The Home of the Security Bloggers Network
Home » Security Boulevard (Original) »
The global cost of cybercrime attacks is rising and reached an estimated €5.5 trillion in 2021. Ransomware attacks alone hit organizations somewhere in the world every 11 seconds. Our use of and dependence on technology grows each day and with it the opportunities for criminals to profit from emerging vulnerabilities. Despite increased awareness and growing spending by organizations to protect themselves and to build resilience in the event of a successful attack, specific cybersecurity threats will continue to rise in 2023. Cybersecurity risks will have to be mitigated by managing direct threats, but sufficient resources will be needed to navigate an increasingly complicated regulatory and operational environment in the coming year.
State-sponsored cybercrime and attacks are now one of the most prominent forms of cybercriminal activity, and will continue to rise in 2023. Nation-states take advantage of our increased dependence on technology to use cybercrime for espionage, sabotage or to sow misinformation. Meanwhile, some are turning a blind eye to cybercriminal groups within their borders that target the private sector, as long as those targets are in other countries.
In 2021, only a quarter of cyberattacks reported in Europe were directed at public administrations, while more than half targeted private-sector companies in a broad variety of sectors. The reasons targets are chosen are not always clear. For example, last month 14 U.S. airports suffered a denial-of-service (DoS) cyberattack that disrupted websites featuring flight information. Russian-speaking attackers took credit for the attack but the reasons for their actions remain unclear.
Private companies will need to closely monitor potential collateral damage caused by state-sponsored threat actors whose motives may not be obvious.
Globalization has dramatically increased the flow of goods throughout the world, but the rising interdependence for supplies and manufacturing processes also means that supply chains are stretched over greater distances and have become especially vulnerable to disruption. Already weakened from pandemic bottlenecks, the manufacturing sector has become an attractive target for attackers. In 2021, the number of supply chain intrusions rose 16% from the previous year.
Manufacturers and service providers often adopt new digital technology to quickly enhance productivity, but sometimes do so without paying sufficient attention to security issues. The introduction of robotics and the internet of things has provided attackers with new avenues to explore and exploit. One recent example is Toyota’s suspension of its Japanese production line last February due to a cyberattack directed not at Toyota itself but at one of its suppliers. The company had to delay the production of 13,000 vehicles as a result.
Cybercriminals monetize their activities via ransomware, and the tactic, which blocks access to systems or data until a ransom is paid, is being used on an ever-broader range of organizations and companies of all sizes. In 2021, there was a record 623 million ransomware attacks; far more than in previous years. Broader adoption of digital tools and remote working during the pandemic helps to explain the rise of attacks. More and more, criminals are using sophisticated phishing scams and targeted deep fakes, and the ubiquity of digital communication means attackers have more windows of opportunity to exploit.
Financial companies are prime targets for cybercriminals and frequent targets of cyberattacks. Financially motivated criminals attempt to infiltrate systems using tactics like server access, misconfigurations and fraud, often monetizing their activities through ransomware.
Almost one-third of successful breaches in the sector come from internal actors, in some cases employees unaware they are putting their company at risk. Adequate cybersecurity awareness training is key to avoiding incidents.
Insiders who knowingly aid cybercriminals, on the other hand, can be difficult to identify. To mitigate the threat from malicious insiders, cybersecurity systems need to take into account a broad range of information and be able to detect unusual or erratic user activity. Processes and controls must be established for granting access to sensitive data and followed closely at all times. User and entity behavior analytics (UEBA) can be critical to properly vetting new hires and keeping an eye out for unusual practices in the workplace.
The sense of alarm is growing among policymakers and regulators throughout the world of the threat to critical infrastructure and businesses that cybercrimes present, not to mention the risks to private citizens. New legislation to improve resilience and try to stem the growing tide of cyberincidents is beginning to appear which will require greater attention to an evolving regulatory landscape for cybersecurity.
Pressured into action by high-profile cybercrimes involving businesses and infrastructure, such as the Colonial Pipeline hack in 2021, the U.S. passed the Strengthening American Cybersecurity Act of 2022 in March 2022. The new legislation obligates companies to notify the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours of discovering a cybersecurity breach and within 24 hours of paying ransom to hackers. The law targets companies that provide critical infrastructure, but details of which companies the law will apply to and how it will be enforced have yet to be fully defined.
The new Digital Operational Resilience Act (DORA) was adopted by the European Parliament in November 2022 and introduced a comprehensive framework for the digital operational resilience of the financial sector. Almost all regulated financial institutions are in scope of DORA and will have to implement sufficient safeguards to protect against cyber and other ICT-related risks.
As the implications of these new laws become clearer and more countries follow with their own requirements, meeting the increasing cybersecurity-specific regulatory requirements across all countries and regions where companies operate will be a growing challenge for cybersecurity managers in 2023.
Unfortunately, the increased use of technology and the rise of cybercrime attacks has not brought with it an increase in the number of qualified cybersecurity professionals available to address the problems. Attracting and retaining the right talent has been a challenge for companies and will continue to be in the future.
Recruiting professionals with the needed skill set is critical, but just as important is retaining talent once they are on board. Many cybersecurity professionals want to work at organizations where their opinions will be taken seriously by top management, where well-defined cybersecurity governance and automation are in place and where cybersecurity training and investment throughout the organization is a key priority. Many want to feel challenged to design new solutions and to connect with the core purpose of the company they work for. Organizations have to focus not just on filling their specific needs but on meeting the expectations for career development and purpose of the cybersecurity talent they depend on.
Overcoming the cybersecurity threats and attacks that lie ahead will take more than stamina to confront the day-to-day battles. Broad vision is critical in order to keep up with an environment in constant evolution and to cultivate adequate resources to help in the fight.
Eric Schifflers is Ria Money Transfer’s CISO. Ria Money Transfer, a business segment of Euronet Worldwide, Inc. (NASDAQ: EEFT), delivers innovative financial services including fast, secure, and affordable global money transfers to millions of customers along with currency exchange, mobile top-up, bill payment and check cashing services, offering a reliable omnichannel experience. The company is steadfast in its commitment to serve its customers and the communities in which they live, opening ways for a better everyday life.
eric-schifflers has 1 posts and counting.See all posts by eric-schifflers
More Webinars 

Author: rescue@crimefire.in
-
The Most Pressing Cybersecurity Challenges of 2023 – Security Boulevard
-
Creating an Employee Cybersecurity Training Program – CrowdStrike
November 9, 2022
If you think your small business is not a target for hackers and cybercriminals — think again. An estimated 50-70% of ransomware attacks target small- and medium-sized businesses[1], likely because adversaries believe smaller organizations do not have robust security measures in place to defend the business and its data.
While cybercriminals rely on a variety of methods to attack a company, one of the most common — and often easiest — is by targeting employees through coordinated phishing attacks or other social engineering techniques.
To minimize this risk, small- and medium-sized businesses need to develop an employee cybersecurity training program that will educate their people about common security risks, promote responsible online behavior and outline steps to take when they believe an attack may be in progress.
Small businesses are often easy prey for cybercriminals on the hunt for sensitive business data and customer information. With CrowdStrike, you get enterprise level-protection and support at a price you can afford – because every SMB deserves protection, regardless of headcount.View cybersecurity solutions for SMBs
Before employee training programs can be developed, your business must have a clear sense of its cybersecurity strategy, as well as the people, processes and technologies that will execute the security program. Here we review the essential elements of the cybersecurity architecture.
A wide variety of solutions and services are available on today’s cybersecurity market. While a trusted and reputable cybersecurity partner can help businesses develop a custom toolset to meet their unique needs, every cybersecurity platform should start at a baseline with antivirus protection.
While cost is a concern for many small business owners, it is important to find solutions that provide the right level of protection at the right budget with the right technology. Learn how to start building a robust cybersecurity plan to meet the specific needs of small businesses.Download: Cybersecurity for Small Businesses: Proactive solutions that meet your need
An incident response plan is a document that outlines an organization’s procedures, steps and responsibilities to prepare for, detect, contain and recover from a data breach.
Even small businesses should develop a clear acceptable use policy for employees who use corporate devices and networks, or have access to data and other sensitive assets. This would include listing the different software applications, programs, websites and social media platforms that are allowed to be accessed with a company device or via a corporate network, as well as the steps that need to be taken to secure and protect the device and its data.
As part of this process, it may also be helpful to outline unacceptable behaviors and prohibited activity.
EXAMPLE: A company’s IT policy should make clear that employees are not allowed to install unlicensed software on any company computer, phone or other device or to download files or programs, such as music, movies, games or other applications. This is because unlicensed software downloads, or any file download, could make the company susceptible to cyberattacks.
Cybersecurity awareness training should be a mandatory task completed by every employee, regardless of level, location or job scope. That said, it may be wise to tailor learning programs based on job type or level of experience, as well as location.
The training program may be adapted for the following audiences:
The training program should cover common and significant cyber threats. These include:
Social engineering is one of the most common methods of cyberattack, where a hacker tricks an employee into sharing sensitive data or credentials by posing as another legitimate employee or partner. For example, a hacker may pose as a help desk agent to ask a user for sensitive information, such as a username and password.
Phishing is a type of social engineering cyberattack that uses email, text message, phone call or social media to entice a victim to share sensitive information — such as passwords or account numbers — or to download a malicious file that will install viruses on their computer or phone.
When creating your training program, include real-life examples of a phishing attack to educate your employees on the main key indicators like you’ll see in the example below: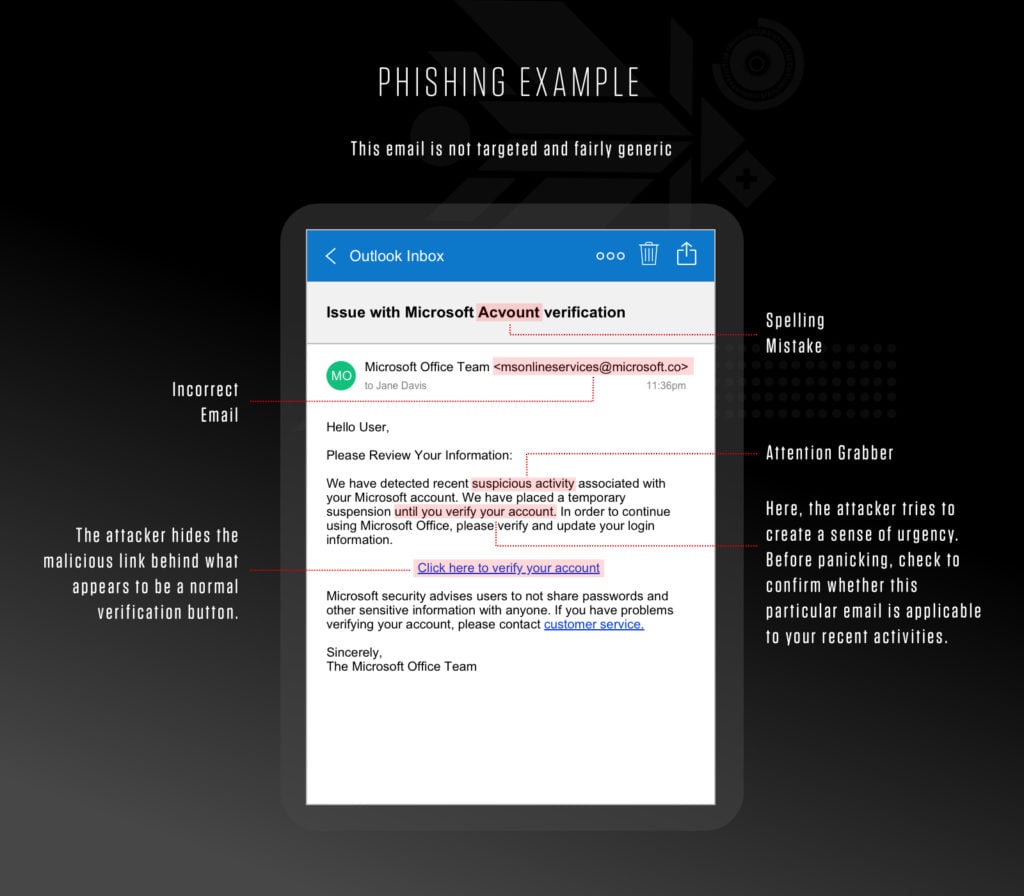
Attackers are constantly after user IDs, email addresses and passwords because these items enable them to pose as a legitimate user to avoid detection while they carry out an attack.
Once the hacker has your credentials they can access any service or network the account is entitled to. One of the best ways to reduce the risk of password compromise is to require users to create strong passwords. Below are examples of strong passwords.
Strong passwords are:
Long, complex, random passwords are exponentially more difficult for password cracking tools to breach. In addition, frequently updated passwords limit the amount of time adversaries have available to crack password hashes.
An insider threat is a cybersecurity risk that comes from within the organization. This is usually a current or former employee or other person who has direct access to the company network, sensitive data and intellectual property.
Typically an insider is financially motivated to lead or take part in a malicious act. These attacks usually involve theft of data or trade secrets which can be sold on the dark web or to a hostile third party. Luckily, there are ways to mitigate insider threats for SMBs, which include continuously monitoring your network and educating employees on all company policies regarding cybersecurity practices.
Every internet-connected device can be the entry point for an attack. Your cybersecurity training program should share best practices for how employees can keep their devices safe, as well as how to install and update the security tools used by the organization.
Social media can be another avenue for cybercriminals to connect with employees, gather personal information and otherwise exploit personal relationships to advance an attack using social engineering techniques. While companies generally cannot prohibit employees from using social media on their own time using their own devices, they can construct clear policies that limit use on company devices or the corporate network.
The main goal of every cybersecurity program is to keep the organization and its assets safe. This includes data of all kinds — including sensitive customer data and intellectual property.
In many cases, employees who handle sensitive customer data, such as personal information, bank details or health records, are required by law to complete cybersecurity training. Organizations that are subject to such regulations should ensure that the training program they develop meets the requirements dictated by government or industry groups.
Cybersecurity must be seen as a company-wide effort. It is important the program has dedicated leadership from IT and HR to ensure training modules are properly developed and rolled out to the appropriate audiences.
As part of this process, the CEO, CFO, IT lead and HR manager should also coordinate on all aspects of program management, including budget. This will help ensure that cybersecurity remains an important part of the company’s ongoing operations and is supported with the proper resources and investments.
As with any new training program, it may be helpful to conduct an initial pilot of the program with a subset of employees and gather feedback about the program content and user experience.
When rolling out the program to your employees, it will be important to track completion rates and test knowledge through both a completion quiz and regular cybersecurity testing, such as a simulated phishing email.
All basic training should be conducted annually in order to refresh employees’ knowledge and keep best practices top-of-mind.
Don’t let the size of your business or your budget stand in the way of developing a strong security defense. CrowdStrike Falcon® Go is an easy-to-manage and affordable solution that prevents ransomware, malware and the latest cyber threats.
Start a free, 15-day trial of Falcon Pro and protect your business from ransomware, malware and sophisticated cyberattacks.
[1] U.S. Secretary of Homeland Security Alejandro Mayorkas in Inc., 2021 -
Debunking Common Cyber-Security Myths – Security Boulevard
The Home of the Security Bloggers Network
Home » Promo » Cybersecurity »
Cybersecurity is a critical issue that affects everyone who uses the internet, both individuals and corporations. Unfortunately, there are many myths and misconceptions about what does and does not work when it comes to protecting yourself online. In this article, I will debunk some of the most common cybersecurity myths. I’ll also provide some tips on what you can do to keep your staff and your information safe.

Many people believe that Macs are immune to viruses, and therefore don’t need to worry about installing antivirus software. This is simply not true. While it is true that Macs are less vulnerable to viruses than PCs, they are not completely immune. In fact, malware and other types of cyber threats have been found on Macs. In light of this, it is important to take steps to protect yourself. This includes installing antivirus software and keeping it up to date, as well as practicing safe browsing habits.
Antivirus software is a valuable tool in the fight against cyber threats, but it is not a catch-all solution. There are many different types of cyber threats, and antivirus software may not protect against all of them. For example, antivirus software may not protect against social engineering attacks, such as phishing scams, or credential harvesting attacks. In addition to installing antivirus software, it is important for employees to practice safe browsing habits, keep your operating system and software up to date, and be trained on the latest cyber threats they may encounter. Providing your staff with awareness training on tactics like elicitation and rapport building, as well as critical thinking, can help them stay on guard against social engineering attacks.

Public Wi-Fi can be convenient, but it’s important to be aware of the risks. Public Wi-Fi networks are often unsecured, which means that anyone on the same network can potentially see the data you’re sending and receiving or can be controlled by malicious actors to redirect legitimate traffic to malicious websites. However, this does not mean that you can never use public Wi-Fi for personal or professional use. When it comes to your employees, it is best to err on the side of caution. Staff should be aware of the dangers in using work computers and accessing company data on public networks. It is highly recommended that employees use a company Virtual Private Network (VPN) to connect to corporate resources. This will encrypt the traffic and help secure your internet connection on public networks.
Many people believe that passwords need to be changed regularly. Some companies even rotate their credentials annually, bi-annually, or even quarterly. Though the logic seems intuitive, updated information tends to say the opposite. Experts advise that unless you become aware of a password breach or compromise, there is no need to change your passwords regularly IF they are strong, unique passwords for each service you use. Yes, having strong and unique passwords is much more important to help increase the security of your credentials. It is beneficial for any company to ensure their staff is using these characteristics. The use of both multi-factor authentication and a credible password manager can help strengthen your security defenses by adding additional layers of protection to login procedures. Password managers especially can assist if a cyber attack takes place, and the need arises to change out compromised passwords for another strong and unique one.
Finally, some people believe that multifactor authentication (MFA) is too inconvenient, and therefore choose not to use it. However, MFA is a very simple and effective way to add an extra layer of security to your accounts and make it more difficult for a threat actor to access information systems. There are also three main types of MFA methods:
What you know, such as answers to personal security questions or additional secret passwords.
Things you have, such as one-time passwords (OTP) generated by smartphone apps, access badges, USB devices, or software tokens and certificates.
Things you are, such as fingerprints, facial recognition, voice, retina, or iris scanning.
While it may add a few extra seconds to login procedures or access protocols, the added security is well worth the inconvenience. In the event credentials ever become compromised due to cyber or social engineering attacks, MFA will prove to be another challenge for the attacker, as they would need something their target knows, has or is for the password to even be worthwhile. Without MFA, the attacker would immediately have access to internal systems. As mentioned in Myth 4, MFA provides an extra layer of protection for employees.

This Article has debunked several common myths regarding cybersecurity. Understanding what is untrue, or does not work, helps us to see what does work to improve our security.
By following these tips, you can protect yourself and your valuable information online. Corporations do well to correct any such myths discussed in this article that may circulate in the workplace. Remember, cybersecurity is everyone’s responsibility, and it is important to be vigilant to keep yourself safe.
Josten Peña
At Social Engineer LLC, our purpose is to bring education and awareness to all users of technology. For a detailed list of our services and how we can help you achieve your information/cybersecurity goals please visit:
https://www.Social-Engineer.com/Managed-Services/
Images:
https://cdn.stocksnap.io/img-thumbs/960w/woman-thinking_MLZIHL9GLY.jpg
https://cdn.mos.cms.futurecdn.net/cAdRiWzdJDySUS2z6NsqG6.jpg
https://kbigroup.com.au/wp-content/uploads/2020/07/Essential-Policies-Procedures-Post.jpg
*** This is a Security Bloggers Network syndicated blog from Social-Engineer, LLC authored by Social-Engineer. Read the original post at: https://www.social-engineer.com/debunking-common-cyber-security-myths/
More Webinars

-
Popular background check services suffer data breach – Do this – Komando
Have you ever done a background check on yourself or someone else? It’s a good way for employers to determine if a potential worker is trustworthy. Some people even do background checks on potential dates in online dating. Tap or click here to learn how to do a free background check.
But your data might be in jeopardy if you’ve used a popular background check service. A data breach exposed information from over 20 million users of a couple of the most popular services.
Keep reading for details on the breach and ways to protect your data.
TruthFinder and Instant Checkmate are websites that offer background check services to their subscribers. They gather information from various publicly accessible sources, including court records, criminal records, social media and others to provide detailed background reports on individuals.
The two companies merged with PeopleConnect Holdings in 2020. Recently, a hacking collective claimed to have stolen a TruthFinder and Instant Checkmate user database and shared it for free on criminal forums.
Learn the tech tips and tricks only the pros know.
The database contains the details of over 20 million users who used the services from 2011 to 2019. Leaked data includes names, email addresses, phone numbers and hashed passwords.
Soon after the hacker shared the details, parent company PeopleConnect acknowledged the breach. “We have confirmed that the list was created several years ago and appears to include all customer accounts created between 2011 and 2019. The published list originated inside our company,” the company explains.
Users of the background check services during the dates in question should be careful about any emails that might seem suspicious. The company stresses that TruthFinder and Instant Checkmate will never ask for your password, Social Security number or payment information over email or phone. If that happens, it is probably a scammer.
When there is a massive data breach like this, there are safety precautions you should take.
Steps to take following a data breach.
To see if your details are part of a data breach, Have I Been Pwned is an excellent resource. Enter your email address, and the website lets you know how many and which breaches your email address was in. Tap or click here for more details on how the site works.
Genealogy site data breach: See if your info was leaked
Twitter data breach: Personal details of 5.4M users leaked
More:
Don’t want to lose your dough to crypto? Check out my new eBook, “Cryptocurrency 101.” I walk you through buying, selling, mining and more!
source -
Meta Fined For 2021 Data Breach As Millions Of Twitter Users’ Data Also Leaked – Forbes
A massive data breach may have affected some 5.4 million Twitter user accounts containing non-public … [+]
A massive data breach may have affected some 5.4 million Twitter user accounts containing non-public information in Europe and the United States. The data was reportedly stolen using an API vulnerability and shared for free on a hacker forum. Though the vulnerability has reportedly been fixed, another massive, even potentially more significant data dump of millions of Twitter records has also been disclosed by security researchers.
According to a report from Bleeping Computer, the data consists of scraped public information as well as private phone numbers and email addresses that are not meant to be public. Multiple threat actors had been utilizing a bug to steal private information.
That bug was discovered by HackerOne during a bug bounty earlier this year, and apparently addressed, but it remains unclear if that disclosure had also been leaked.
“This breach showcases how quickly criminals move whenever there is a vulnerability, particularly in a large social media site,” explained Javvad Malik, security awareness advocate at KnowBe4, via an email. “With so much information disclosed, criminals could quite easily use it to launch convincing social engineering attacks against users. This could be not only to target their Twitter accounts, but also via impersonating other services such as online shopping sites, banks, or even tax offices.”
Security researcher Avishai Avivi, CISO at SafeBreach, warned that API attacks are going to become more prominent in the near future and plague the companies relying on APIs for years to come. This is because APIs are meant to be used by systems to communicate with each other and exchange massive amounts of data – and as a result, these interfaces represent an alluring target for malicious actors to abuse.
“While API weaknesses may be more challenging to discover, once an adversary gains access to an improperly designed API, they essentially have direct access to the organization’s databases,” said Avivi. “This is also why when a breach occurs through an API, we will see millions of records being impacted.”
Moreover, API vulnerabilities also do not need human interaction – such as clicking on a malicious link, or falling for a phishing email).
“The positive side of API vulnerabilities is that they are typically unique to the organization using it. Unlike traditional software vulnerabilities, the malicious actor cannot use the same vulnerability to attack a different organization,” added Avivi.
That is likely of little comfort for the millions of Twitter users whose data may now be offered for free on the dark web.
Meta Handed Quarter Billion Dollar Fine
The news of the Twitter breach is noteworthy as Ireland’s Data Protection Commission (DPC) also handed down a $265 million fine to Facebook parent Meta for a data breach that impacted millions of users of the social network in 2021. The information from “scraped data” had apparently included phone numbers, Facebook IDs, names, locations, DOBs, and email addresses.
“Every single one of the 533 million Facebooks users whose information was published on hacking forums faced potential follow-up phishing scams exploiting their exposed PII (Personal Identifiable Information) in the pursuit of more valuable credentials,” said John Stevenson, product director at cybersecurity firm Cyren, via an email.
“So, whilst the initial data leak was back in 2021, it’s nonetheless encouraging to see fines being issued retrospectively,” Stevenson added. “Hopefully, the consequences here will encourage other enterprises to comply with cyber regulations and follow best practices to avoid a mercenary penalty in the future, particularly given cyber insurers increasingly setting a higher bar for due diligence to avoid extortionate payouts like this one.”
It is too early to know if Twitter will be facing a similar fine for its recent data breach. -
This 9-Course Bundle Can Take Your Cybersecurity Skills to the Next Level – The Hacker News
If you regularly read The Hacker News, there’s a fair chance that you know something about cybersecurity. It’s possible to turn that interest into a six-figure career. But to make the leap, you need to pick up some key skills and professional certifications.
Featuring nine in-depth courses, The 2022 Masters in Cyber Security Certification Bundle helps you get ready for the next step. And in a special reader offer, you can get lifetime access for only $39.99.
Special Offer — This bundle contains nine courses with a total value of $1,800. But for a limited time, you can get lifetime on-demand access for only $39.99. That is a massive 97% off MSRP!
From penetration testing to threat analysis, there are thousands of vacant roles in the cybersecurity industry right now. What’s more, this trend is set to continue, with experts predicting a 12% growth within the industry in the remainder of this decade.
The really exciting part is that anyone can land a highly paid job within this niche — you just need to prove your knowledge with professional certifications. The 2022 Masters in Cyber Security Certification Bundle helps you do just that, with 681 individual video lessons that help you prepare for key exams and pick up real-world knowledge.
Along the way, you learn about the most common vulnerabilities that are utilized by black hat hackers today. You also discover ethical hacking and penetration testing techniques, together with risk management and disaster recovery protocols.
Just as importantly, the training provides full prep for CISSP, CISM, CISA, and other important exams. Plus, you even get an entire course dedicated to IT interviews — really helpful when it comes to securing your first job.
All the included content comes from highly-rated instructors, such as Mohamed Atef. He is a senior penetration tester, and a certified IT instructor with more than 20 years of experience. In that time, he earned a rating of 4.6 out of 5 stars from students.
Order today for only $39.99 to get lifetime on-demand access to all nine courses, normally worth $1,800 in total!
Prices subject to change
Sign up for free and start receiving your daily dose of cybersecurity news, insights and tips. -
Cybersecurity Trends & Statistics For 2023: More Treachery And Risk Ahead As Attack Surface And Hacker … – Forbes
Vector of Moving Forward
Every year I peruse emerging statistics and trends in cybersecurity and provide some perspective and analysis on the potential implications for industry and government from the data. While cybersecurity capabilities and awareness seem to be improving, unfortunately the threat and sophistication of cyber-attacks are matching that progress.
The 2023 Digital Ecosystem
Blue glowing futuristic technology, computer generated abstract background, 3D render
The emerging digital ecosystem is treacherous. In our current digital environment, every company is now a reachable target, and every company, large or small, has operations, brand, reputation, and revenue pipelines that are potentially at risk from a breach.
For 2023 and beyond the focus needs to be on the cyber-attack surface and vectors to determine what can be done to mitigate threats and enhance resiliency and recovery. As the interest greatly expands in users, so do the threats, As the Metaverse comes more online it will serve as a new vector for exploitation. Artificial intelligence and machine learning, while great for research & analytics (i.e. ChatGPT). However, AI tools can also be used by hackers for advanced attacks. Deep fakes are already being deployed and bots are continuing to run rampant. and the geopolitics of the Russian invasion of Ukraine has highlighted the vulnerabilities of critical infrastructure (CISA Shields Up) by nation-state threats, including more DDSs attacks on websites and infrastructure. Most ominous was the hacking of a Ukrainian satellite.
Here are some initial digital ecosystem statistics to consider: According to a Deloitte Center for Controllership poll. “During the past 12 months, 34.5% of polled executives report that their organizations’ accounting and financial data were targeted by cyber adversaries. Within that group, 22% experienced at least one such cyber event and 12.5% experienced more than one.” And “nearly half (48.8%) of C-suite and other executives expect the number and size of cyber events targeting their organizations’ accounting and financial data to increase in the year ahead. And yet just 20.3% of those polled say their organizations’ accounting and finance teams work closely and consistently with their peers in cybersecurity.” Nearly half of executives expect cyber-attacks targeting accounting, other systems Nearly half of executives expect cyber attacks targeting accounting, other systems (northbaybusinessjournal.com)
Cyber-Trends:
AI, Artificial Intelligence concept,3d rendering,conceptual image.
AI and ML Making Impacting the Cyber-Ecosystem in a big Way in 2023 and Beyond
International Data Corporation (IDC) says AI in the cybersecurity market is growing at a CAGR of 23.6% and will reach a market value of $46.3 billion in 2027 Please see: Experts predict how AI will energize cybersecurity in 2023 and beyond | VentureBeat
My Take: AI and ML can be valuable tools to help us navigate the cybersecurity landscape. Specifically it can (and is being) used to help protect against increasingly sophisticated and malicious malware, ransomware, and social engineering attacks. AI’s capabilities in contextual reasoning can be used for synthesizing data and predicting threats.
They enable predictive analytics to draw statistical inferences to mitigate threats with less resources. In a cybersecurity context, AI and ML can provide a faster means to identify new attacks, draw statistical inferences and push that information to endpoint security platforms.
While AI and ML can be important tools for cyber-defense, they can also be a two edged sword. While it can be used to rapidly identify threat anomalies and enhance cyber defense capabilities, it can also be used by threat actors. Adversarial Nations and criminal hackers are already using AI and MI as tools to find and exploit vulnerabilities in threat detection models.
Cyber criminals are already using AI and machine learning tools to attack and explore victims’ networks. Small business, organizations, and especially healthcare institutions who cannot afford significant investments in defensive emerging cybersecurity tech such as AI are the most vulnerable. Extortion by hackers using ransomware and demanding payment by cryptocurrencies may become and more persistent and evolving threat. The growth of the Internet of Things will create many new targets for the bad guys to exploit. There is an urgency for both industry and government to understand the implications of the emerging morphing cyber threat tools that include AI and ML and fortify against attacks.
Please also see the recent FORBES article discussing three key applications of artificial intelligence for cybersecurity including, Network Vulnerability Surveillance and Threat Detection, Incident Diagnosis and Response, and applications for Cyber Threat Intelligence Reports: Three Key Artificial Intelligence Applications For Cybersecurity by Chuck Brooks and Dr. Frederic Lemieux Three Key Artificial Intelligence Applications For Cybersecurity by Chuck Brooks and Dr. Frederic Lemieux (forbes.com)
Cyber-Crime and the Cyber Statistics to Explore so Far in 2023
A close-up on an abstract design of a display, which is warning about a cyber attack. Multiple rows … [+]
Cyber-crime is growing exponentially. According to Cybersecurity Ventures, the cost of cybercrime is predicted to hit $8 trillion in 2023 and will grow to $10.5 trillion by 2025. Please see: eSentire | 2022 Official Cybercrime Report There are many factors for such growth and some of them will be explored in more detail below.
Programming code abstract technology background of software developer and Computer script
Open Source Vulnerabilities Found in 84% of Code Bases
It starts with open source code. Unfortunately, according to Synopsys researchers, at least one open source vulnerability was found in 84% of code bases. The vulnerability data was included in Synopsys’ 2023 Open Source Security and Risk Analysis (OSSRA) report on 2022 data. Since most software applications rely on open source code, this is still a significant cybersecurity issue to address.
The report noted: “open source was in nearly everything we examined this year; it made up the majority of the code bases across industries,” the report said, adding that the code bases contained troublingly high numbers of known vulnerabilities that organizations had failed to patch, leaving them vulnerable to exploits. All code bases examined from companies in the aerospace, aviation, automotive, transportation, and logistics sectors contained some open source code, with open source code making up 73% of total code. “
As significant as the risks from the open source code are, they can be detected by penetration testing and especially by patching. The report found that patches clearly are not being appplied. It cited that “of the 1,481 code bases examined by the researchers that included risk assessments, 91% contained outdated versions of open-source components, which means an update or patch was available but had not been applied.”
Please see: At least one open source vulnerability found in 84% of code bases: Report At least one open source vulnerability found in 84% of code bases: Report | CSO Online
On way that hackers take advantage of code vulnerabilities and open source flaws is via zero-day exploits. Recently a ransomware gang used a new zero-day flaw to steal data on 1 million hospital patients. “Community Health Systems (CHS), one of the largest healthcare providers in the United States with close to 80 hospitals in 16 states, confirmed this week that criminal hackers accessed the personal and protected health information of up to 1 million patients. The Tennessee-based healthcare giant said in a filing with government regulators that the data breach stems from its use of a popular file-transfer software called GoAnywhere MFT.” Clop claims it mass-hacked 130 organizations, including a US hospital network
My Take: as a remedy to avoid vulnerability exploits and keep open source code updated, the report suggested that organizations should use a Software Bill of Materials (SBOMS) . I agree, in addition to Pen testing, SBOMS are an important way to map systems and organize to be more cyber secure. An SBOM is basically a list of ingredients that make up software components and serves as a formal record containing the details and supply chain relationships of various components used in building the software. I wrote about this extensively in a previous FORBES article.
In the article, Dmitry Raidman. CTO, of a company called Cybeats offered insights into l specific use cases for SBOMS. They include transparency into software provenance and pedigrees, continuous security risk assessment, access control and sharing with customer who can access and what data can be seen, threat intelligence data correlation, software composition license analysis and policy enforcement, software component end of life monitoring, SCRM – Supply Chain Risk Management and supply chain screening, SBOM documents repository and orchestration, efficiency in data query and retrieval.
Clearly, SBOMS are a good path forward in discovering and correcting open source vulnerabilities in code. Please see: Bolstering Cybersecurity Risk Management With SBOMS Bolstering Cybersecurity Risk Management With SBOMS (forbes.com)
PHISHING Button on Computer Keyboard
Phishing Continues to be a preferred Method of Hackers in 2023
Phishing is still the tool of choice for many hackers. Phishing is commonly defined as a technique of hackers to exfiltrate your valuable data, or to spread malware. Anyone can be fooled by a targeted phish, especially when it appears to be coming as a personal email from someone higher up the work chain, or from a bank, organization, or a website you may frequent.
Advances in technology have made it easier for hackers to phish. They can use readily available digital graphics, apply social engineering data, and a vast array of phishing tools, including some automated by machine learning. Phishing is often accompanied by ransomware and a tactic for hackers is to target leadership at companies or organizations (spear-phishing) because they usually have better access to valuable data and make ready targets because of lack of training.
According to the firm Lookout, the highest rate of mobile phishing in history was observed in 2022, with half of the mobile phone owners worldwide exposed to a phishing attack every quarter. The Lookout report was based on Lookout’s data analytics from over 210 million devices, 175 million apps, and four million URLs daily. The report noted that “non-email-based phishing attacks are also proliferating, with vishing (voice phishing), smishing (SMS phishing), and quishing (QR code phishing) increasing sevenfold in the second quarter of 2022. And that “the damage can be colossal for businesses that fall victim to mobile phishing attacks: Lookout calculated that the potential annual financial impact of mobile phishing to an organization of 5000 employees is nearly $4m.
The report also noted that “Cybercriminals mostly abused Microsoft’s brand name in phishing attacks, with more than 30 million messages using its branding or mentioning products like Office or OneDrive. However, other companies were also frequently impersonated by cybercriminals, including Amazon (mentioned in 6.5 million attacks); DocuSign (3.5 million); Google (2.6 million); DHL (2 million); and Adobe (1.5 million).”
Please see: Record Number of Mobile Phishing Attacks in 2022 Record Number of Mobile Phishing Attacks in 2022 – Infosecurity Magazine (infosecurity-magazine.com)
3D rendering Glowing text Ransomware attack on Computer Chipset. spyware, malware, virus Trojan, … [+]
Ransomware and Phishing: the current state of cyber-affairs is an especially alarming one because ransomware attacks are growing not only in numbers, but also in the financial and reputational costs to businesses and organizations.
Currently, ransomware, mostly via phishing activities, is the top threat to both the public and
private sectors. Ransomware allows hackers to hold computers and even entire networks hostage for electronic cash payments. In the recent case of Colonial Pipeline, a ransomware attack disrupted energy supplies across the east coast of the United States.
“In 2022, 76% of organizations were targeted by a ransomware attack, out of which 64% were actually infected. Only 50% of these organizations managed to retrieve their data after paying the ransom. Additionally, a little over 66% of respondents reported to have had multiple, isolated infections.” Please see: New cyberattack tactics rise up as ransomware payouts increase New cyberattack tactics rise up as ransomware payouts increase | CSO Online
My Take: Since most of us are now doing our work and personal errands on smartphones, this is alarming data. But there are remedies. Training employees to identify potential phishing emails is the first step in prevention, but many of the obvious clues, such as misspelled words and poor grammar, are no longer present. Fraudsters have grown more sophisticated, and employees need to keep up with the new paradigm.
Human errors are inevitable, however, and some employees will make mistakes and accidentally fall victim to phishing. The backup system at that point should include automated systems that can silo employee access and reduce damage if a worker’s account is compromised. The best way is to establish and monitor administrative privileges for your company. You can limit employee access or require two [authentication] steps before they go there. A lot of companies will also outlaw certain sites that workers can’t go visit, so it makes it more difficult to get phished.
My additional advice to protect against phishing and ransomware, is to make sure you backup your valuable data (consider encrypting it too), preferably on another device segmented from the targeted PC or phone. If you are a small business or an individual, it is not a bad idea to invest in anti-phishing software. It adds another barrier. I also recommend monitoring your social accounts and credit accounts to see if there are any anomalies on a regular basis.
Creative abstract postal envelopes sketch on modern laptop background, e-mail and marketing concept. … [+]
Business E-mail Compromise
Often done in coordination with phishing, business email compromise is still a serious cybersecurity issue. A research company Trellix determined 78% of business email compromise (BEC) involved fake CEO emails using common CEO phrases, resulting in a 64% increase from Q3 to Q4 2022. Tactics included asking employees to confirm their direct phone number to execute a voice-phishing – or vishing – scheme. 82% were sent using free email services, meaning threat actors need no special infrastructure to execute their campaigns. Please see: Malicious actors push the limits of attack vectors Malicious actors push the limits of attack vectors – Help Net Security
“Seventy-five percent of organizations worldwide reported an attempted business email compromise (BEC) attack last year. While English remained the most common language employed, companies in a few non-English nations witnessed a higher volume of attacks in their own languages, including organizations in the Netherlands and Sweden, which reported a 92% jump in such attacks; in Spain, with a 92% jump; Germany, with an 86% increase; and France, with an 80% increase.” Please see: New cyberattack tactics rise up as ransomware payouts increase New cyberattack tactics rise up as ransomware payouts increase | CSO Online
“Business Email Compromise (BEC) attacks are no longer limited to traditional email accounts. Attackers are finding new ways to conduct their schemes — and organizations need to be prepared to defend themselves. Attackers are leveraging a new scheme called Business Communication Compromise to take advantage of large global corporations, government agencies and individuals. They are leveraging collaboration tools beyond email that include chat and mobile messaging — including popular cloud-based applications such as Slack, WhatsApp, LinkedIn, Facebook, Twitter and many more — to carry out attacks.” Please see: The evolution of business email compromise to business communication compromise The evolution of business email compromise to business communication compromise (betanews.com)
My Take: business emails have been a top target of hackers. Accordingly, organizations need to create a corporate risk management strategy and vulnerability framework that identifies digital assets and data to be protected, including sensitive emails. Such as risk management strategy should be holistic and include people, processes, and technologies. This includes protecting and backing up email data, and the business enterprise systems such as financial systems, email exchange servers, HR, and procurement systems with new security tools (encryption, threat intel and detection, Identity Access Management, firewalls, etc.) and policies. That risk management approach must also include knowing your inventory and gaps, integrating cybersecurity hygiene practices, procuring, and orchestrating an appropriate cyber-tool stack.
Fraud Alert in red keys on high-tech computer keyboard background with security engraved lock on … [+]
Fraud is Trending Digital, Especially Identity Theft
Fraud has always been a societal problem, but it is being compounded by the expansion of criminals in the digital realm. The cost is going higher as more people do their banking and buying online.
Federal Trade Commission (FTC) data shows that consumers reported losing nearly $8.8 billion to fraud in 2022, an increase of more than 30 percent over the previous year. Much of this fraud came from fake investing scams and imposter scams. Perhaps most alarming in this report was that there were over 1.1 million reports of identity theft received through the FTC’s IdentityTheft.gov website. FTC reveals alarming increase in scam activity, costing consumers billions – Help Net Security
My take: the reason for the increased rate of identity fraud is clear. As we become more and more connected, the more visible and vulnerable we become to those who want to hack our accounts and steal our identities. The surface threat landscape has expanded exponentially with smartphones, wearables, and the Internet of Things. Moreover, those mobile devices, social media applications, laptops & notebooks are not easy to secure.
There are no complete remedies to identity theft but there are actions that can enable people and companies to help deter the threats. Below is a quick list of what you can to help protect your accounts, privacy, and reputation:
1) Use strong passwords. Hackers are quite adept at guessing passwords especially when they have insights into where you lived in the past (street names), birthdays and favorite phrases. Changing your password regularly can also complicate their tasks.
2) Maintain a separate computer to do your financial transactions and use it for nothing else.
3) Consider using encryption software for valuable data that needs to be secured. Also set up Virtual Private Networks for an added layer of security when using mobile smartphones.
4) Very important; monitor your credit scores, your bank statements, and your social accounts on a regular basis. Life Lock and other reputable monitoring organizations provide account alerts that are very helpful in that awareness quest. The quicker you detect fraud the easier it is to handle the issues associated with identity theft.
5) If you get breached, if it is especially serious, do contact enforcement authorities as it might be part of a larger criminal enterprise that they should know about. In any severe breach circumstance consider looking for legal assistance on liability issues with creditors. Also consider hiring outside reputation management if necessary.
Business and technology concept. Internet of Things(IoT). Information Communication Network(ICT). … [+]
Some Additional Resources and Compilation of Cybersecurity Trends for 2023:
There is a very good report done by the Bipartisan Policy Research Center on the top eight macro risks to watch out for in 2023. The are stated below from the article and I agree with them all.Please see: Cyber arms race, economic headwinds among top macro cybersecurity risks for 2023 Cyber arms race, economic headwinds among top macro cybersecurity risks for 2023 | CSO Online
And for a deeper dive on cyber stats please see: 34 cybersecurity statistics to lose sleep over in 2023 34 cybersecurity statistics to lose sleep over in 2023 (techtarget.com) The article notes upfront that that we need understand the data and its immense volume used for cyber-attacks. “By 2025, humanity’s collective data will reach 175 zettabytes — the number 175 followed by 21 zeros. This data includes everything from streaming videos and dating apps to healthcare databases. Securing all this data is vital.”
Please also see Dan Lohrman’s annual analysis on cybersecurity trends: “After a year full of data breaches, ransomware attacks and real-world cyber impacts stemming from Russia’s invasion of Ukraine, what’s next? Here’s part 1 of your annual roundup of security industry forecasts for 2023 and beyond.” The Top 23 Security Predictions for 2023 (Part 1) The Top 23 Security Predictions for 2023 (Part 1) (govtech.com) and The Top 23 Security Predictions for 2023 (Part 2) The Top 23 Security Predictions for 2023 (Part 2) (govtech.com)
My Take: Of course, there are many other trends and statistics to explore as the year unfolds. It is certainly a treacherous cyber ecosystem, and it is expanding with risk and threats. Being cyber-aware is part of the process of risk management and security and hopefully looking at the cyber-threat landscape will implore both industry and government to prioritize cybersecurity from the top down and bottom up!
About The Author
Chuck Brooks
Chuck Brooks is a globally recognized thought leader and subject matter expert Cybersecurity and Emerging Technologies. Chuck is also an Adjunct Faculty at Georgetown University’s Graduate Cybersecurity Risk Management Program where he teaches courses on risk management, homeland security technologies, and cybersecurity. LinkedIn named Chuck as one of “The Top 5 Tech People to Follow on LinkedIn.” He was named “Cybersecurity Person of the Year for 2022” by The Cyber Express, and as one of the world’s “10 Best Cyber Security and Technology Experts” by Best Rated, as a “Top 50 Global Influencer in Risk, Compliance,” by Thompson Reuters, “Best of The Word in Security” by CISO Platform, and by IFSEC, and Thinkers 360 as the “#2 Global Cybersecurity Influencer.” He was featured in the 2020, 2021, and 2022 Onalytica “Who’s Who in Cybersecurity” He was also named one of the Top 5 Executives to Follow on Cybersecurity by Executive Mosaic, He is also a Cybersecurity Expert for “The Network” at the Washington Post, Visiting Editor at Homeland Security Today, Expert for Executive Mosaic/GovCon, and a Contributor to Skytop Media, and to FORBES. He has an MA in International relations from the University of Chicago, a BA in Political Science from DePauw University, and a Certificate in International Law from The Hague Academy of International Law.
Chuck Brooks – Cybersecurity Person of The Year -
Sydney Man Sentenced for Blackmailing Optus Customers After … – The Hacker News
A Sydney man has been sentenced to an 18-month Community Correction Order (CCO) and 100 hours of community service for attempting to take advantage of the Optus data breach last year to blackmail its customers.
The unnamed individual, 19 when arrested in October 2022 and now 20, used the leaked records stolen from the security lapse to orchestrate an SMS-based extortion scheme.
The suspect contacted dozens of victims to threaten that their personal information would be sold to other hackers and “used for fraudulent activity” unless an AU$ 2,000 payment is made to a bank account under their control.
The scammer is said to have sent the SMS messages to 92 individuals whose information was part of a larger cache of 10,200 records that was briefly published in a criminal forum in September 2022,
The Australian Federal Police (AFP), which launched Operation Guardian following the breach, said there is no evidence that any of the affected customers transferred the demanded amount.
Following his arrest, the offender pleaded guilty in November 2022 to two counts of using a telecommunications network with intent to commit a serious offense.
“The criminal use of stolen data is a serious offense and has the potential to cause significant harm to the community,” AFP Commander Chris Goldsmid said.
The Australian telecom service provider suffered a massive hack last year, with passport information and Medicare numbers pertaining to nearly 2.1 million of its current and former customers exposed.
Sign up for free and start receiving your daily dose of cybersecurity news, insights and tips. -
20 Million Users Impacted by Data Breach at Instant Checkmate, TruthFinder – SecurityWeek
Hi, what are you looking for?
Instant Checkmate and TruthFinder have disclosed data breaches affecting a total of more than 20 million users.
By
Flipboard
Reddit
Pinterest
Whatsapp
Whatsapp
Email
PeopleConnect-owned background check services Instant Checkmate and TruthFinder have disclosed data breaches affecting a total of more than 20 million users.
In individual data breach notices published on February 3, the organizations informed users that the incident was discovered after cybercriminals started sharing databases stolen from the two companies on underground forums.
The databases – or ‘lists’, as the two companies call them – contain names, email addresses, phone numbers, encrypted passwords, and password reset tokens that are either expired or inactive.
“We have confirmed that the list was created several years ago and appears to include all customer accounts created between 2011 and 2019. The published list originated inside our company,” the announcements read.
The two organizations note that the leaked information does not include details on user activity or payment data.
While Instant Checkmate and TruthFinder also note that no “readable or usable passwords or other means to compromise user accounts” leaked either, it is not uncommon for cybercriminals to try to crack stolen encrypted passwords.
“As a best practice we would recommend that you not respond to suspicious communications. We will never ask you for your password, social security number or payment information via email or telephone,” the companies say.
Investigations were launched into both incidents, but no evidence of malicious activity has been found as of now on their networks. According to the two announcements, the data breach was the result of the “inadvertent leak or theft” of the impacted database.
While neither Instant Checkmate nor TruthFinder shared information on the number of affected individuals, the data has already been added to Troy Hunt’s breach notification service Have I been pwned.
The leaked databases include the information of more than 11.9 million Instant Checkmate accounts, and the details of over 8.1 million TruthFinder accounts.
Related: 820k Impacted by Data Breach at Zacks Investment Research
Related: 18k Nissan Customers Affected by Data Breach at Third-Party Software Developer
Related: 251k Impacted by Data Breach at Insurance Firm Bay Bridge AdministratorsIonut Arghire is an international correspondent for SecurityWeek.
Subscribe to the SecurityWeek Email Briefing to stay informed on the latest threats, trends, and technology, along with insightful columns from industry experts.
Join this webinar to learn best practices that organizations can use to improve both their resilience to new threats and their response times to incidents.
Join this live webinar as we explore the potential security threats that can arise when third parties are granted access to a sensitive data or systems.
 Anna Tutt, CMO of Oort, shares her experiences and perspectives on how we can accelerate growth of women in cybersecurity. (Marc Solomon)
Anna Tutt, CMO of Oort, shares her experiences and perspectives on how we can accelerate growth of women in cybersecurity. (Marc Solomon)
 History has shown that when it comes to ransomware, organizations cannot let their guards down. (Torsten George)
History has shown that when it comes to ransomware, organizations cannot let their guards down. (Torsten George)
 The conventional tools we rely on to defend corporate networks are creating gaps in network visibility and in our capabilities to secure them. (Matt Wilson)
The conventional tools we rely on to defend corporate networks are creating gaps in network visibility and in our capabilities to secure them. (Matt Wilson)
 While there are many routes to application security, bundles that allow security teams to quickly and easily secure applications and affect security posture in a self-service manner are becoming increasingly popular. (Joshua Goldfarb)
While there are many routes to application security, bundles that allow security teams to quickly and easily secure applications and affect security posture in a self-service manner are becoming increasingly popular. (Joshua Goldfarb)
 Varied viewpoints as related security concepts take on similar traits create substantial confusion among security teams trying to evaluate and purchase security technologies. (Marc Solomon)
Varied viewpoints as related security concepts take on similar traits create substantial confusion among security teams trying to evaluate and purchase security technologies. (Marc Solomon)
Flipboard
Reddit
Pinterest
Whatsapp
Whatsapp
Email
Zendesk is informing customers about a data breach that started with an SMS phishing campaign targeting the company’s employees.
The release of OpenAI’s ChatGPT in late 2022 has demonstrated the potential of AI for both good and bad.
No one combatting cybercrime knows everything, but everyone in the battle has some intelligence to contribute to the larger knowledge base.
The changing nature of what we still generally call ransomware will continue through 2023, driven by three primary conditions.
GoTo said an unidentified threat actor stole encrypted backups and an encryption key for a portion of that data during a 2022 breach.
The FBI dismantled the network of the prolific Hive ransomware gang and seized infrastructure in Los Angeles that was used for the operation.
PayPal is alerting roughly 35,000 individuals that their accounts have been targeted in a credential stuffing campaign.
A recently disclosed vBulletin vulnerability, which had a zero-day status for roughly two days last week, was exploited in a hacker attack targeting the…
Got a confidential news tip? We want to hear from you.
Reach a large audience of enterprise cybersecurity professionals
Subscribe to the SecurityWeek Daily Briefing and get the latest content delivered to your inbox.
Copyright © 2023 SecurityWeek ®, a Wired Business Media Publication. All Rights Reserved.