November 9, 2022
If you think your small business is not a target for hackers and cybercriminals — think again. An estimated 50-70% of ransomware attacks target small- and medium-sized businesses[1], likely because adversaries believe smaller organizations do not have robust security measures in place to defend the business and its data.
While cybercriminals rely on a variety of methods to attack a company, one of the most common — and often easiest — is by targeting employees through coordinated phishing attacks or other social engineering techniques.
To minimize this risk, small- and medium-sized businesses need to develop an employee cybersecurity training program that will educate their people about common security risks, promote responsible online behavior and outline steps to take when they believe an attack may be in progress.
Small businesses are often easy prey for cybercriminals on the hunt for sensitive business data and customer information. With CrowdStrike, you get enterprise level-protection and support at a price you can afford – because every SMB deserves protection, regardless of headcount.View cybersecurity solutions for SMBs
Before employee training programs can be developed, your business must have a clear sense of its cybersecurity strategy, as well as the people, processes and technologies that will execute the security program. Here we review the essential elements of the cybersecurity architecture.
A wide variety of solutions and services are available on today’s cybersecurity market. While a trusted and reputable cybersecurity partner can help businesses develop a custom toolset to meet their unique needs, every cybersecurity platform should start at a baseline with antivirus protection.
While cost is a concern for many small business owners, it is important to find solutions that provide the right level of protection at the right budget with the right technology. Learn how to start building a robust cybersecurity plan to meet the specific needs of small businesses.Download: Cybersecurity for Small Businesses: Proactive solutions that meet your need
An incident response plan is a document that outlines an organization’s procedures, steps and responsibilities to prepare for, detect, contain and recover from a data breach.
Even small businesses should develop a clear acceptable use policy for employees who use corporate devices and networks, or have access to data and other sensitive assets. This would include listing the different software applications, programs, websites and social media platforms that are allowed to be accessed with a company device or via a corporate network, as well as the steps that need to be taken to secure and protect the device and its data.
As part of this process, it may also be helpful to outline unacceptable behaviors and prohibited activity.
EXAMPLE: A company’s IT policy should make clear that employees are not allowed to install unlicensed software on any company computer, phone or other device or to download files or programs, such as music, movies, games or other applications. This is because unlicensed software downloads, or any file download, could make the company susceptible to cyberattacks.
Cybersecurity awareness training should be a mandatory task completed by every employee, regardless of level, location or job scope. That said, it may be wise to tailor learning programs based on job type or level of experience, as well as location.
The training program may be adapted for the following audiences:
The training program should cover common and significant cyber threats. These include:
Social engineering is one of the most common methods of cyberattack, where a hacker tricks an employee into sharing sensitive data or credentials by posing as another legitimate employee or partner. For example, a hacker may pose as a help desk agent to ask a user for sensitive information, such as a username and password.
Phishing is a type of social engineering cyberattack that uses email, text message, phone call or social media to entice a victim to share sensitive information — such as passwords or account numbers — or to download a malicious file that will install viruses on their computer or phone.
When creating your training program, include real-life examples of a phishing attack to educate your employees on the main key indicators like you’ll see in the example below: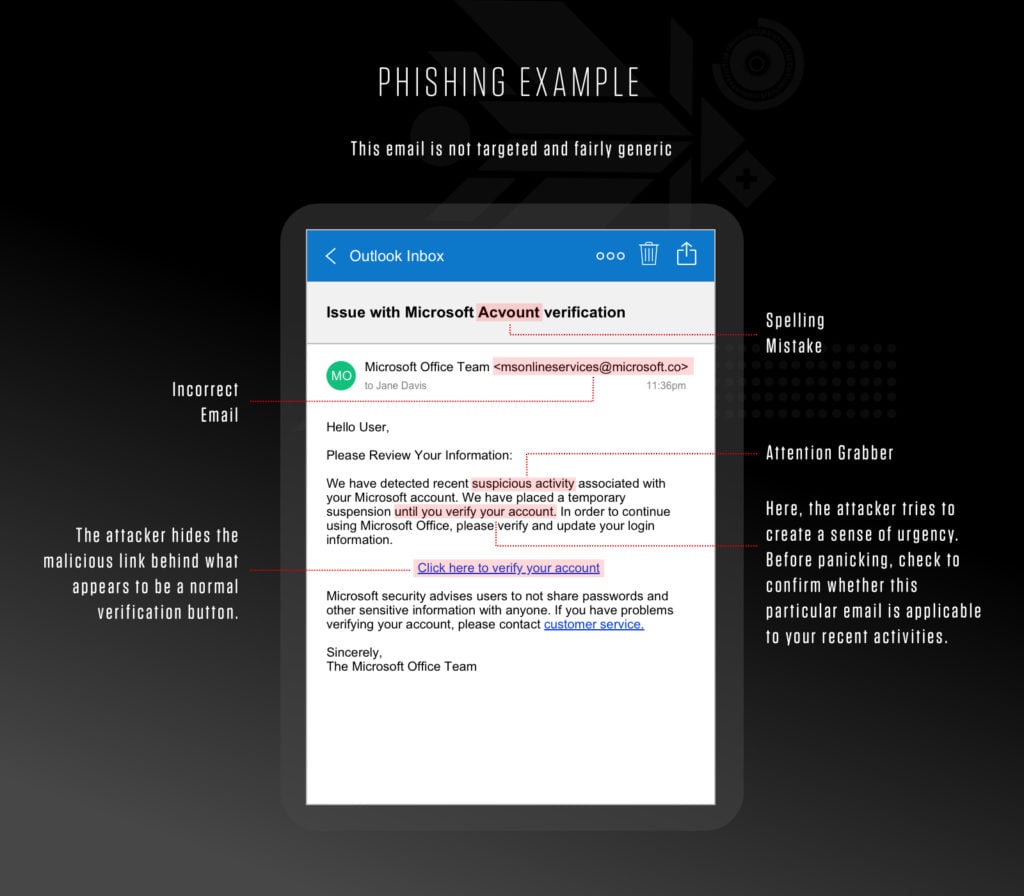
Attackers are constantly after user IDs, email addresses and passwords because these items enable them to pose as a legitimate user to avoid detection while they carry out an attack.
Once the hacker has your credentials they can access any service or network the account is entitled to. One of the best ways to reduce the risk of password compromise is to require users to create strong passwords. Below are examples of strong passwords.
Strong passwords are:
Long, complex, random passwords are exponentially more difficult for password cracking tools to breach. In addition, frequently updated passwords limit the amount of time adversaries have available to crack password hashes.
An insider threat is a cybersecurity risk that comes from within the organization. This is usually a current or former employee or other person who has direct access to the company network, sensitive data and intellectual property.
Typically an insider is financially motivated to lead or take part in a malicious act. These attacks usually involve theft of data or trade secrets which can be sold on the dark web or to a hostile third party. Luckily, there are ways to mitigate insider threats for SMBs, which include continuously monitoring your network and educating employees on all company policies regarding cybersecurity practices.
Every internet-connected device can be the entry point for an attack. Your cybersecurity training program should share best practices for how employees can keep their devices safe, as well as how to install and update the security tools used by the organization.
Social media can be another avenue for cybercriminals to connect with employees, gather personal information and otherwise exploit personal relationships to advance an attack using social engineering techniques. While companies generally cannot prohibit employees from using social media on their own time using their own devices, they can construct clear policies that limit use on company devices or the corporate network.
The main goal of every cybersecurity program is to keep the organization and its assets safe. This includes data of all kinds — including sensitive customer data and intellectual property.
In many cases, employees who handle sensitive customer data, such as personal information, bank details or health records, are required by law to complete cybersecurity training. Organizations that are subject to such regulations should ensure that the training program they develop meets the requirements dictated by government or industry groups.
Cybersecurity must be seen as a company-wide effort. It is important the program has dedicated leadership from IT and HR to ensure training modules are properly developed and rolled out to the appropriate audiences.
As part of this process, the CEO, CFO, IT lead and HR manager should also coordinate on all aspects of program management, including budget. This will help ensure that cybersecurity remains an important part of the company’s ongoing operations and is supported with the proper resources and investments.
As with any new training program, it may be helpful to conduct an initial pilot of the program with a subset of employees and gather feedback about the program content and user experience.
When rolling out the program to your employees, it will be important to track completion rates and test knowledge through both a completion quiz and regular cybersecurity testing, such as a simulated phishing email.
All basic training should be conducted annually in order to refresh employees’ knowledge and keep best practices top-of-mind.
Don’t let the size of your business or your budget stand in the way of developing a strong security defense. CrowdStrike Falcon® Go is an easy-to-manage and affordable solution that prevents ransomware, malware and the latest cyber threats.
Start a free, 15-day trial of Falcon Pro and protect your business from ransomware, malware and sophisticated cyberattacks.
[1] U.S. Secretary of Homeland Security Alejandro Mayorkas in Inc., 2021
Leave a Reply