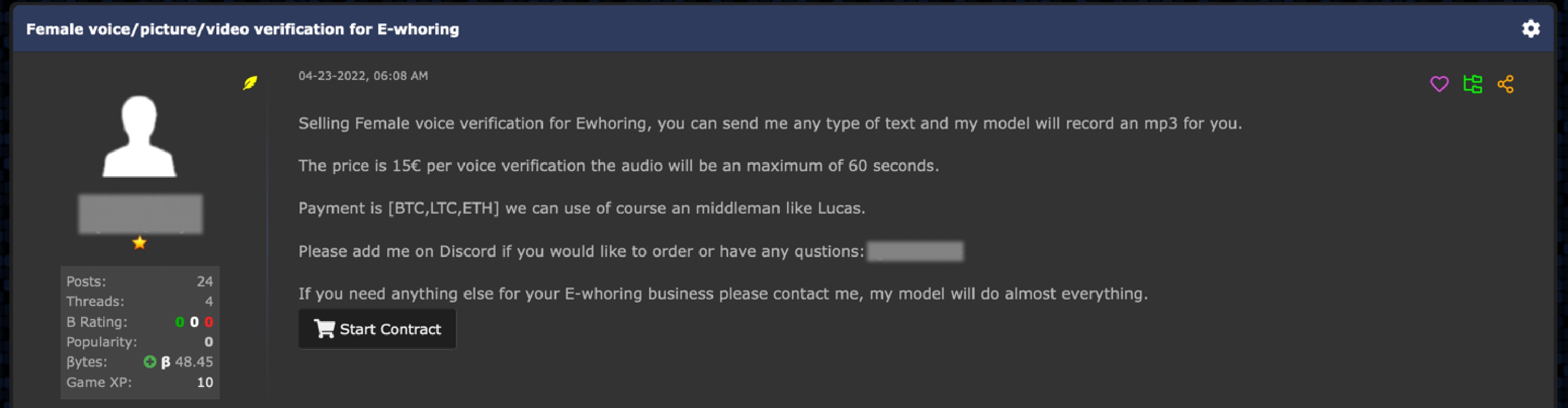
Figure 19. Underground job posting for female voices to use in romance scams
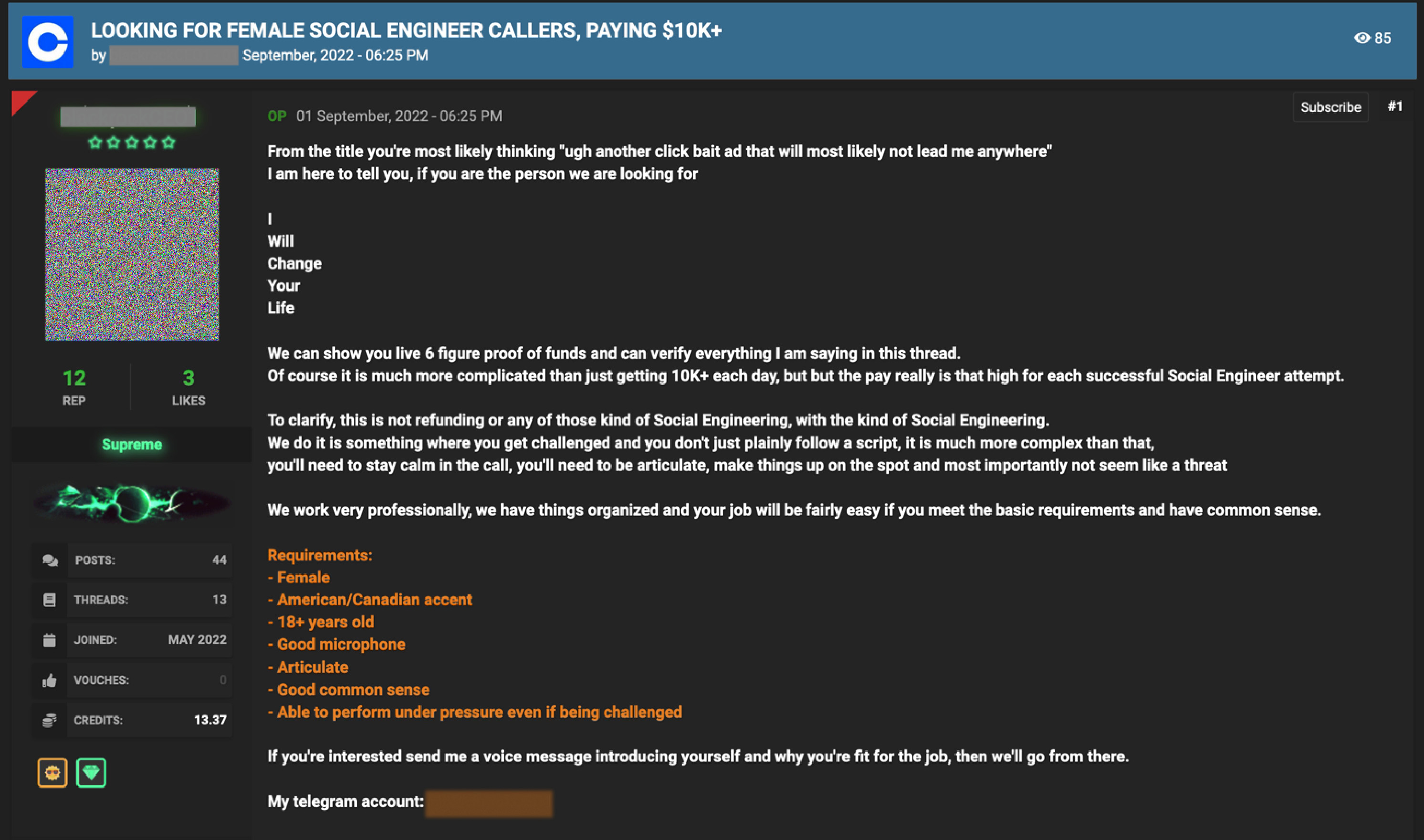
Figure 20. Social engineering scam job posting with very specific requirements
Call center jobs can be found in English- and Russian-based language forums. These types of postings often look for male and female native speakers in multiple languages such as German, English, French Spanish, and Italian. The call center jobs could be used for social engineering, romance scams, and fake software support. Prices start from $10 per call and are sometimes paid by the hour, too. Women are probably sought out due to people being more likely to trust female service agents versus male callers. Some forum users have explicitly said they prefer women for call-based jobs and are better than men at extracting information. In the future, these jobs may be replaced by using artificial intelligence (AI) video creation platforms. Cybercriminal underground forums are already using video creation platforms such as Synthesia for deepfake videos.
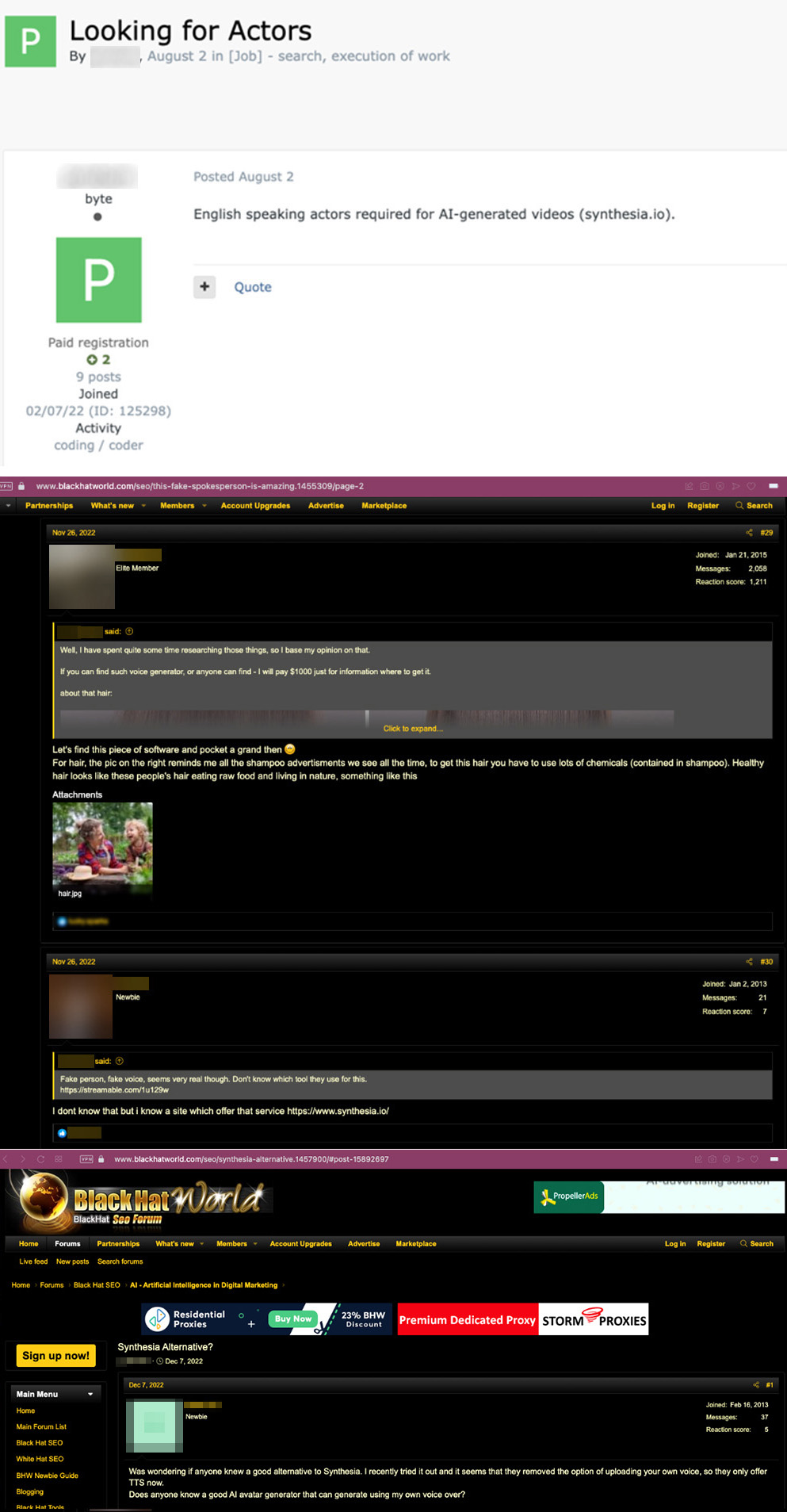
Figure 21. Russian-based forum posts looking for voice actors and platforms to use for deepfake videos
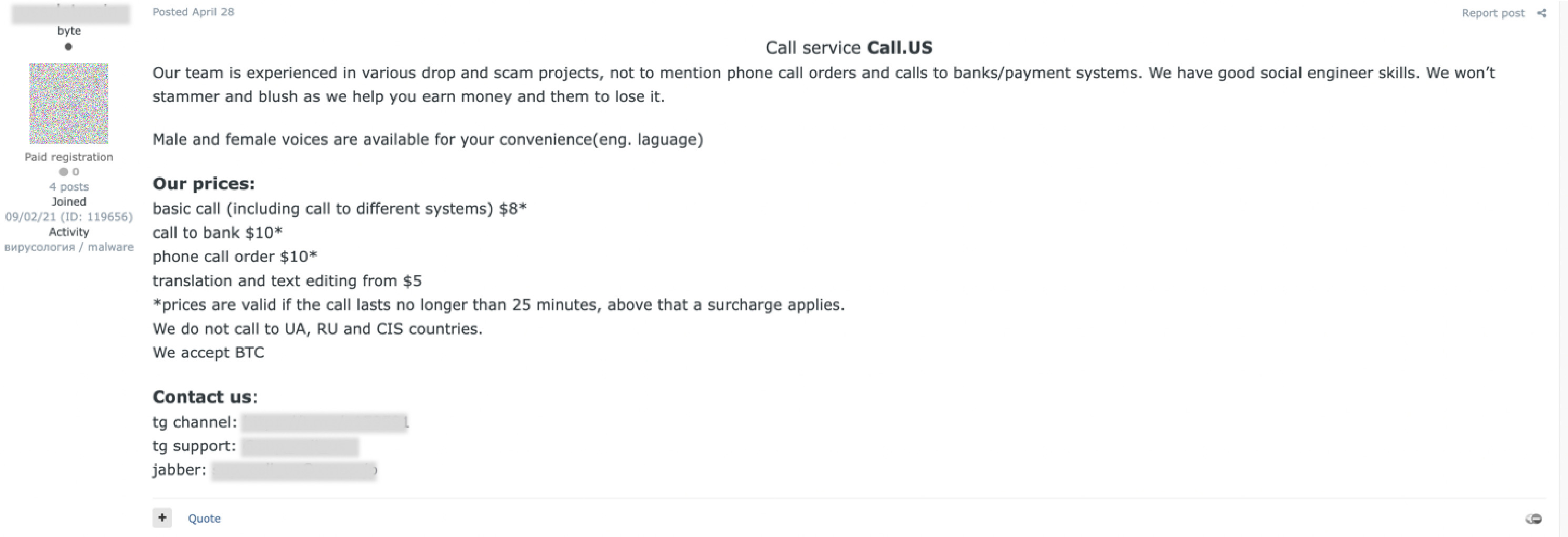
Figure 22. Call center job posting for male and female voice actors
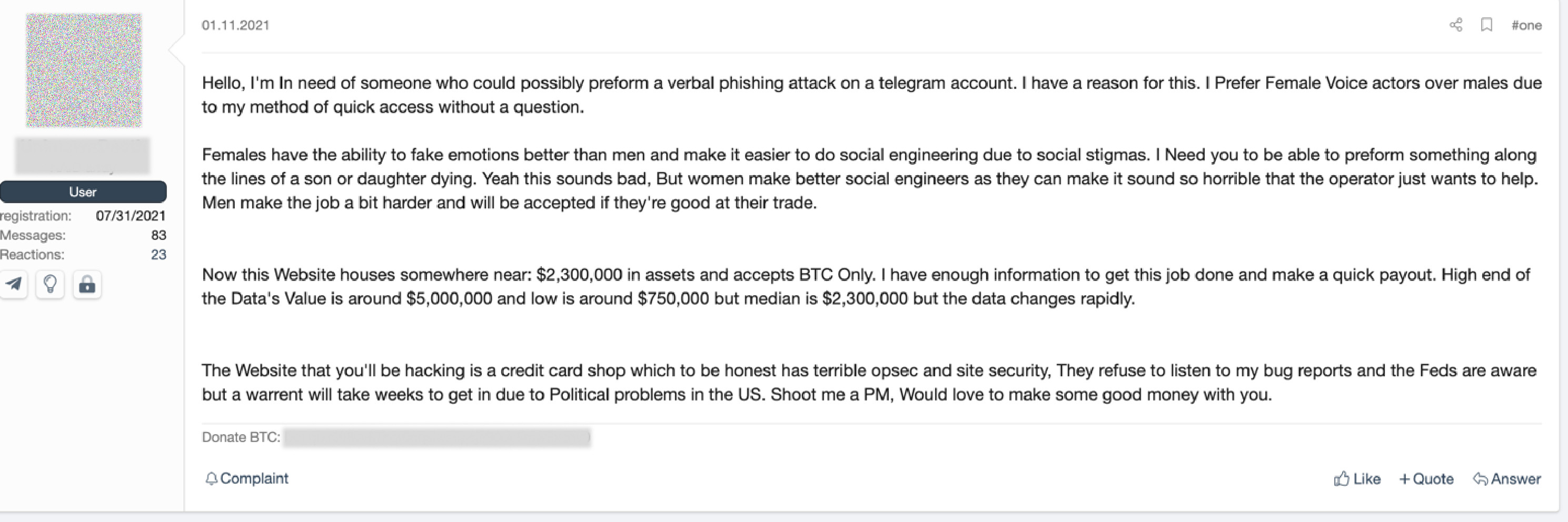
Figure 23. Social engineering job posting for female voice actors
Discussions in the underground for non-cisgender topics are strictly about non-business dealings. These topics can be found in the science, relationship, religion, philosophy, and politics sections of forums. The forums that do talk about these topics are usually English-based spaces. Many of the discussions are derogatory and not taken seriously by others. A few forums’ discussions on this appear to try to have a serious exchange, but are quickly turned down by others or questioned why this topic is being discussed in the forum.
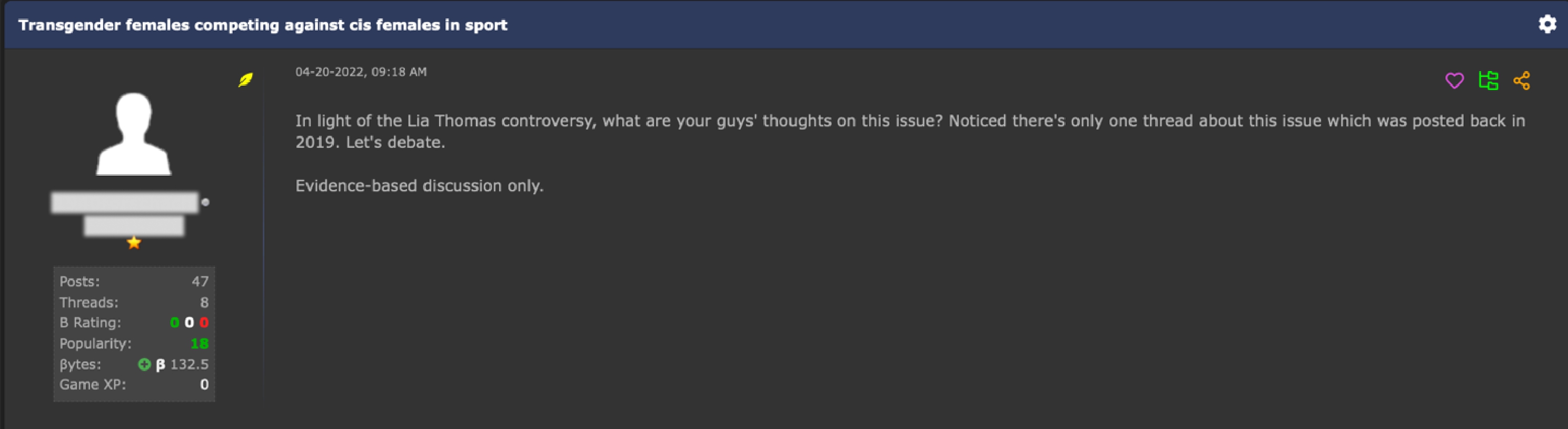
Figure 24. A query for a discussion on a transgender athlete in US college sports
We looked at the top five non-cisgender identity words mentioned in English and Russian language forums based on a list by Spunout.
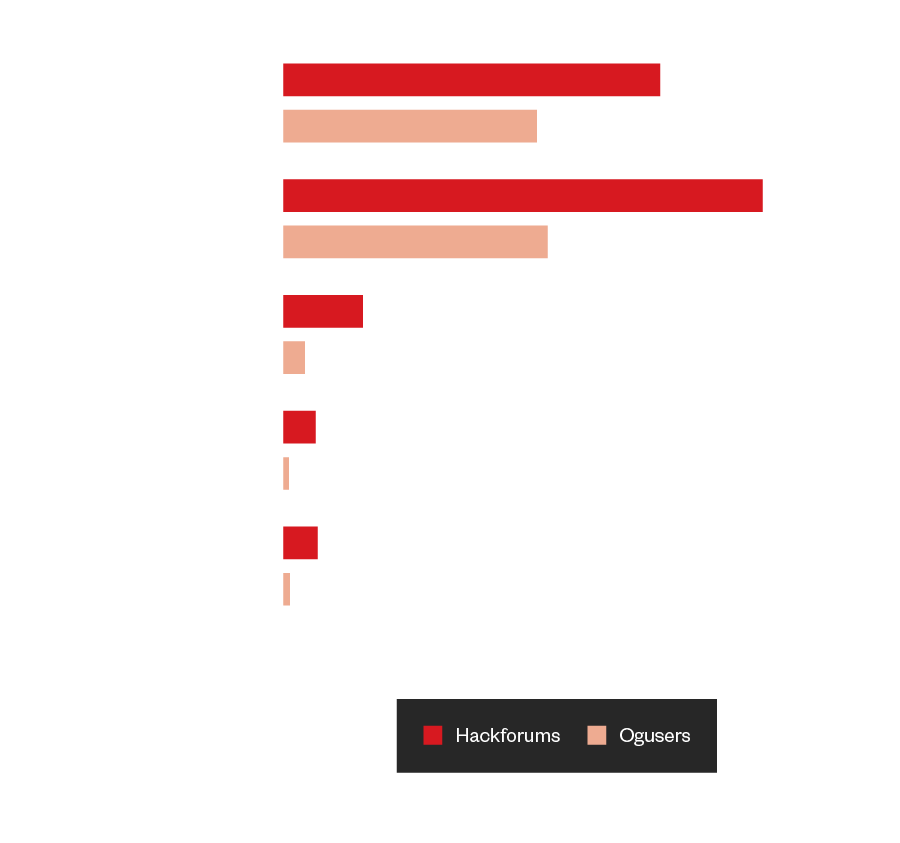
Figure 25. Mention counts of the top five non-cisgender keywords found in underground English forums
The top five most mentioned non-cisgender words were “trans,” “transgender,” “transitioning,” “gender identity,” and “MTF” (male-to-female) in English language forums. In contrast with Russian language forums, we had to reduce the number to the top three words, which were significantly lower and did not reach the hundreds unlike the English language forums’ numbers. Meanwhile, search results for the words “female,” “women,” and “woman” on HackForums reached over 35,000 hits.
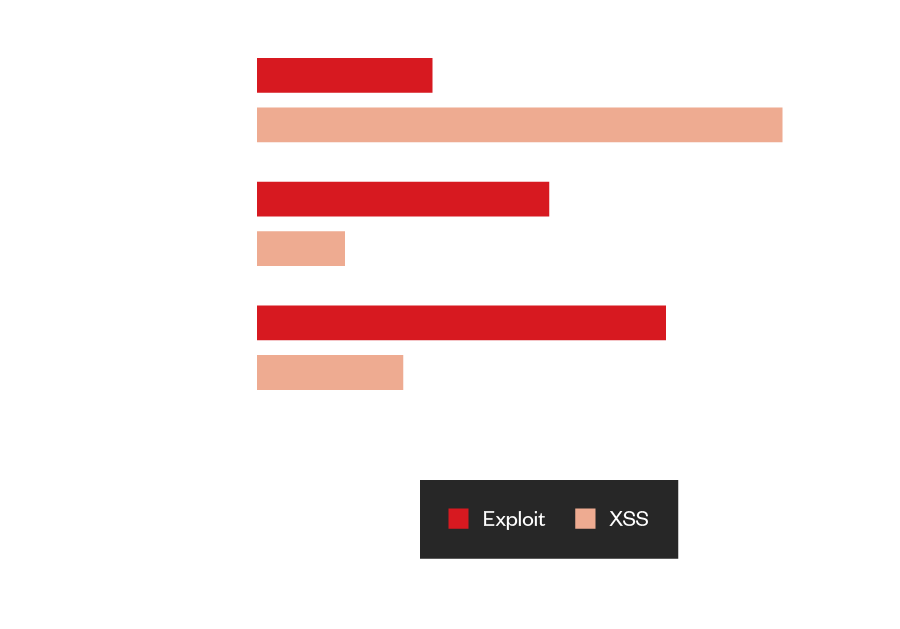
Figure 26. Mention counts of the top three non-cisgender keywords found in underground Russian forums
Overall, this reflects previous sections’ discussions on women in the underground. Topics around gender are unusual, as is any unnecessary revelation of one’s gender outside of job postings (when a specific gender profile is preferred for a role). Unless it has a direct benefit for business, it is not seen as necessary and will not be discussed.
We used a tool called Semrush, a search engine marketing company that uses data from a variety of social networks and public census through their own machine learning (ML) algorithms and trusted data providers to conduct case studies and analytics. While the exact methodology used is proprietary, the company claims to draw on data from web traffic of over 200 million real internet users in 190 countries. Using this tool, we looked at a snapshot of male and female visitors, along with their respective age groups, visiting five English and Russian language forums. As a control sample, we compared them to popular IT blogs Stack Overflow and Reddit.
While we cannot fully validate the methods used by Semrush to ascertain gender, we used it instead to compare traffic to different sites as the methods should be consistent. With an increasing number of women in STEM roles, we wanted to see if there was also a percentage of women visiting underground criminal forums. Considering we see advertisements directed at women in the underground, we can assume someone is answering these postings.
We looked at the following English forums:
We looked at the following five Russian language forums:
We chose these underground forums for their popularity in the cybercrime community, the number of users participating and following the forums, the number of threads, and the number of offered jobs and posts. Especially in the case of the Russian forums, XSS and Exploit rank as the two most popular forums for cybercrime and security research for analysts. XSS was even featured in the news as ransomware actors posted advertisements on the forum looking for people to work with them in the Colonial Pipeline ransomware attack.
For English forums, the total number of visitors at the given time were 200. We found 40% women visited these sites compared to the 60% male visitors. For Russian forums, we also counted 200 visitors. We found 42.6% women visited these sites compared to 57.4% men. Sinister had the most female visitors at 61%. When compared to Stack Overflow, a developer and programming forum, only 12% of visitors were female.
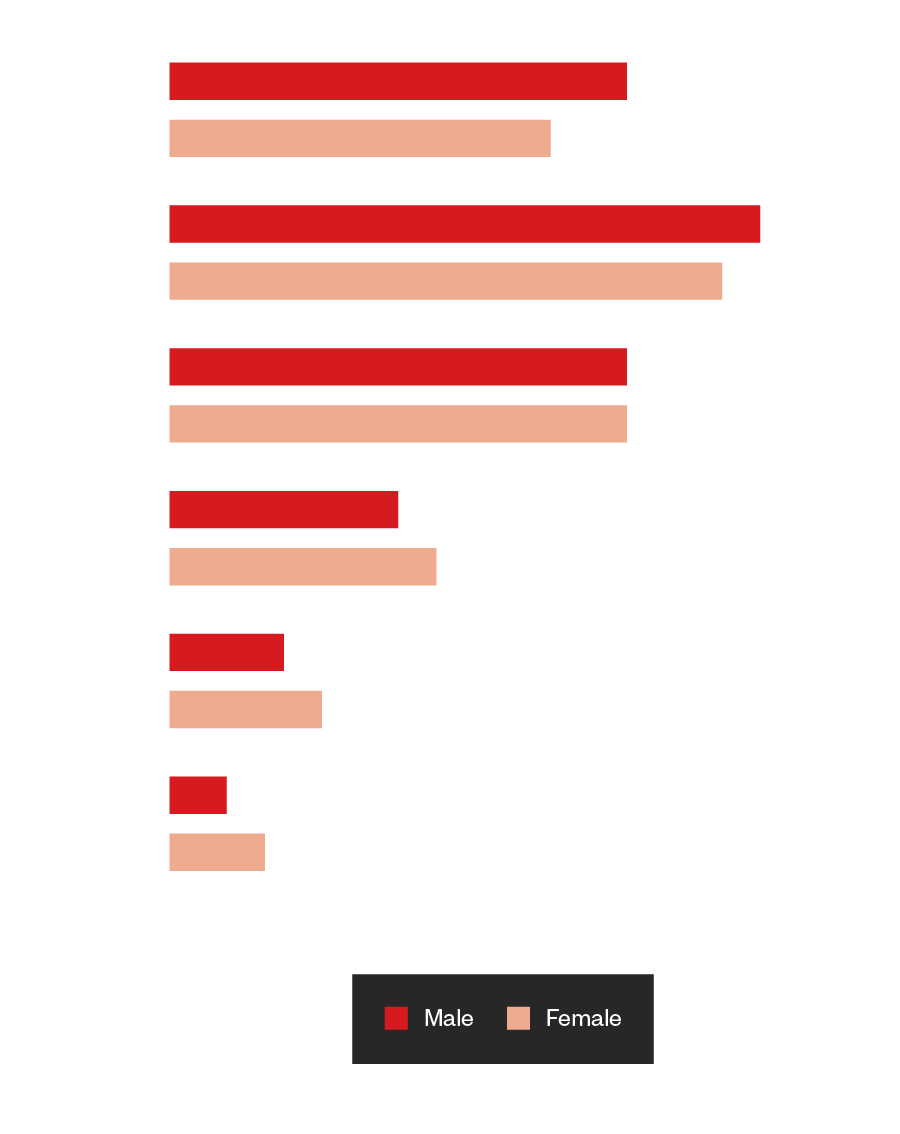
Figure 27. The number of male and female visitors in underground English forums by age group
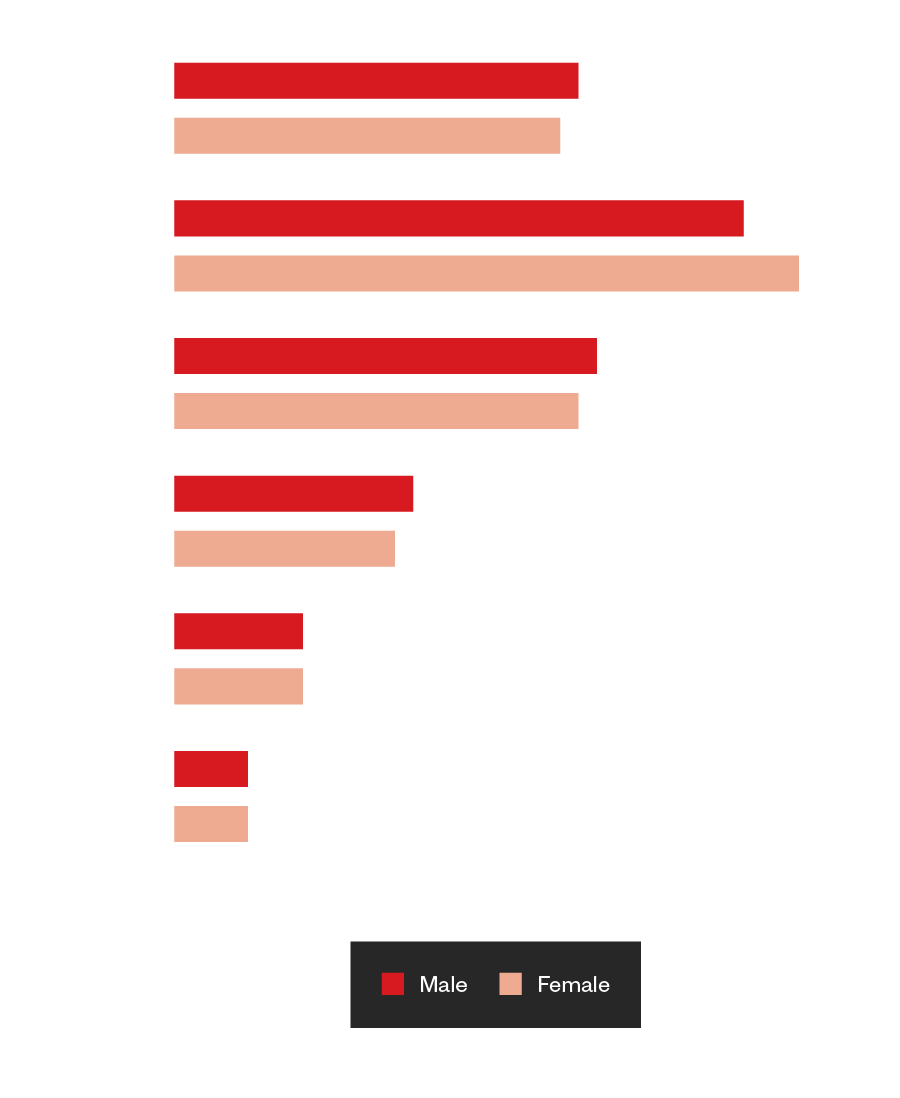
Figure 28. The number of male and female visitors in underground Russian forums by age group
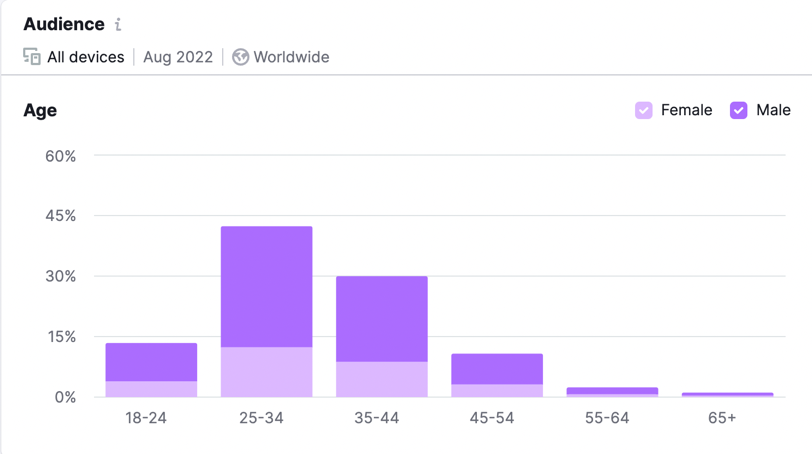
Figure 29. Reddit demographics results for August 2022 (data taken from Semrush)
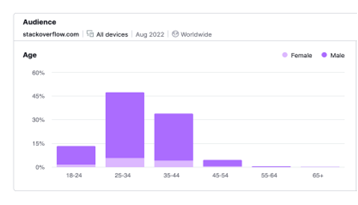
Figure 30. Stack Overflow demographics results for August 2022 (data taken from Semrush)
Looking to find other analytic methods beyond a marketing research tool, we also experimented with an online gender text analyzer to figure out if a forum text is written by a male or female. This is also in consideration that many users do not disclose their gender preferences in their profiles. For this portion of the research, we looked at two popular cybercriminal forums: the Russian-speaking XSS, and the English-speaking Hackforums.
We used the tool Gender Analyzer V5 created in 2008 by uClassify, a machine learning web service to create and use text classifiers. As of this writing, version 5 has been trained to analyze text based on 11,000 blogs: 5,500 blogs written by females and 5,500 by males.
Our control group consisted of 10 aliases that posted their gender profiles online and identified themselves as women from XSS and Hackforums. When we ran posts from these users through the text analyzer, results indicated that all the aliases were classified as female with an average classifier percentage of 82.4%.
We then ran 50 random users’ accounts from XSS forum through the classifier. The average account of these users was created approximately 31 months prior, and had an average of 704 posts to give enough data to work with. When we ran the text analyzer, the results showed that of the 50 random users, 70% were male users and 30% female. Comparing these results to the Semrush analytics, they had predicted that XSS received 59% male visitors compared to 41% women.
We also ran 50 random aliases from Hackforums wherein the average account was 32 months old with an average of 947 posts. The results showed that the aliases were 64% male and 36% female. These results are closer to the overall English forums where we found 40% of women visited these sites compared to 60% when we used Semrush.
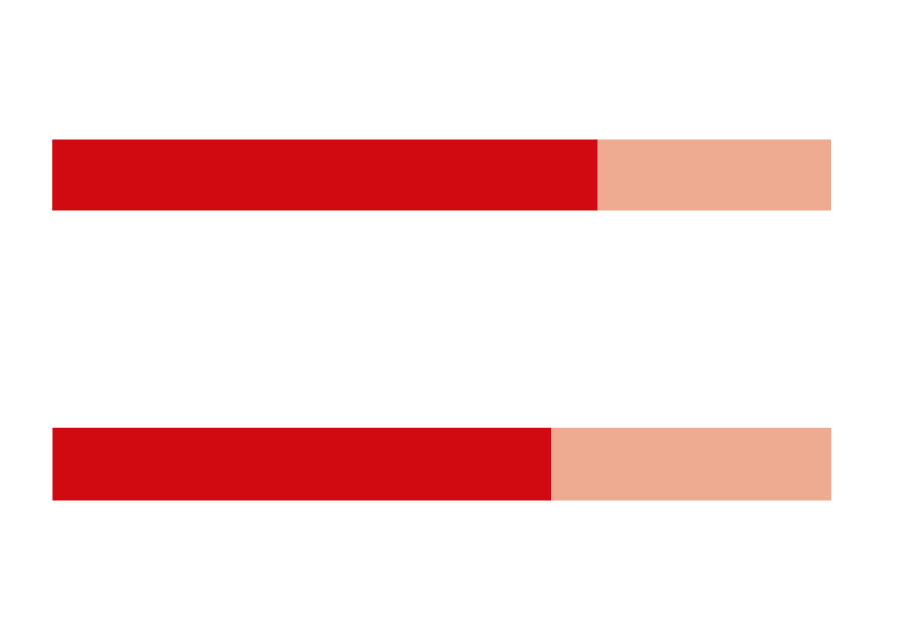
Figure 31. The percentage of male and female users based on text analysis of underground forum users’ accounts
The underground provides an open environment for individuals of any gender to find employment or a side business, particularly in communities that protect potentially discriminating details about identities. While language can be a barrier, we did not see any evidence that an actor was disqualified from participating in a role based on gender. It is generally accepted that most cybercriminals are likely male. However, gender bias — whether explicit or implicit — can severely undermine a criminal investigation. Law enforcement and other investigators should not automatically assume the actor’s gender to be one or the other. Our text analyzer exercise showed that at least 30% of underground forum participants may be women, even though they are not openly discussing their gender profiles online.
The criminal underground is one of the most meritocratic online communities where people are valued only for their skills and experience — and not their gender — when it comes to conducting business. Underground criminal forums in the past have kept up with current events and societal changes. We now often see forum users asking if there are women in the forums, with some even mentioning the increased female participation in STEM fields. Discussion on non-cisgender topics is less common, but this is due to the business-focused nature of these communities where ability is all that matters. As more cybercriminals are arrested and names are published in the media, we might get a better view of how often women get to participate in cybercrime.
It is our recommendation for all investigators to avoid assumptions of male personas while carrying out their work (such as referring to a suspect as “he” or “his”) as this creates an inherent bias as they progress their case. We suggest instead to use “they,” which will not only cover any gender involved, but also force investigators to factor in that more than one person may be behind a single moniker under investigation.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Enterprises and organizations are facing a period of transition and uncertainty – malicious actors will hunker down and reuse tried-and-tested tools and techniques.
View the 2023 Trend Micro Security Predictions
Our annual cybersecurity report sheds light on the major security concerns that surfaced and prevailed in 2022.
View the report
source






























