BIRMINGHAM, Ala. (WBRC) – A Birmingham-based medical practice is informing patients of a data breach that could have compromised personal information.
Cardiovascular Associates (CVA), a physician practice with multiple locations in and around Birmingham, discovered on December 5 that systems within CVA’s network may have been subject to unauthorized activity.
After an investigation, it was determined that a third party had gained access to personal information and removed a copy of some data between November 28 and December 5.
CVA said that some of the personal information involved may include one or more of the following:
CVA said that for a limited number of people, the information may have also included username and password information. The practice did note that “not all data elements were involved for all individuals.”
CVA takes the security of personal information seriously. As soon as the incident was discovered, a forensic investigation was launched, and steps were taken to mitigate and remediate the incident and to help prevent further unauthorized activity. In response to this incident, security and monitoring capabilities are being enhanced and systems are being hardened as appropriate to minimize the risk of any similar incident in the future.
CVA said they are offering complimentary credit monitoring and identity restoration services to those whose sensitive information may have been involved. They advise for patients to carefully review credit reports and statements from healthcare providers and financial institutions to ensure valid account activity.
CVA has set up a dedicated assistance line for anyone seeking more information about the incident. Anyone with questions over the next 90 days can call 1 (833) 753-3802 between 8 a.m. and 8 p.m., Monday through Friday. More information is available at https://response.idx.us/cvainformation/.
Get news alerts in the Apple App Store and Google Play Store or subscribe to our email newsletter here.
Copyright 2023 WBRC. All rights reserved.
Author: rescue@crimefire.in
-
Birmingham medical practice informs patients of security breach – WBRC
-
Top Cyber Security Companies in Delhi – Security Boulevard
The Home of the Security Bloggers Network
Home » Security Bloggers Network »
Strong cyber security measures are now essential given the speed at which businesses are going digital and the rise in cyber threats. Businesses need the help of cyber security firms to protect themselves from attacks and prevent the compromise of important data. Security has become a top priority for both individuals and businesses as a result of the rapid advancement of technology and the addition of new devices to the online world every day.
If a network or equipment is not properly safeguarded from hackers, it might be damaged and breached. According to projections, the cost of cybercrime is expected to rise to $10.5 trillion by 2025. Due to their extensive data collection and storage, businesses are particularly susceptible to cybercrime.
As the nation’s capital and a major commercial center, Delhi is home to a large number of cybersecurity firms. But, not all cyber security companies are the same, so it’s important to pick the one that best suits your needs.
We’ll talk about the leading cyber security companies in Delhi, their offerings, and their distinctive qualities in this blog. In this blog, we’ll look at a few of Delhi’s best cyber security firms, their specialties, and how they’re assisting businesses in keeping their data secure in the current digital environment. So let’s investigate the finest cyber security companies in Delhi.
Cybersecurity is the process of defending computer systems, networks, programs, and data against theft, damage, or unwanted access. In order to stop, recognize, and address attacks and threats against digital systems, a variety of strategies and procedures are used.
Due to the increase in frequency and sophistication of cyberattacks, which can take the shape of viruses, malware, phishing schemes, ransomware, and other forms of malicious software, cybersecurity is becoming an increasingly essential topic. These assaults can potentially compromise private information, result in monetary losses, interfere with commercial operations, and harm one’s reputation.
Organizations and individuals must put in place a number of security measures to maintain cybersecurity, including employing strong passwords, encrypting sensitive data, upgrading software and systems frequently, utilizing firewalls and antivirus software, and offering staff cybersecurity training.
Due to the sophistication and frequency of cyber threats, cybersecurity has emerged as one of the top concerns for both enterprises and individuals. Cyber threats are becoming more sophisticated and complex as technology develops. It should come as no surprise that businesses all around the world are investing in cyber security to safeguard themselves against potential assaults. Some businesses that focus on offering cyber security services are located in Delhi, the capital of India. The solutions provided by these businesses include threat detection and response, vulnerability analysis, penetration testing, and security consultancy.
Below is the list of the Top Cyber security companies in Delhi
Numerous businesses offer various cyber security services, but it’s still unclear which is the best. One of the leading cyber security providers, Kratikal can meet all of your organizational needs.
Kratikal, one of the leading cybersecurity companies, is well known for its innovative security solutions. In addition to security auditing for PCI DSS, HIPAA, GDPR, and ISO 27001, it offers a comprehensive range of penetration testing and vulnerability assessment services.
Through security testing, Kratikal, a CERT-In Empanelled security solutions provider, offers the services required to guarantee the protection of an organization’s IT assets as well as the safety of its employees. The aim of the entire VAPT service portfolio, which includes Network Penetration Testing, Application Penetration Testing, Cloud Penetration Testing, and many others, is to locate the weaknesses in various devices and their networks so that they can be fixed in advance.
In order to help you choose a top cyber security testing company in Delhi, we set out to enlighten you about them in this blog. Post your comments in the space provided below.
The post Top Cyber Security Companies in Delhi appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Deepti Sachdeva. Read the original post at: https://kratikal.com/blog/top-cyber-security-companies-in-delhi/
More Webinars

-
Cybersecurity Threats in Europe: What You Need to Know and What … – tripwire.com
As governments and organizations standardize and harmonize their responses to better mitigate the increasing number of cyber-attacks, so do cybercriminals. In Europe, security decision-makers and businesses face similar attack techniques as their global counterparts. While the methodologies employed are identical because they all rely on the same digital technologies exploiting similar vulnerabilities, the motivations vary.
The threat actors can be distinguished into two major groups according to their motivation:
Both groups follow well-known pathways to initial compromise, such as exploiting unpatched vulnerabilities, credential theft, social engineering and phishing attacks, and deploying malware with a preference for ransomware attacks.
A Forrester report found that throughout 2022, CISOs in European organizations faced four threats that differed from the global trends.
State-sponsored attacks are a valid concern for European businesses, but organized crime is booming.
While Europe is not the key target of state-sponsored activities, security leaders must be aware of this problem. Africa, the Middle East and Turkey are most targeted by politically motivated actors, followed by Northern Europe. In Europe, organizations are predominantly plagued by financially driven threat actors located in Russia, Iran, and North Korea.
Organized cybercriminals have skilled up as cybercrime goes mainstream. With the cybercrime economy growing and becoming the third-largest global economy, criminal gangs are forming collectives to exchange knowledge and trade. Organized Crime as a Service is booming, taking several forms:
Overall, we witness an increased collaboration between cybercriminal gangs, more like Crime as a Business. Cybercriminals have specializations, like any business and teams, and work together to achieve objectives ranging from petty scams to espionage.
Forrester’s data highlights that 16% of European security decision-makers treat securing OT environments as a top tactical priority. At the same time, IBM reports a 2,204% increase in reconnaissance against OT systems.
State-sponsored affiliated actors, including Electrum, Magnallium, and Xenotime, increasingly target manufacturing organizations. These actors gain initial access using credential theft, exploiting cloud vulnerabilities and malware. However, the positive sign is that security decision-makers at organizations that had experienced disruption or data ransom were more likely to prioritize ICS or OT security.
Businesses need help to integrate threat intelligence into their security programs. However, threat intelligence feeds listing initial compromise indicators must be more comprehensive. European organizations must evaluate their threat intelligence program through three lenses: tactical, operational, and strategic. This is essential because, besides recognizing the attackers’ tactics, geography and politics are vital factors to consider when building cyber threat intelligence.
Therefore, businesses should base their threat intel program on four critical considerations:
Focusing on the OT domain, security begins with knowing your environment. Therefore, the first step is to identify all your intellectual property and where it resides and consider how you can protect it with consistent data security policies.
Once you have achieved the desired level of visibility, the next step is to encrypt your critical data and implement a data loss prevention (DLP) strategy. Leveraging specialized DLP software offers multiple benefits for organizations. Finally, you should use data classification capabilities and centralized policy management to simplify detection and policy enforcement.
However, cybersecurity is not only about processes. It is also about the people and technology in your organization. European organizations should prepare their people for the possibility of a successful attack. There are several steps you can take in this direction:
Fortra has long been known for helping organizations become more secure and autonomous. To increase security maturity and decrease operational burden, we must address technology-based and people-based vulnerabilities together. That means securing infrastructure and data, consistently improving people’s awareness of security risks, and supplementing their teams with additional security operations resources.
By doing this successfully, we will significantly increase an organization’s security maturity in the areas that account for 75% of all attacks with just one cybersecurity partner while decreasing their operational burden. Fortra offers a wide range of cybersecurity solutions to help European organizations effectively protect against the evolving threat landscape.
To dig more into the topic, understand in greater detail the Forrester survey findings and learn how Fortra can help you, you may watch the on demand webinar, “Cybersecurity Threats In Europe: What You Need to Know and What to Do About Them.” -
Economic volatility to exacerbate cyber risk in 2023 – Cybersecurity Dive
Let Cybersecurity Dive’s free newsletter keep you informed, straight from your inbox.
Global economic uncertainty hangs over everything like a dark cloud, which is triggering market volatility and risks across the cybersecurity sector too.
“Cybersecurity is not immune to recessions — research indicates that cyberattacks increase during and following economic downturns,” the think tank said in the report.
Key risk factors related to a potential recession include delayed innovation and inadequate budgets for long-term investments.
Organizations have improved corporate governance in cybersecurity, but the headway has been modest at best, according to the Bipartisan Policy Center. Distance between security professionals and the C-suite on information flow and decision making, and a lack of technical expertise on boards of directors are compounding this risk and must be addressed.
The think tank also called out vulnerable infrastructure, particularly third- and fourth-party vendors that may lack necessary cybersecurity controls, as a top risk for 2023.
“Vulnerable software, operating systems, or other infrastructure almost always factor into consequential security incidents and data breaches,” the report said.
“Keeping pace with patching and replacing end-of-life software and hardware is a major operational burden for organizations of all sizes. When this need is ignored, the cost, complexity and likelihood of incidents multiply over time,” the think tank warned in its report.
Other top macro risks include overlapping and conflicting regulations, talent scarcity, geopolitical tension and an accelerating cyber arms race.
The report pulled from a working group assembled to identify the top cybersecurity risks confronting all stakeholders. Members include current and former officials in state and federal government and executives from banking, cloud, communications, health, energy and other sectors.
Get the free daily newsletter read by industry experts
Enterprise cybersecurity is navigating market turmoil and vendor consolidation. Here’s what experts expect to happen to the industry in 2023.
Chief Product Officer Josh Prewitt said the company restored email access to more than three-quarters of its Hosted Exchange customers. But Rackspace officials pushed back on alleged connections to ProxyNotShell.
Subscribe to Cybersecurity Dive for top news, trends & analysis
Get the free daily newsletter read by industry experts
Enterprise cybersecurity is navigating market turmoil and vendor consolidation. Here’s what experts expect to happen to the industry in 2023.
Chief Product Officer Josh Prewitt said the company restored email access to more than three-quarters of its Hosted Exchange customers. But Rackspace officials pushed back on alleged connections to ProxyNotShell.
The free newsletter covering the top industry headlines -
Rapid7 Brings Threat Intel Data to USF Cybersecurity Lab – Dark Reading
Cybersecurity In-Depth
At the most basic level, security research happens when curious people poke around data. What makes it good security research is when these people have access to good data and the right kind of skills.
That is what Rapid7 hopes to accomplish with its new partnership with the University of South Florida to create a cyber threat intelligence laboratory. The Boston company recently made a $1.5 million donation via the Rapid7 Cybersecurity Foundation to set up the Rapid7 Cyber Threat Intelligence Laboratory at the school.
Rapid7 will provide the laboratory with access to its massive data initiatives, including Metasploit, Velociraptor, and Sonar, says Corey Thomas, Rapid7’s CEO. The laboratory will support interdisciplinary research efforts by faculty experts and students and help drive a deeper understanding of the challenges defenders are currently facing.
“We are already investing in the data, and we want more people to use the data,” says Thomas, noting that people with varying experiences and backgrounds bring diverse perspectives and wind up using the data differently. “Start with the same data and get different insights,” Thomas says.
The students will have the opportunity for hands-on learning and cybersecurity skills development as well as real-world experience tracking global threat actors. Laboratory projects and research based on threat intelligence data will help students better understand the challenges security practitioners face as they protect users, Thomas says. The laboratory would play a role in helping to educate and develop the next generation of security professionals, he adds.
Through the laboratory, students and faculty will have access to real world data they can use for research and training, which is an “unprecedented opportunity,” Robert Bishop, dean of the USF College of Engineering, says in an email to Dark Reading. “Most importantly, this partnership is going to bring the campus together on cybersecurity research.”
The laboratory will launch by establishing an interdisciplinary faculty leadership foundation with a new directorship in the USF College of Engineering and endowed faculty positions created in four USF colleges: the College of Arts and Sciences, College of Behavioral and Community Sciences, College of Engineering, and the Muma College of Business. The laboratory will also work closely with the State of Florida’s Cyber Florida initiative, a program based out of the university focused on expanding and enhancing the cybersecurity workforce in the Tampa Bay region.
Rapid7 already has a history of investing in the community, Thomas says. There are many areas of collaboration in threat intelligence, incident response, and information sharing. With this partnership with the University of South Florida, the company is “escalating our commitment to open data, open research, and open threat intelligence,” Thomas says.
Thomas says he is not going to try to predict what kind of research projects will come out of the laboratory. Rapid7 is providing the data, but the university faculty and students will be pushing forward their own ideas and perspectives. “We aren’t controlling the outcome — the professors and students have their own plans,” Thomas says.
Many universities have established cybersecurity laboratories to provide students with hands-on learning opportunities to gain cybersecurity skills and real-world experience in the field. A laboratory setting makes it possible to refine techniques, get access to different resources from outside partners, and collaborate across different fields to drive research in security technology and techniques. The results of the laboratory research will help improve the industry’s understanding of attacker behavior, and those insights then flows back to practitioners to apply to their jobs.
Back in 2018, the Royal Bank of Canada (RBC) opened a cybersecurity laboratory at the University of Waterloo to help build advanced cybersecurity and privacy tools. The RBC investment supported researchers in the David R. Cheriton School of Computer Science and the Department of Combinatorics and Optimization at Waterloo’s Faculty of Mathematics, according to the university. Research projects included data-driven software defined security, privacy-enhancing technologies, and post-quantum cryptography. Defense contractor Northrop Grumman partnered with California Polytechnic University back in 2014 to establish the Cal Poly–Northrop Grumman Cyber Lab as a cybersecurity teaching facility. The lab gave faculty and students the opportunity to engage with experts from other higher education institutions, private businesses, defense and government agencies, and research labs.
These private sector partnerships with educational institutions also focus on developing a cybersecurity workforce. For example, IBM partnered with Historically Black College & Universities to establish Cybersecurity Leadership Centers. As part of the partnership, IBM provides a customized security curriculum and learning platform to complement the university’s cybersecurity education offerings. Faculty and students also have access to IBM Security’s Command Center, an immersive training experience on how to respond to cyberattacks.
The Rapid7 Cyber Threat Intelligence Laboratory fits in with ongoing cybersecurity initiatives at the University of South Florida because of the focus on developing the skills needed to enter the cybersecurity workforce. The university recently received a $3.7 million grant from the National Science Foundation (NSF) to establish the Cybersecurity Research and Education for Service in Government (CREST) program. The NSF grant would provide scholarships for over two dozen graduate and undergraduate students to prepare them for in-demand and high-paying jobs with the federal government and other public institutions, according to a university press release. The funds will also be used to bolster educational and research resources at the Florida Center for Cybersecurity, or Cyber Florida, which is housed at USF and gives students access to classroom simulations and experiential learning opportunities. There is also a program to help professionals without a computer science background enter a master’s program in the field, according to Dr. Sudeep Sarkar, distinguished university professor and department chair of computer science and engineering at the University of South Florida.
“By focusing on both continuing education for professionals and enhancing current cybersecurity education efforts, USF is working to fill the talent pipeline for one of the fastest growing and most lucrative fields in the United States,” Sarkar tells Dark Reading in an email exchange.
Copyright © 2023 Informa PLC Informa UK Limited is a company registered in England and Wales with company number 1072954 whose registered office is 5 Howick Place, London, SW1P 1WG. -
Why Is Hub Cyber Security (HUBC) Stock Up 62% Today? – InvestorPlace
Copyright © 2023 InvestorPlace Media, LLC. All rights reserved. 1125 N. Charles St, Baltimore, MD 21201.
HUBC stock is bouncing back from recent dips
Hub Cyber Security (NASDAQ:HUBC) stock is on the rise shortly after the company went public through a special purpose acquisition company (SPAC) merger with Mount Rainier Acquisition Corp.
That merger took place on Wednesday and saw the company’s shares change over to the new HUBC stock ticker. However, the company didn’t go public without its own drama, as certain issues caused the stock to fall with its debut.
That negative momentum continued into Thursday as shares saw a 21.4% decline in normal trading hours on Thursday. That came alongside more than 11 million shares changing hands.
Now, it seems like shares of HUBC stock are finally done falling as they rally this morning. The company’s shares are climbing 62.4% in pre-market trading on Friday. That comes as 10 million shares of the stock change hands.
Hub Cyber Security is a cybersecurity company that’s targeting a different form of data protection. The company seeks to protect data when it’s in use, rather than just in storage or in transit. The company seeks commercial customers as well as contracts with large businesses and governments for cloud data protection.
Investors looking for even more of the latest stock market news will want to stick around!
We have all of the hottest stock market news investors need to know about on Friday! Among that is what has shares of ObsEva (NASDAQ:OBSV) stock rising, the biggest pre-market stock movers this morning and more! We’ve got all that news ready to go at the following links!
On Penny Stocks and Low-Volume Stocks: With only the rarest exceptions, InvestorPlace does not publish commentary about companies that have a market cap of less than $100 million or trade less than 100,000 shares each day. That’s because these “penny stocks” are frequently the playground for scam artists and market manipulators. If we ever do publish commentary on a low-volume stock that may be affected by our commentary, we demand that InvestorPlace.com’s writers disclose this fact and warn readers of the risks.
Read More: Penny Stocks — How to Profit Without Getting Scammed
On the date of publication, William White did not hold (either directly or indirectly) any positions in the securities mentioned in this article. The opinions expressed in this article are those of the writer, subject to the InvestorPlace.com Publishing Guidelines.
Technology, Cybersecurity
Penny StocksArticle printed from InvestorPlace Media, https://investorplace.com/2023/03/why-is-hub-cyber-security-hubc-stock-up-62-today/.
©2023 InvestorPlace Media, LLC
Stocks to Buy
Stocks to Buy
Today's Market
Financial Market Data powered by FinancialContent Services, Inc. All rights reserved. Nasdaq quotes delayed at least 15 minutes, all others at least 20 minutes. Copyright © 2023 InvestorPlace Media, LLC. All rights reserved. 1125 N. Charles St, Baltimore, MD 21201.
Not Yet a Premium Subscriber?
Sign up below to get this incredible offer! There’s even room for more lines. Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Your Email -
7 trends that could shape the future of cybersecurity in 2030 – World Economic Forum
Organizations must be prepared to tackle cybersecurity threats. Image: Freepik.com
Listen to the articleWhat is the World Economic Forum doing on cybersecurity?
Create a free account and access your personalized content collection with our latest publications and analyses.
License and Republishing
World Economic Forum articles may be republished in accordance with the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International Public License, and in accordance with our Terms of Use.
The views expressed in this article are those of the author alone and not the World Economic Forum.
A weekly update of the most important issues driving the global agendaYou can unsubscribe at any time using the link in our emails. For more details, review our
privacy policy.
This one simple technique can help you avoid online scams, new research says
Yaniv Hanoch and Nicholas J. Kelley
March 1, 2023
Cybersecurity in this era of polycrisis
Giulia Moschetta, Filipe Beato and Akshay Joshi
February 24, 2023
Cyber scams are exploiting Türkiye-Syria earthquake relief efforts. Here’s what to know
Spencer Feingold
February 24, 2023
What is tech diplomacy and why does it matter?
Sebastian Buckup and Mario Canazza
February 23, 2023
Who is responsible for cybersecurity in the home?
Remko Vos
February 22, 2023
Cybersecurity: Why we need to shift the narrative to build a cyber-ready workforce
Santha Subramoni
February 8, 2023
About Us
Events
Media
More from the Forum
Partners & Members
Language Editions
Privacy Policy & Terms of Service
© 2023 World Economic Forum -
WH Smith staff data hit by cyber-attack – BBC
High Street retailer WH Smith has been hit by a cyber-attack, with hackers accessing some of its workers' data.
Data that may have been breached includes names, addresses, National Insurance numbers and dates of birth of the firm's current and former UK staff.
However, its website, customer accounts and customer databases are not affected, WH Smith said.
The company said it had launched an investigation and had told the relevant authorities of the incident.
"WH Smith takes the issue of cyber-security extremely seriously and investigations into the incident are ongoing," it said.
"We are notifying all affected colleagues and have put measures in place to support them."
It added: "There has been no impact on the trading activities of the group. Our website, customer accounts and underlying customer databases are on separate systems that are unaffected by this incident."
WH Smith did not say how many of its current and former employees had been affected by the breach, which took place earlier this week. The company employs about 10,000 people in the UK across its High Street stores and outlets at railway stations and airports.
The Information Commissioner's Office, a watchdog which investigates data breaches, said it was aware of the incident and was investigating.
Lauren Wills-Dixon, an expert in data privacy law at law firm Gordons, said retailers were at a higher risk of cyber-attack because of the large amount of data they hold on their customers and employees.
"There is also enhanced reputational risk and potential for disruption because retailers are so reliant on public trust and confidence, which cyber incidents threaten to undermine. This makes the retail sector an attractive target."
She added that attacks on employees' data could be more damaging than others because the type of data companies hold about their staff means a leak can lead to a greater risk of identity theft for the affected individuals.
This year has already seen two cyber-attacks on high-profile UK companies.
In January, Royal Mail was hit by a Russian linked ransomware attack that caused severe disruption to overseas deliveries for several weeks.
That same month sportswear chain JD Sports said that it had been targeted by a cyber-attack which could have put data relating to 10 million customers at risk.
In April last year, online greeting card company Funky Pigeon, which is owned by WH Smith, was hit by a cyber-attack that left it unable to process orders for several days.
Post offices resume overseas mail after cyber-attack
Cyber-attack hits 10 million JD Sports customers
Ukraine names unarmed smoking soldier shot by Russians
Exposed for abuse but still revered – Japan’s pop predator
Suppressing China won't make America great – Beijing
Japan’s J-pop predator – exposed for abuse but still revered
Comebacks, stunts and selfies: 8 awards season highlights
The book that records all disasters at sea
The crane which refuses to leave its human saviour. Video
The migrants stranded on an island they had not heard of
The sacred stone stolen by the English
Twitter insiders: We can't protect users from trolling under Musk
Quake survivors living in fear on Turkey's streets
The island paradise held prisoner by heroin
The university that changed the world
11 of the best films to watch in March
Why scraping burnt toast may be wise
© 2023 BBC. The BBC is not responsible for the content of external sites. Read about our approach to external linking. -
Belgium's cyber security agency links China to spear phishing attack … – Financial Times
Keep abreast of significant corporate, financial and political developments around the world. Stay informed and spot emerging risks and opportunities with independent global reporting, expert commentary and analysis you can trust.
- Then ₹4,190 per month
- New customers only
- Cancel anytime during your trial
During your trial you will have complete digital access to FT.com with everything in both of our Standard Digital and Premium Digital packages.
Standard Digital includes access to a wealth of global news, analysis and expert opinion. Premium Digital includes access to our premier business column, Lex, as well as 15 curated newsletters covering key business themes with original, in-depth reporting. For a full comparison of Standard and Premium Digital, click here.
Change the plan you will roll onto at any time during your trial by visiting the “Settings & Account” section.
If you do nothing, you will be auto-enrolled in our premium digital monthly subscription plan and retain complete access for ₹4,190 per month.
For cost savings, you can change your plan at any time online in the “Settings & Account” section. If you’d like to retain your premium access and save 20%, you can opt to pay annually at the end of the trial.
You may also opt to downgrade to Standard Digital, a robust journalistic offering that fulfils many user’s needs. Compare Standard and Premium Digital here.
Any changes made can be done at any time and will become effective at the end of the trial period, allowing you to retain full access for 4 weeks, even if you downgrade or cancel.
You may change or cancel your subscription or trial at any time online. Simply log into Settings & Account and select “Cancel” on the right-hand side.
You can still enjoy your subscription until the end of your current billing period.
We support credit card, debit card and PayPal payments.
Find the plan that suits you best.
Premium access for businesses and educational institutions.
Check if your university or organisation offers FT membership to read for free.
We use and other data for a number of reasons, such as keeping FT Sites reliable and secure, personalising content and ads, providing social media features and to analyse how our Sites are used.
International Edition -
2022 Healthcare Data Breach Report – HIPAA Journal
The HIPAA Journal is the leading provider of news, updates, and independent advice for HIPAA compliance
Posted By HIPAA Journal on Jan 24, 2023
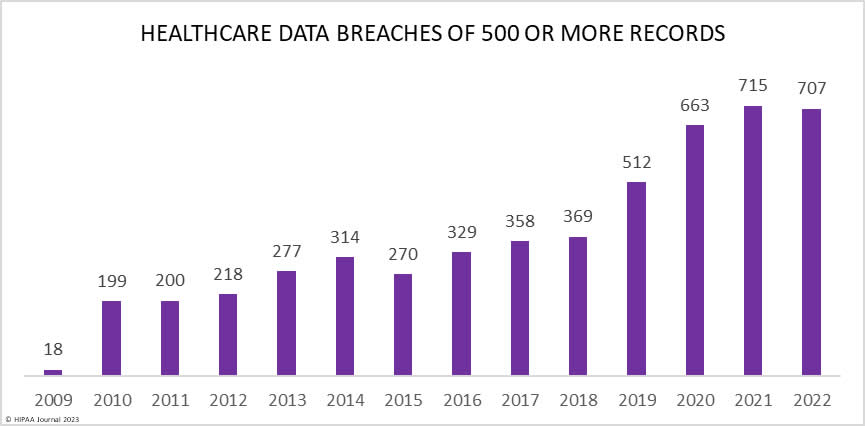
For the first time since 2015, there was a year-over-year decline in the number of data breaches reported to the Department of Health and Human Services’ Office for Civil Rights (OCR), albeit only by 1.13% with 707 data breaches of 500 or more records reported. Even with that reduction, 2022 still ranked as the second-worst-ever year in terms of the number of reported breaches.
As the year drew to an end, data breach numbers started to decline from a high of 75 data breaches in October. Time will tell whether this trend will continue in 2023, although the lull in data breaches appears to have continued so far this year with an atypically low number of breaches currently showing on the OCR data breach portal this month.
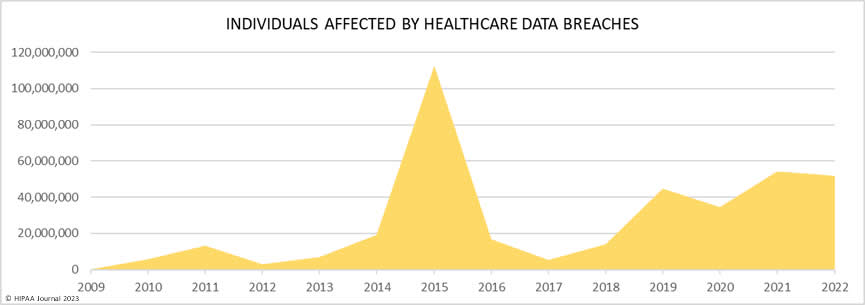
In addition to the slight reduction in reported data breaches, there was also a drop in the number of breached records, which fell by 13.15% from 54.09 million records in 2021 to 51.9 million records in 2022.
The theft of protected health information places patients and health plan members at risk of identity theft and fraud, but by far the biggest concern is the threat to patient safety. Cyberattacks on healthcare providers often cause IT system outages, which in many cases have lasted several weeks causing considerable disruption to patient care. While there have not been any known cases of cyberattacks directly causing fatalities, the lack of access to patient data causes diagnosis and treatment delays that affect patient outcomes. Multiple studies have identified an increase in mortality rates at hospitals following ransomware attacks and other major cyber incidents.
Delivered via email so please ensure you enter your email address correctly.
Your Privacy Respected
HIPAA Journal Privacy Policy
These cyberattacks and data breaches result in huge financial losses for healthcare organizations. The 2022 IBM cost of a data breach report indicates the average cost of a healthcare data breach increased to an all-time high of $10.1 million in 2023, although data breaches can be significantly more expensive. In addition to the considerable breach remediation costs, security must be improved, cyber insurance premiums increase, and it is now common for multiple class action lawsuits to be filed following data breaches. There is also a risk of financial penalties from regulators.
The largest ever healthcare data breach, suffered by Anthem Inc in 2015, affected 78.8 million members and cost the health insurer around $230 million in clean-up costs, $115 million to settle the lawsuits, $39.5 million to settle the state attorneys general investigation, and $16 million to resolve the OCR investigation. Even much smaller data breaches can prove incredibly costly. Scripps Health suffered a data breach of 1.2 million records in 2021 due to a ransomware attack. The attack caused losses in excess of $113 million due to lost business ($92 million) and the clean-up costs ($21 million). There are also several lawsuits outstanding and there could be regulatory fines.
There were 11 reported healthcare data breaches of more than 1 million records in 2022 and a further 14 data breaches of over 500,000 records. The majority of those breaches were hacking incidents, many of which involved ransomware or attempted extortion. Notable exceptions were several impermissible disclosure incidents that resulted from the use of pixels on websites. These third-party tracking technologies were added to websites to improve services and website functionality, but the data collected was inadvertently transmitted to third parties such as Meta and Google when users visited the websites while logged into their Google or Facebook accounts. The extent to which these tracking technologies have been used by healthcare organizations prompted OCR to issue guidance on these technologies, highlighting the considerable potential for HIPAA violations.
While 2022 saw some very large data breaches reported, the majority of reported data breaches were relatively small. 81% of the year’s data breaches involved fewer than 50,000 records, and 58% involved between 500 and 999 records.
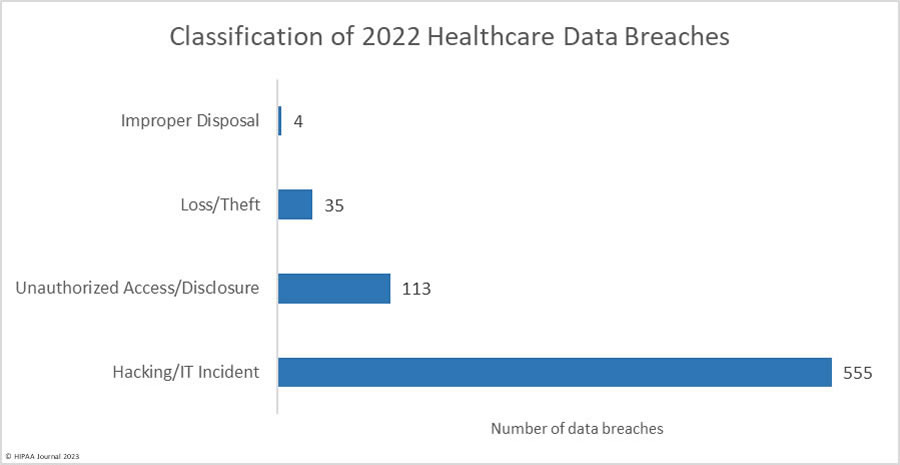
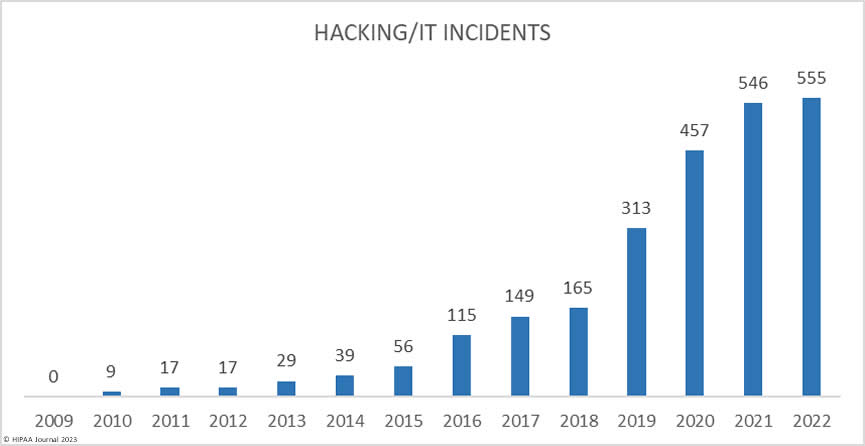
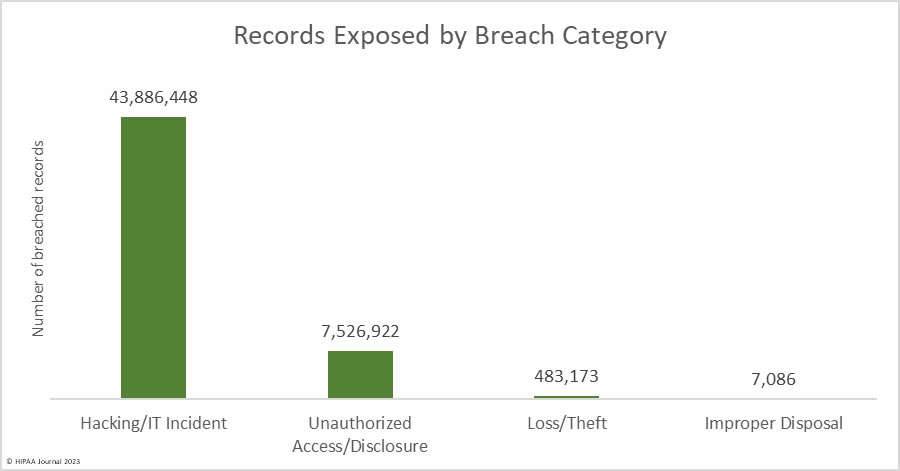
Hacking incidents dominated the breach reports with 555 of the 707 reported breaches (71.4%) classified as hacking/IT incidents, which accounted for 84.6% of all breached records in 2022. The average breach size was 79,075 records and the median breach size was 8,871 records. It is important to note that while the number of healthcare data breaches declined slightly year-over-year, the number of hacking/IT incidents increased by 1.65% in 2022. Attacks are still increasing, but at a much lower rate than in the previous 3 years.
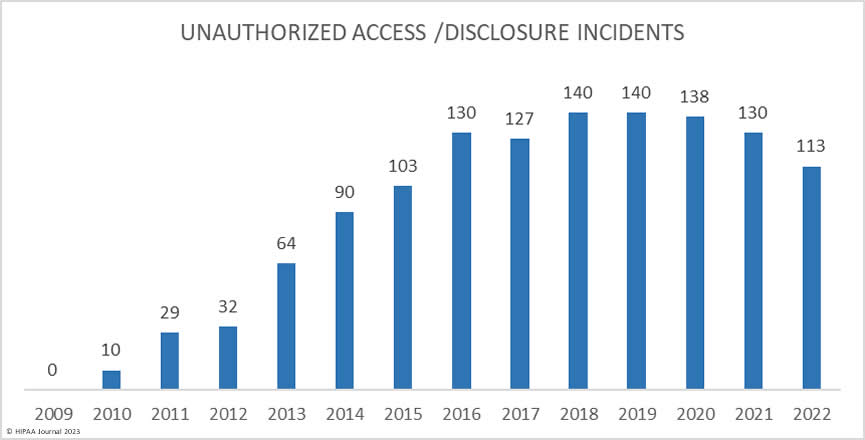
There were 113 reported unauthorized access/disclosure breaches reported in 2022, accounting for 14.5% of the breached records. The average breach size was 66,610 records due to some large pixel-related data breaches, and the median breach size was 1,652 records. Unauthorized access/disclosure incidents have been decreasing since 2019.
Theft (23 breaches) and loss (12 breaches) incidents were reported in relatively low numbers, continuing a downward trend from these once incredibly common data breaches. The downward trend is due to better control of devices and the use of encryption. The average breach size was 13,805 records and the median breach size was 1,704 records. There were four incidents involving the improper disposal of devices containing PHI and physical records. The average breach size was 1,772 records and the median was 1,021 records.
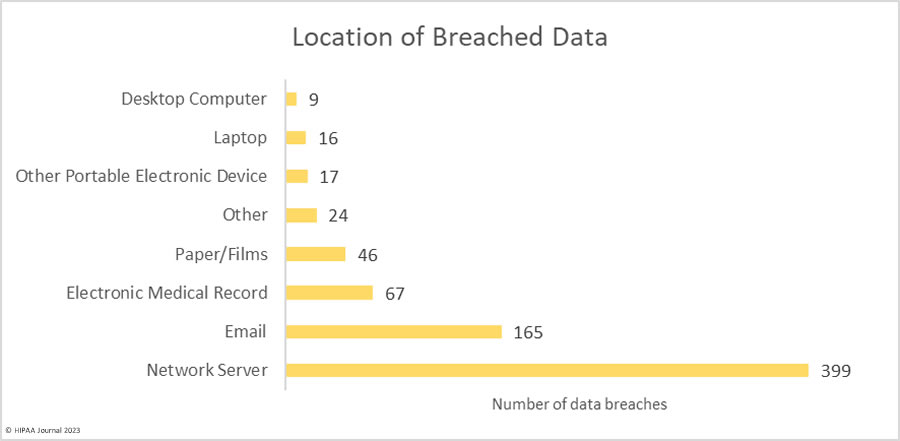
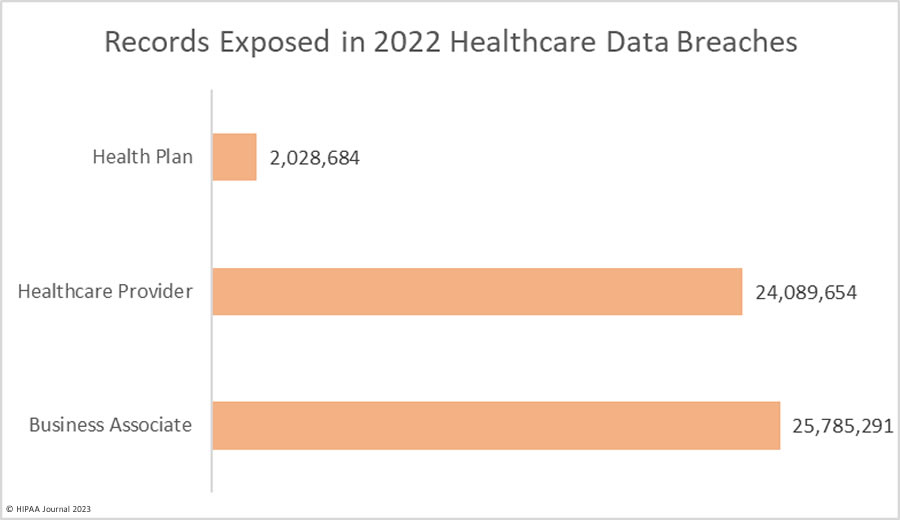
The high number of hacking incidents is reflected in the chart below, which shows the location of breached protected health information. Compromised email accounts remain a major source of data breaches, highlighting the importance of multi-factor authentication and training employees on how to recognize the signs of phishing.
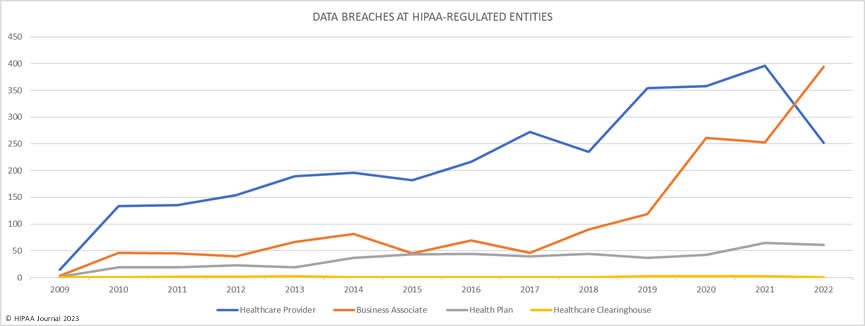
The raw data on the OCR breach portal does not accurately reflect the extent to which business associate data breaches are occurring. When you factor in business associate involvement it is possible to gain a more accurate gauge of the extent to which data breaches are occurring at business associates. In 2022, 127 data breaches were self-reported by business associates, but there were 394 reported data breaches where business associates were involved – That’s a 337% increase since 2018. Last year, data breaches at business associates outnumbered data breaches at healthcare providers for the first time.
Several major business associate data breaches were reported to OCR in 2022, with some of the data breaches affecting several hundred healthcare organizations. A data breach at the debt collections company, Professional Finance Company, affected 657 of its healthcare clients and involved more than 1.91 million healthcare records. Eye Care Leaders, a provider of electronic health records to eye care providers, suffered a cyberattack that affected at least 41 eye care providers and exposed the data of almost 3.65 million patients.
The graph below shows the sharp increase in data breaches at business associates in recent years. There are several reasons for the increase. Hackers have realized the value of conducting attacks on business associates. One successful attack can provide access to the data, and sometimes networks, of all of the vendor’s clients. Healthcare organizations are now using more vendors to manage administrative functions and risk increases in line with the number of vendors. As more vendors are used, it becomes harder to monitor cybersecurity at the vendors. Managing third-party risk is one of the biggest challenges for healthcare organizations in 2023.
Healthcare data breaches were reported by HIPAA-regulated entities in 49 states, Washington D.C., and Puerto Rico in 2022. Alaska was the only state to survive the year with no reported data breaches. In general, the most populated states suffer the most data breaches. In 2022, the 10 most populated U.S. states all ranked in the top 15 worst affected states, although it was New York rather than California that topped the list with 68 reported breaches.
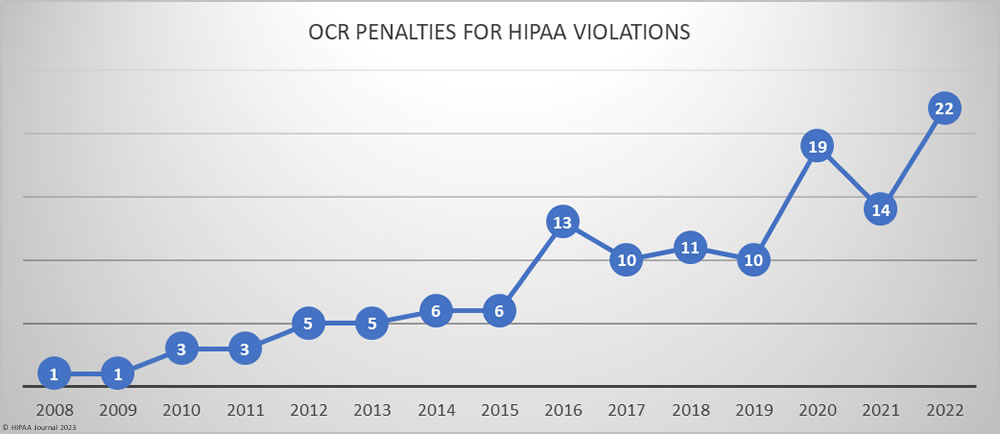
HIPAA is primarily enforced by OCR, with state attorneys general also assisting with HIPAA enforcement. OCR imposed more financial penalties for HIPAA violations in 2022 than in any other year to date, with 22 investigations resulting in settlements or civil monetary penalties.
OCR has limited resources for investigations but does investigate all breaches of 500 or more records. That task has become increasingly difficult due to the increase in data breaches, which have tripled since 2010. Despite the increase in data breaches, OCR’s budget for HIPAA enforcement has hardly increased at all, aside from adjustments for inflation. As of January 17, 2022, OCR had 882 data breaches listed as still under investigation. 97% of all complaints and data breach investigations have been successfully resolved.
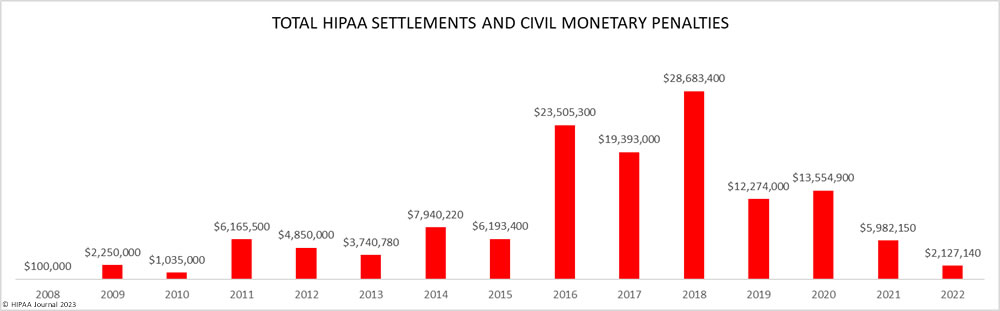
Some investigations warrant financial penalties, and while the number of penalties has increased, the penalty amounts for HIPAA violations have been decreasing. Most of the financial penalties in 2022 were under $100,000.
Since 2019, the majority of financial penalties imposed by OCR have been for HIPAA right of access violations, all of which stemmed from complaints from individual patients who had not been provided with their medical records within the allowed time frame. OCR continues to pursue financial penalties for other HIPAA violations, but these penalties are rare.
HIPAA enforcement by state attorneys general is relatively rare. Only three financial penalties were imposed in 2022 by state attorneys general. In these cases, penalties were imposed for violations of the HIPAA Rules and state laws.
Author: Steve Alder is the editor-in-chief of HIPAA Journal. Steve is responsible for editorial policy regarding the topics covered on HIPAA Journal. He is a specialist on healthcare industry legal and regulatory affairs, and has several years of experience writing about HIPAA and other related legal topics. Steve has developed a deep understanding of regulatory issues surrounding the use of information technology in the healthcare industry and has written hundreds of articles on HIPAA-related topics.
Delivered via email so please ensure you enter your email address correctly.
Your Privacy Respected
HIPAA Journal Privacy Policy
Delivered via email so please ensure you enter your email address correctly.
Your Privacy Respected
HIPAA Journal Privacy Policy
HIPAA Journal provides the most comprehensive coverage of HIPAA news anywhere online, in addition to independent advice about HIPAA compliance and the best practices to adopt to avoid data breaches, HIPAA violations and regulatory fines. HIPAA Journal’s goal is to assist HIPAA-covered entities achieve and maintain compliance with state and federal regulations governing the use, storage and disclosure of PHI and PII.
Receive weekly HIPAA news directly via email
HIPAA News
Regulatory Changes
Breach News
HITECH News
HIPAA Advice
Email Never Shared
Cancel Any Time
Privacy Policy
Copyright © 2014-2023 HIPAA Journal. All rights reserved.
Get Help With Your HIPAA Compliance
Eliminate Risk Of Non-Compliance
Your Privacy Respected Please see HIPAA Journal privacy policy
Get Help With Your
HIPAA Compliance
Your Privacy Respected
Please see HIPAA Journal privacy policy
For Individuals
Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunction’s Certificate Of Completion
Your Privacy Respected
HIPAA Journal Privacy Policy